Tomorrow Bio’s founder and CEO Dr. Emil Kendziorra will give a presentation introducing the topic of cryonics, followed by a Q&A with the audience.
Get the latest international news and world events from around the world.
Möbius Mystery Solved By Mathematician After 5 Decades
Möbius strips are fun geometrical shapes that only have one side. Take a strip of paper – it’s got a front and a back. Now twist it and glue the two short edges together. Suddenly there is no front or back. You could draw a line across its whole surface without having to lift the pencil from the paper. Forty-six years ago mathematicians suggested the minimum size for such a strip but they couldn’t prove it. Now, someone finally has.
Since the creation of the strip by August Ferdinand Möbius and Johann Benedict Listing, its simplicity in making and visualizing it had to be balanced with the mathematical complexity of such a shape. It is not surprising that in 1977, Charles Sidney Weaver and Benjamin Rigler Halpern created the Halpern-Weaver Conjecture, which stated the minimal ratio between the width of the strip and its length. They suggested that for a strip with a width of 1 centimeter (0.39 inches), the length had to be at least the square root of 3 centimeters (about 1.73 centimeters or 0.68 inches).
For smooth Möbius strips that are “embedded”, meaning they don’t intersect with each other, the conjecture had no solution. If the strip can go through itself, it is a much easier problem to solve, Brown University’s mathematician Richard Evan Schwartz proposed in 2020 – but he had made a mistake. In a paper posted as a preprint – meaning it is yet to be subjected to peer review – Schwartz corrected the error and found the right solution for the conjecture.
Decoding Complexity: MIT’s Insight Into Individual Neurons and Behavior
Study finds that in worms, the HSN neuron uses multiple chemicals and connections to orchestrate egg-laying and locomotion over the course of several minutes.
A new MIT
MIT is an acronym for the Massachusetts Institute of Technology. It is a prestigious private research university in Cambridge, Massachusetts that was founded in 1861. It is organized into five Schools: architecture and planning; engineering; humanities, arts, and social sciences; management; and science. MIT’s impact includes many scientific breakthroughs and technological advances. Their stated goal is to make a better world through education, research, and innovation.
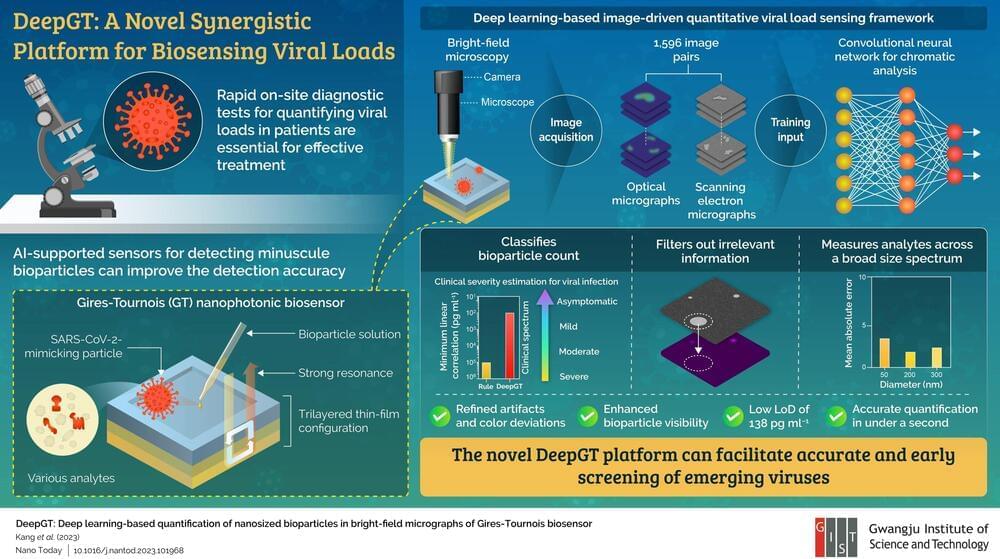
Scientists develop deep learning-based biosensing platform to better count viral particles
Recent studies have found that Gires-Tournois (GT) biosensors, a type of nanophotonic resonator, can detect minuscule virus particles and produce colorful micrographs (images taken through a microscope) of viral loads. But they suffer from visual artifacts and non-reproducibility, limiting their utilization.
In a recent breakthrough, an international team of researchers, led by Professor Young Min Song from the School of Electrical Engineering and Computer Science at Gwangju Institute of Science and Technology in Korea, has leveraged artificial intelligence (AI) to overcome this problem. Their work was published in Nano Today.
Rapid and on-site diagnostic technologies for identifying and quantifying viruses are essential for planning treatment strategies for infected patients and preventing further spread of the infection. The COVID-19 pandemic has highlighted the need for accurate yet decentralized diagnostic tests that do not involve complex and time-consuming processes needed for conventional laboratory-based tests.


350-Year-Old Theorem Reveals New Properties of Light
Ever since the 17th-century debates between Isaac Newton and Christiaan Huygens about the essence of light, the scientific community has grappled with the question: Is light a wave or a particle — or perhaps, at the quantum level, even both at once? Now, researchers at the Stevens Institute of Technology have revealed a new connection between the two perspectives, using a 350-year-old mechanical theorem — ordinarily used to describe the movement of large, physical objects like pendulums and planets — to explain some of the most complex behaviors of light waves.
The work, led by Xiaofeng Qian, assistant professor of physics at Stevens and reported in the August 17 online issue of Physical Review Research, also proves for the first time that a light wave’s degree of non-quantum entanglement exists in a direct and complementary relationship with its degree of polarization. As one rises, the other falls, enabling the level of entanglement to be inferred directly from the level of polarization, and vice versa. This means that hard-to-measure optical properties such as amplitudes, phases, and correlations – perhaps even those of quantum wave systems – can be deduced from something a lot easier to measure: light intensity.

Researchers use measurements to generate quantum entanglement and teleportation
Quantum mechanics is full of weird phenomena, but perhaps none as weird as the role measurement plays in the theory. Since a measurement tends to destroy the “quantumness” of a system, it seems to be the mysterious link between the quantum and classical world. And in a large system of quantum bits of information, known as “qubits,” the effect of measurements can induce dramatically new behavior, even driving the emergence of entirely new phases of quantum information.
This happens when two competing effects come to a head: interactions and measurement. In a quantum system, when the qubits interact with one another, their information becomes shared nonlocally in an “entangled state.” But if you measure the system, the entanglement is destroyed. The battle between measurement and interactions leads to two distinct phases: one where interactions dominate and entanglement is widespread, and one where measurements dominate, and entanglement is suppressed.
As reported in the journal Nature, researchers at Google Quantum AI and Stanford University have observed the crossover between these two regimes—known as a “measurement-induced phase transition”—in a system of up to 70 qubits. This is by far the largest system in which measurement-induced effects have been explored.

From a five-layer graphene sandwich, a rare electronic state emerges
Despite its waif-like proportions, scientists have found over the years that graphene is exceptionally strong. And when the material is stacked and twisted in specific contortions, it can take on surprising electronic behavior.
Now, MIT physicists have discovered another surprising property in graphene: When stacked in five layers, in a rhombohedral pattern, graphene takes on a very rare, “multiferroic” state, in which the material exhibits both unconventional magnetism and an exotic type of electronic behavior, which the team has coined ferro-valleytricity.