Study uses AI and blood samples from 50,000 to predict dementia 15 years in advance, offering hope for early intervention.


EpiSci has won a $1.6 million contract with the US Space Development Agency to flesh out its AI-powered, hypersonic missile tracking system.
The SDA and EpiSci have partnered to create AI software that detects hypersonic missiles using satellite technology, AI, and advanced analytics.

The new model is called Big Adaptive Streamable TTS with Emergent abilities — BASE TTS.
In what is being called the largest text-to-speech model ever developed, researchers at Amazon AGI have made waves after creating the Big Adaptive Streamable TTS with Emergent abilities (BASE TTS).
Text-to-Speech (TTS) models are used in the development of voice assistants for smart devices and are employed to convert written text into spoken words, allowing voice assistants to communicate with users in a natural and human-like manner.
Furthermore, TTS models produce outputs that closely resemble natural speech, incorporating elements such as intonation, emphasis, and inflection.
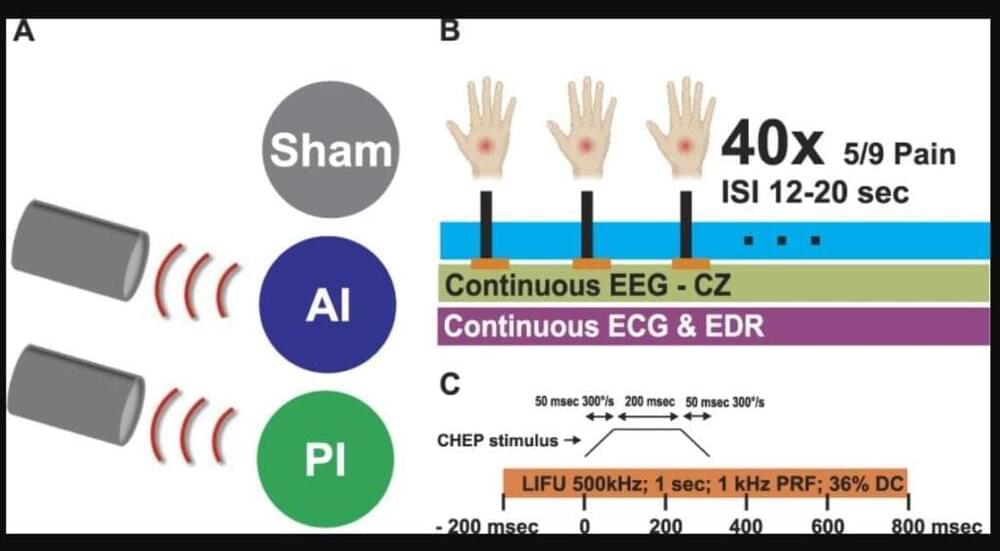
Research reveals potential of using low-intensity focused ultrasound for pain management. Scientists have found soundwaves from low-intensity focused ultrasound aimed at a place deep in the brain called the insula can reduce both the perception of pain and other effects of pain, such as heart rate changes.
You feel a pain, so you pop a couple of ibuprofen or acetaminophen. If the pain is severe or chronic, you might be prescribed something stronger — an opioid pain killer that can be addictive under some circumstances.
But what if you could ease pain by non-invasively manipulating a spot inside your brain where pain is registered?
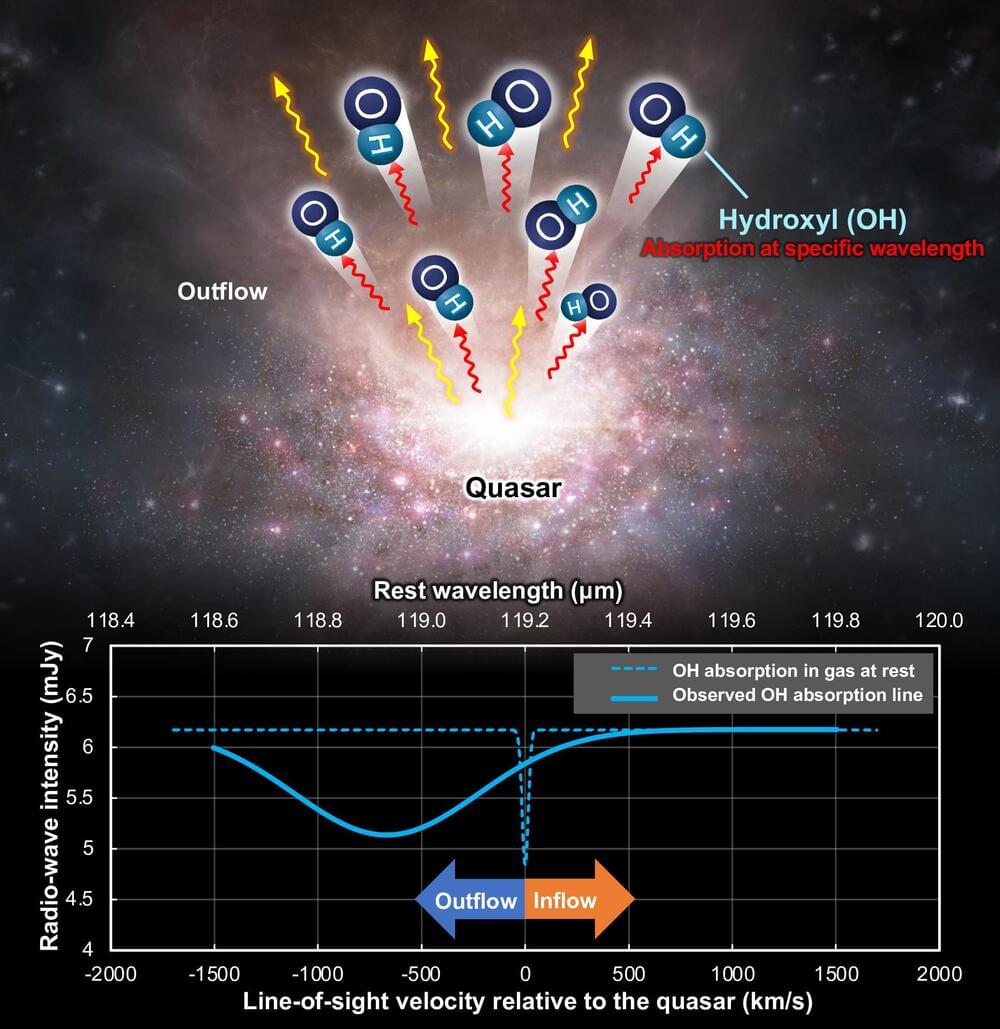
Theoretical predictions have been confirmed with the discovery of an outflow of molecular gas from a quasar when the Universe was less than a billion years old.
A quasar is a compact region powered by a supermassive black hole located in the center of a massive galaxy.
They are extremely luminous, with a point-like appearance similar to stars, and are extremely distant from Earth.
A team of researchers in Spain has achieved a breakthrough by capturing the world’s first detailed images of a human cell’s ‘highway network’ beginning to emerge.
The high-resolution images and atomic-scale film help explain a longstanding puzzle of how small structures called microtubules form during cell division. The discovery could progress the development of targeted treatments for cancer, and many other conditions.
“Microtubules are critical components of cells, but all the images we see in textbooks describing the first moments of their creation are models or cartoons based on structures in yeast,” says biochemist Thomas Surrey from the Centre for Genomic Regulation in Barcelona.
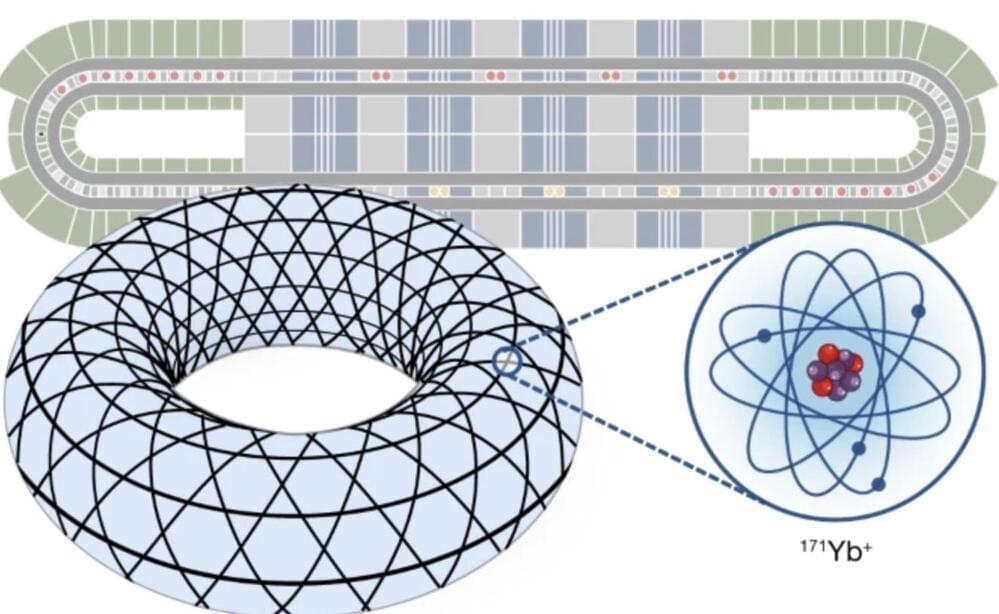
Last year, a Quantinuum-led team of scientists announced that they were able to realize and control a state of matter known as non-Abelian topological order within a quantum processor. The team published their results in the pre-print server ArXiv, outlining how they accomplished what many experts considered a far-off advance — if possible at all – and what the scientists hoped could be an advance toward revolutionizing the way we approach quantum computing.
That advance has now been officially peer reviewed in Nature, marking another important step in the scientific process – and maybe even a significant step in the quest for fault-tolerant quantum computers, a quantum device that could handle operations with unprecedented accuracy and efficiency.
“Our key finding is that non-Abelian topological orders can experimentally be prepared with high fidelities on par with Abelian states like the surface code,” the team writes. “Non-Abelian states are among the most intricately entangled quantum states theoretically known to exist, and carry promise for new types of quantum information processing. Their realization evidences the rapid development of quantum devices and opens several new questions.”

For patients with acute ischemic stroke and large cores, endovascular thrombectomy (EVT) improves clinical outcomes compared with medical management (MM), according to a study published online Feb. 7 in the Journal of the American Medical Association to coincide with the annual American Stroke Association International Stroke Conference, which was held from Feb. 7 to 9 in Phoenix.
Amrou Sarraj, M.D., from Case Western Reserve University in Cleveland, and colleagues describe the relationship between imaging estimates of irreversibly injured brain and at-risk regions and clinical outcomes and EVT treatment effect in an exploratory analysis of the SELECT2 trial.
Adults with acute ischemic stroke due to occlusion of the internal carotid or middle cerebral artery (M1 segment) and large ischemic core were randomly allocated to EVT versus MM across 31 global centers; the analysis included 336 patients.