Researchers at National Taiwan University have developed a new type of spintronic device that mimics how synapses work in the brain—offering a path to more energy-efficient and accurate artificial intelligence systems.
In a study published in Advanced Science, the team introduced three novel memory device designs, all controlled purely by electric current and without any need for an external magnetic field.
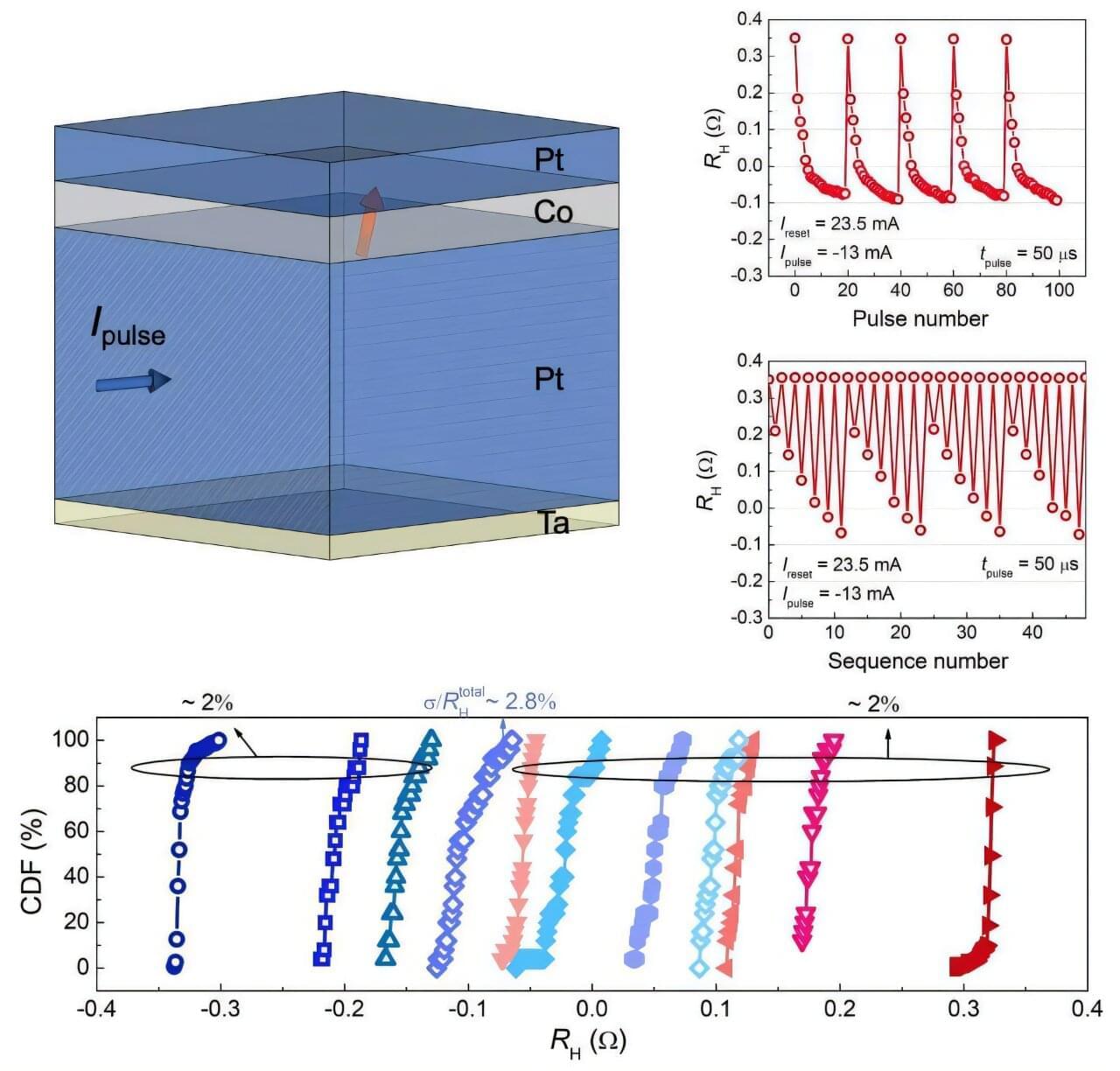
Among the devices, the one based on “tilted anisotropy” stood out. This optimized structure was able to achieve 11 stable memory states with highly consistent switching behavior.