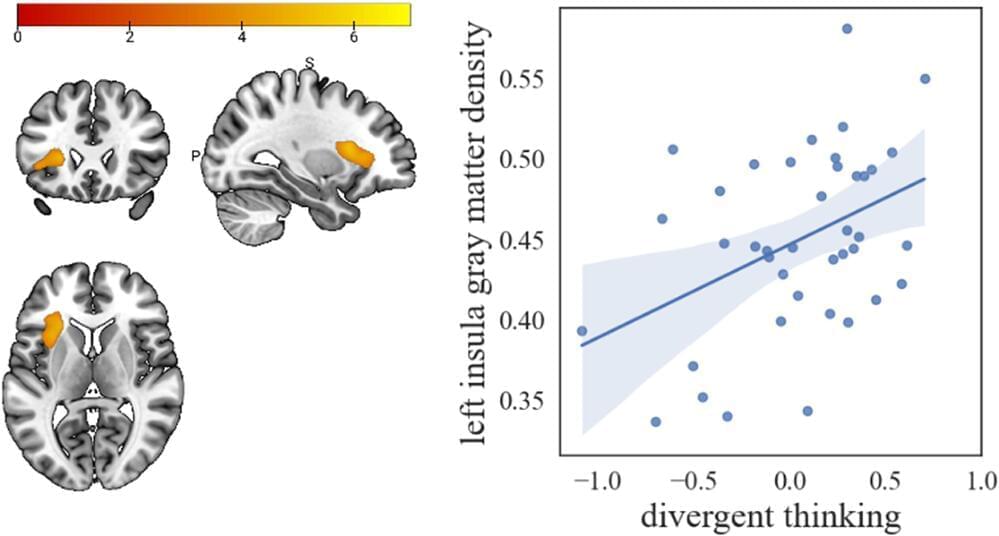
These technologies are helping researchers to explore what sets the human brain apart from those of other species, and how its cognitive abilities have evolved. For example, the role of non-invasive imaging in learning about cognitive abilities is discussed in a Perspective article by Feline Lindhout at the Medical Research Council’s Laboratory of Molecular Biology in Cambridge, UK, and her colleagues1. In another article, Evelina Fedorenko at the Massachusetts Institute of Technology in Cambridge and her colleagues also draw on this literature to argue that, in humans, language probably serves mainly as a communication tool rather than as a means for thinking or reasoning2 — and that language is not a prerequisite for complex thought.
One desirable outcome for human neuroscience would be to develop personalized treatments for neurological and psychiatric disorders, because translating the results of studies in animals has not proved successful or sufficient for generating effective therapies at scale. But in grasping these opportunities, researchers must keep in mind that the brain is different from other organs — it’s the seat of people’s memory, experiences and personality. When using the human brain — whether in small cubes removed during neurosurgery, or through 3D organoids made from stem cells and grown in cultures to resemble parts of the developing human brain — for research, scientists must consider the dignity and respect owed to the individuals concerned.