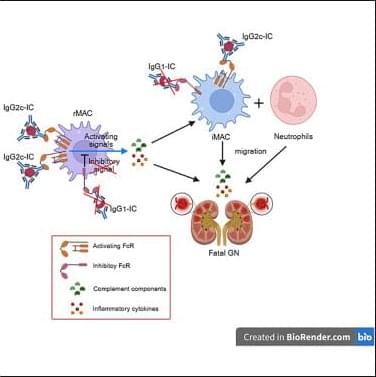
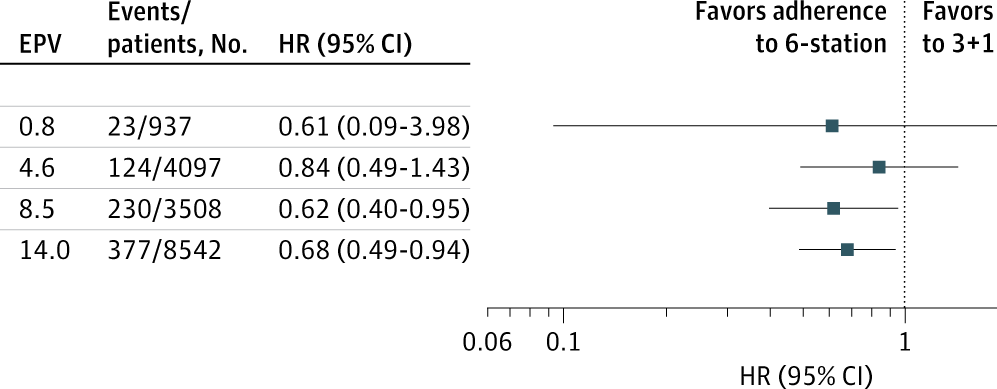
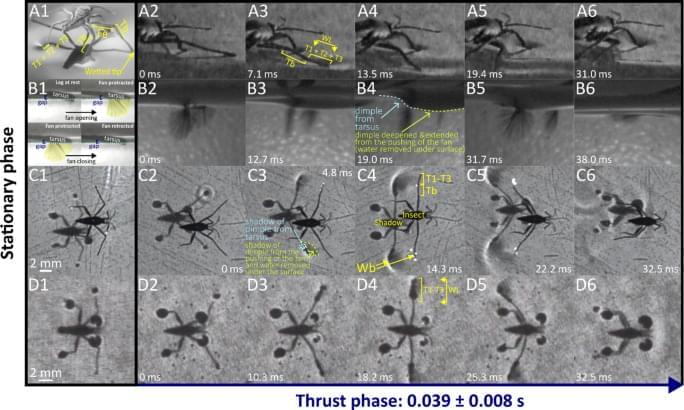
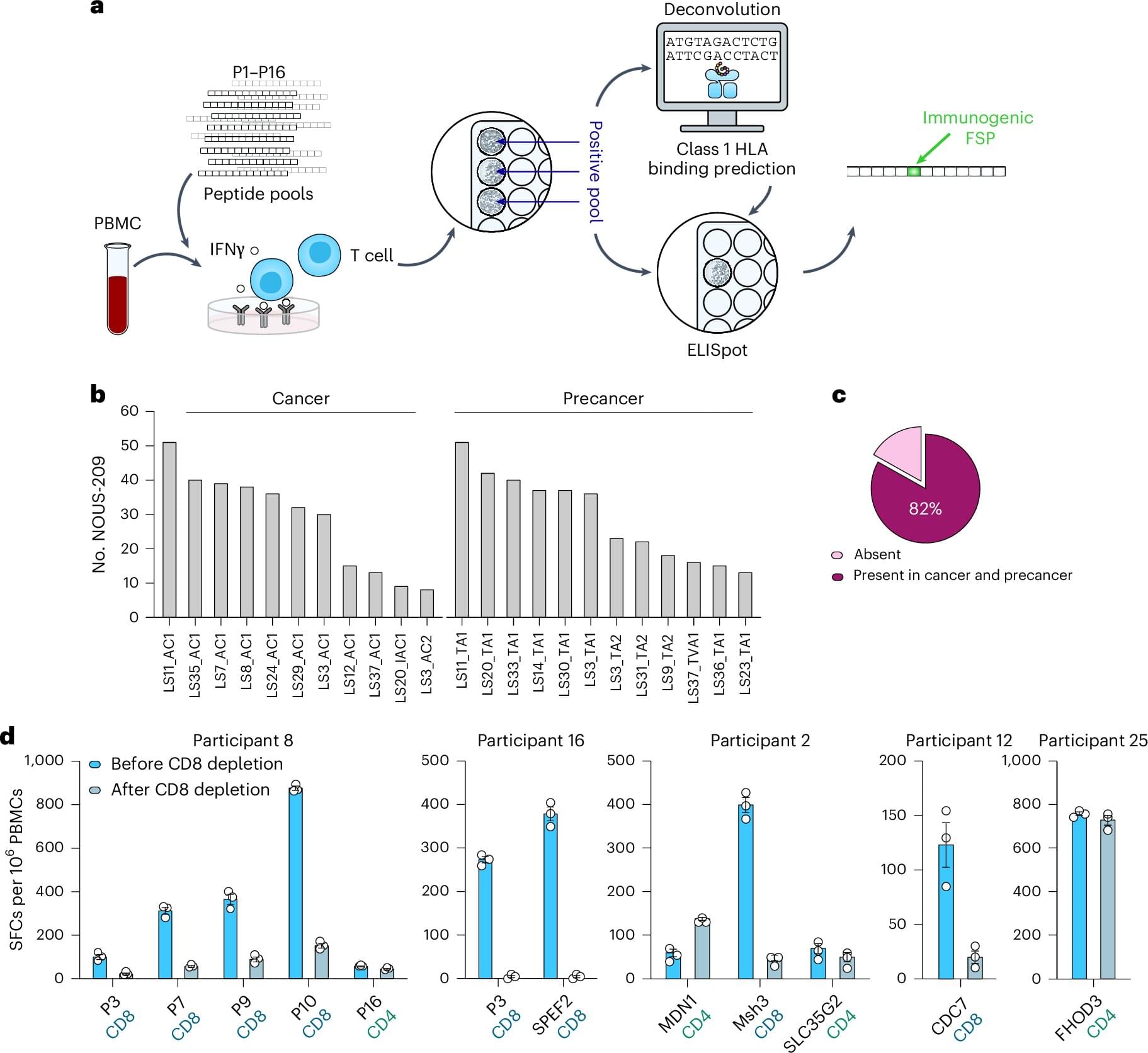
A landmark international study that pooled brain scans and memory tests from thousands of adults has shed new light on how structural brain changes are tied to memory decline as people age.
The findings — based on more than 10,000 MRI scans and over 13,000 memory assessments from 3,700 cognitively healthy adults across 13 studies — show that the connection between shrinking brain tissue and declining memory is nonlinear, stronger in older adults, and not solely driven by known Alzheimer’s-associated genes like APOE ε4. This suggests that brain aging is more complex than previously thought, and that memory vulnerability reflects broad structural changes across multiple regions, not just isolated pathology.
Published in Nature Communications, the study, “Vulnerability to memory decline in aging revealed by a mega-analysis of structural brain change,” found that structural brain change associated with memory decline is widespread, rather than confined to a single region. While the hippocampus showed the strongest association between volume loss and declining memory performance, many other cortical and subcortical regions also demonstrated significant relationships. This suggests that cognitive decline in aging reflects a distributed macrostructural brain vulnerability, rather than deterioration in a few specific brain regions. The pattern across regions formed a gradient, with the hippocampus at the high end and progressively smaller but still meaningful effects across large portions of the brain.
https://www.nature.com/articles/s41467-025-66354-y
Genetic risk for Alzheimer’s and widespread brain shrinkage linked to greater memory loss — even in otherwise healthy adults.