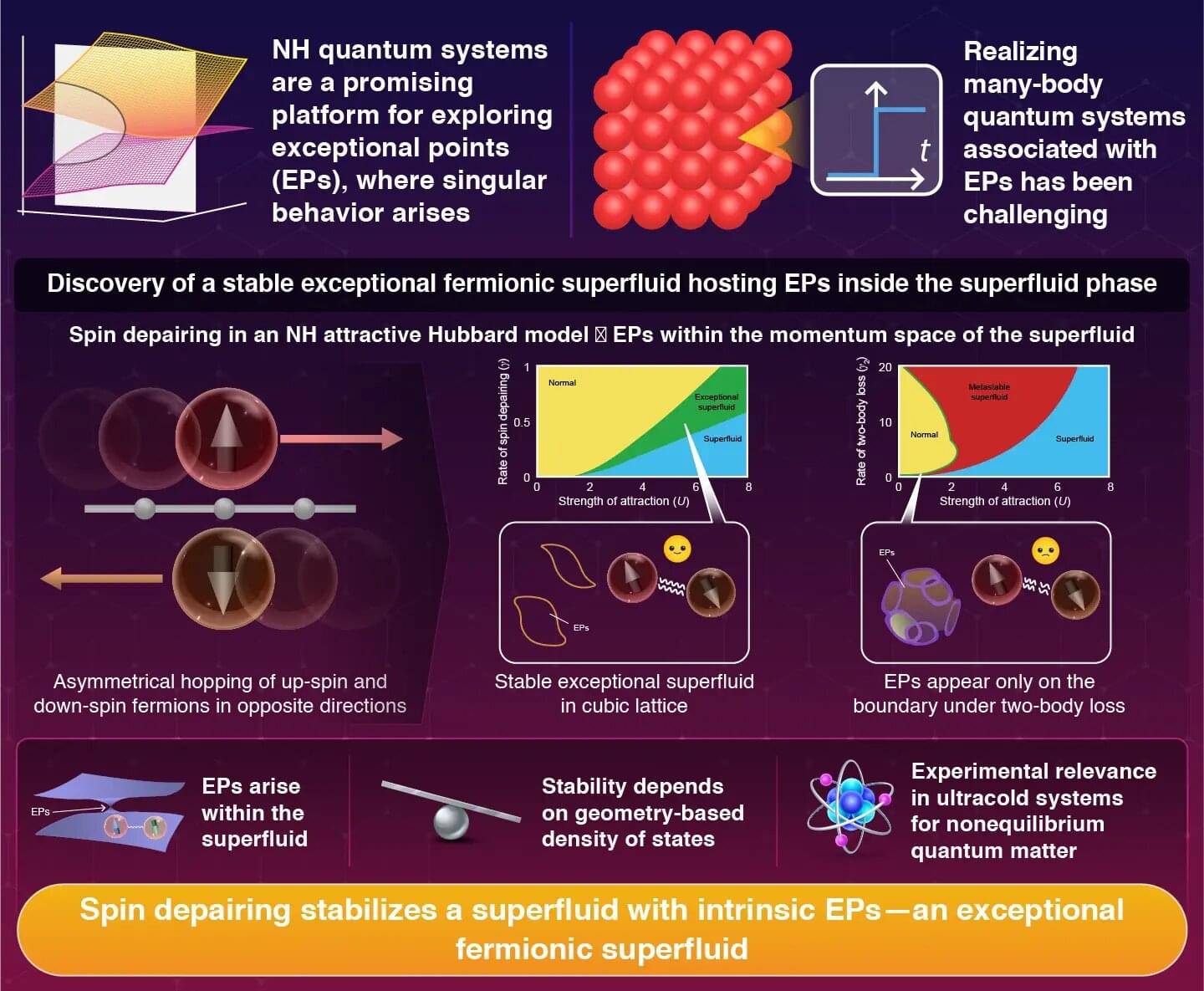
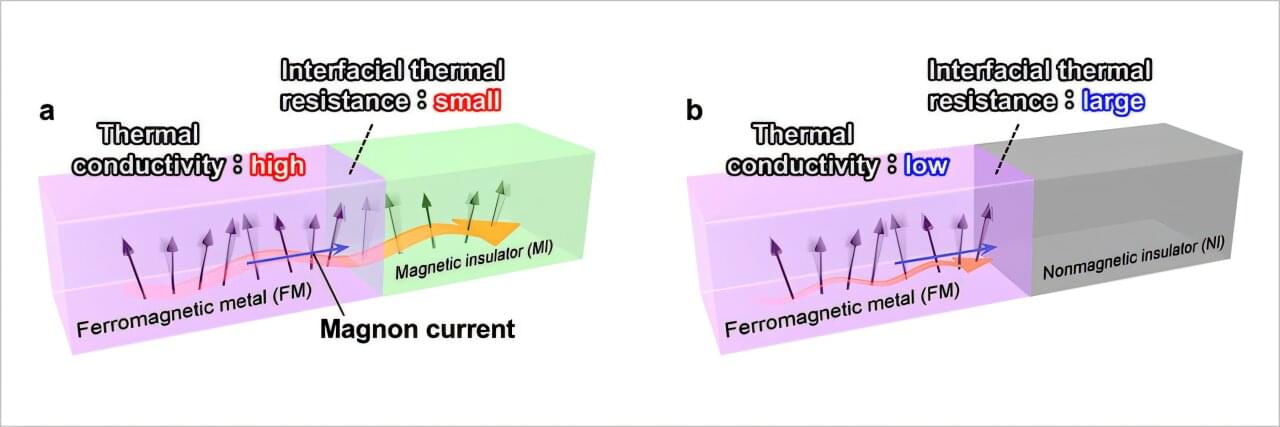
A stable “exceptional fermionic superfluid,” a new quantum phase that intrinsically hosts singularities known as exceptional points, has been discovered by researchers at the Institute of Science Tokyo.
Their analysis of a non-Hermitian quantum model with spin depairing shows that dissipation can actively stabilize a superfluid with these singularities embedded within it. The work reveals how lattice geometry dictates the phase’s stability and provides a path to realizing it in experiments with ultracold atoms.
In the quantum world, open quantum systems are those where particle loss and directional asymmetry are fundamental features. These systems can no longer be described by conventional mathematics.