See a close-up of the above image!
UK aging research foundation produces roadmap for the emerging longevity industry in a series of reports to be published throughout the year
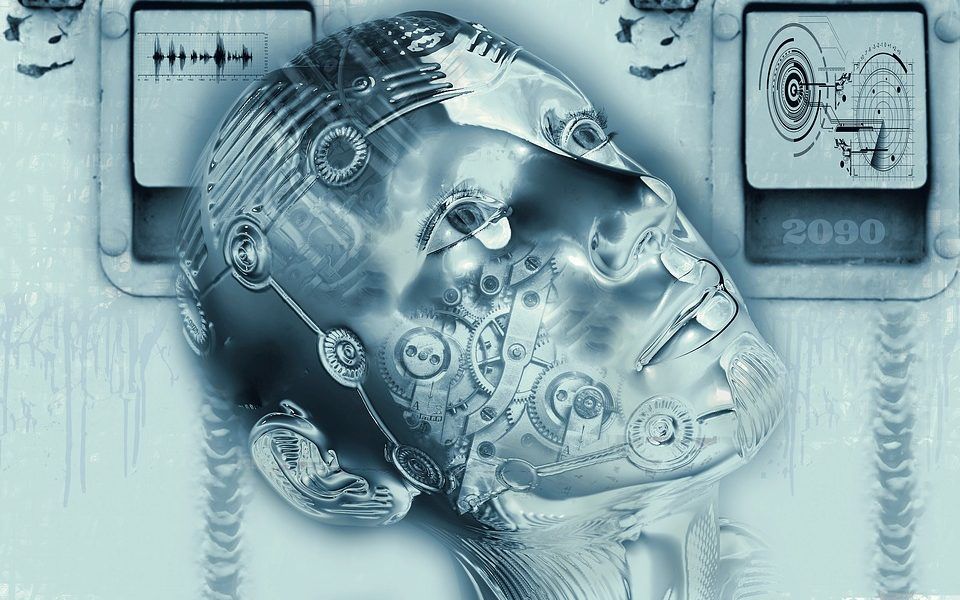
Friday, Feb. 2, 2017, London, UK: The Biogerontology Research Foundation has embarked on a year-long mission to summarise in a single document the various emerging technologies and industries which can be brought to bear on aging, healthy longevity, and everything in between, as part of a joint project between The Global Longevity Consortium, consisting of the Biogerontology Research Foundation, Deep Knowledge Life Sciences, Aging Analytics Agency and Longevity. International platform.
For scientists, policy makers, regulators, government officials, investors and other stakeholders, a consensus understanding of the field of human longevity remains fragmented, and has yet to be systematized by any coherent framework, and has not yet been the subject of a comprehensive report profiling the field and industry as a whole by any analytical agency to date. The consortium behind this series of reports hope that they will come to be used as a sort of Encyclopedia Britannica and specialized Wikipedia of the emerging longevity industry, with the aim of serving as the foundation upon which the first global framework of the industry will be built, given the significant industry growth projected over the coming years.