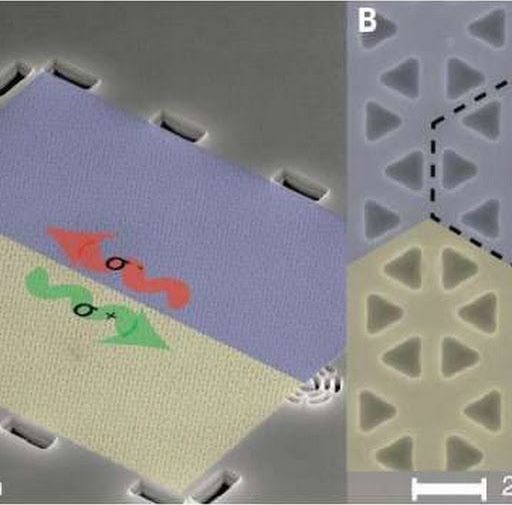
Fabricated device and band structure. (A) Scanning electron microscope image of the device, which is composed of two regions identified by blue and yellow shading, corresponding to two photonic crystals with different topological properties. The interface between the two photonic crystals supports helical edge states with opposite circular polarization (s+ and s–). Grating couplers at each end of the device scatter light in the out-of-plane direction for collection. (B) Close-up image of the interface. Black dashed lines identify a single unit cell of each photonic crystal. Credit: Science…