New research from Caltech’s Center for Autonomous Systems and Technologies finds robots that morph before landing are more robust
Get the latest international news and world events from around the world.



Quantum Enabled Radar
Advances in Quantum technologies offer a step improvement in phase noise performance compared to conventional oscillators. University of Birmingham (UoB) is developing a new class of ultra low phase noise optical lattice clock Quantum oscillator that can provide several orders of magnitude improvement in radar sensitivity against clutter.
To facilitate this enabling research, the Advanced Radar Network (ADRAN) facility funded by the EPSRC Quantum Technologies Hub is being set-up to enable comparative performance assessment of a radar systems with quantum oscillators as compared to conventional alternatives.
This may be shared as something else, but these guys just used quantum tech to “unstealth stealth”. I think that’s a pretty cool thing to accomplish.
Information about quantum enabled radar research in the Microwave Integrated Systems Laboratory (MISL) at the University of Birmingham.

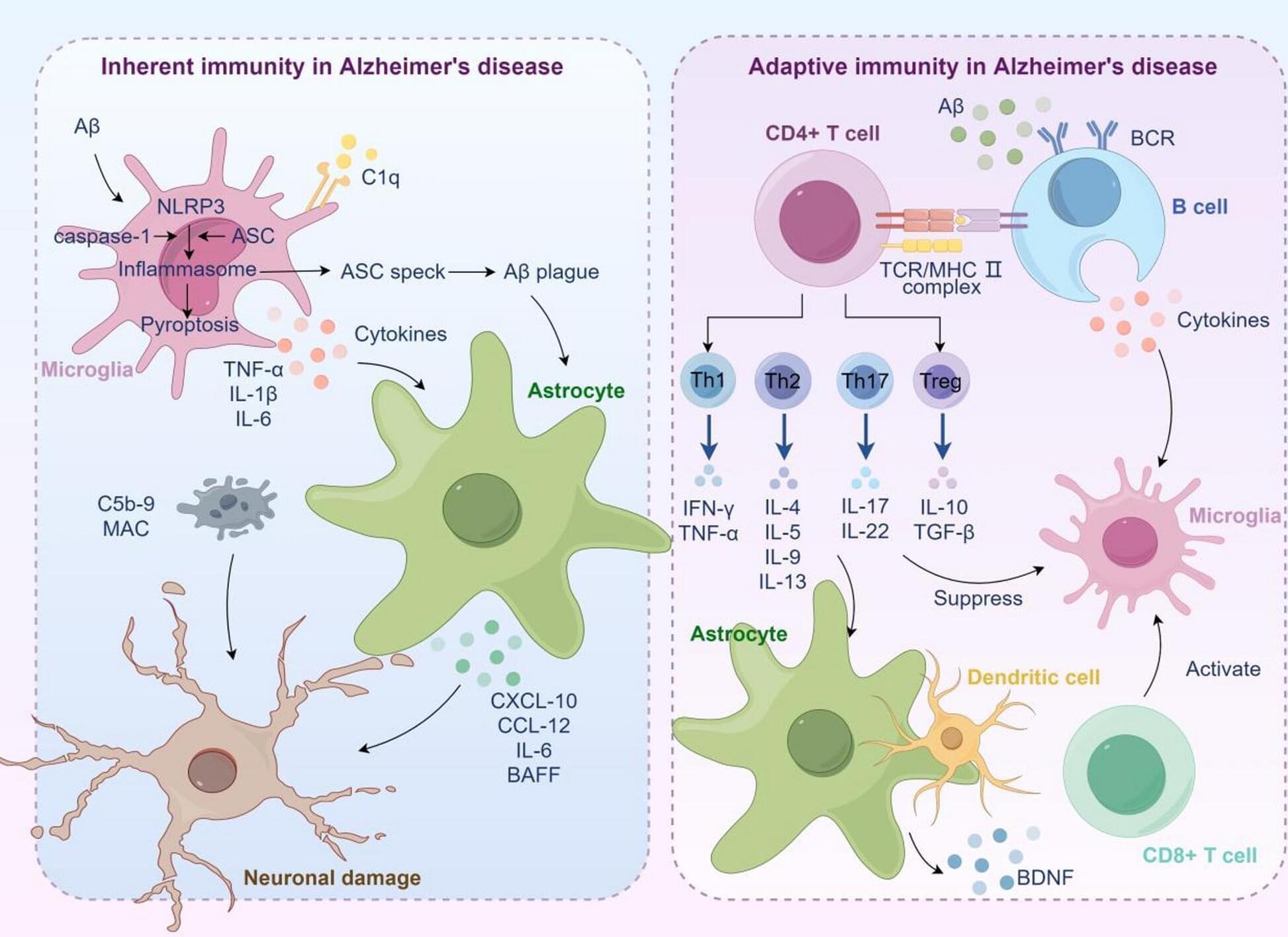
Alzheimer’s disease pathogenesis: standing at the crossroad of lipid metabolism and immune response
Alzheimer’s disease (AD) is a neurodegenerative disorder characterized by macroscopic features such as cortical atrophy, narrowing of the gyri, widening of the sulci, and enlargement of the ventricles. At the cellular level, the pathological characteristics include the extracellular aggregation of β-amyloid (Aβ) forming senile plaques, and the intracellular accumulation of hyperphosphorylated tau proteins forming neurofibrillary tangles. AD leads to the progressive decline of cognitive, behavioral, and social abilities, with no effective treatment available currently. The pathophysiology of AD is complex, involving mechanisms such as immune dysregulation and lipid metabolism alterations. Immune cells, such as microglia, can identify and clear pathological aggregates like Aβ early in the disease.

Renowned Mars expert says Trump-Musk axis risks dooming mission
Robert Zubrin quite literally wrote the book on why humanity should go to Mars—so why has the renowned aerospace engineer soured on Elon Musk, the billionaire entrepreneur leading the charge?
In an interview, the 73-year-old founder of the Mars Society delivered a blistering critique, accusing the world’s richest person of undermining the mission through divisive politics and a bleak vision of the Red Planet as an escape from Earth rather than a journey of hope.
“On one level, he’s absolutely instrumental in opening up this opportunity to get humans to Mars, both through the development of Starship and also the inspiration that has caused,” Zubrin told AFP, referring to Musk’s prototype rocket.
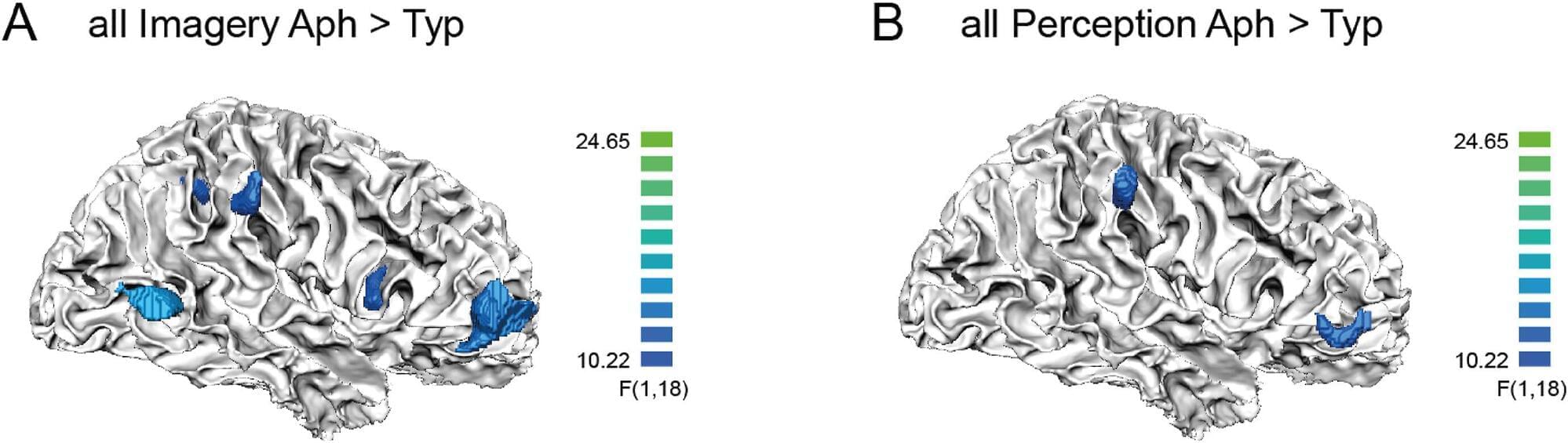
Aphantasia might be linked to alterations in brain connectivity
Thanks to 7T fMRI, researchers from Paris Brain Institute and NeuroSpin, the CEA’s neuroimaging center, are exploring the neural substrate of visual imagery at very high resolution for the first time. Their results, published in Cortex, pave the way for a better understanding of this fascinating cognitive ability, which some of us entirely lack.
Visual imagery—the ability to mentally summon the image of a landscape, a person, or an object that is not directly observable—varies greatly in intensity from one individual to another. Some people can recall a detailed city map and walk through each street as if watching a movie. Thinking of a loved one, others may barely make out their silhouette and hair color.
Interestingly, about 4% of the population seems completely unable to visualize a scene on demand: this is known as aphantasia, a cognitive peculiarity known for over a century but only recently studied by scientists.

A more realistic look at DNA in action
The background
Most biochemistry labs that study DNA isolate it within a water-based solution that allows scientists to manipulate DNA without interacting with other molecules. They also tend to use heat to separate strands, heating the DNA to over 150 degrees Fahrenheit, a temperature a cell would never naturally reach. By contrast, in a living cell DNA lives in a very crowded environment, and special proteins attach to DNA to mechanically unwind the double helix and then pry it apart.
