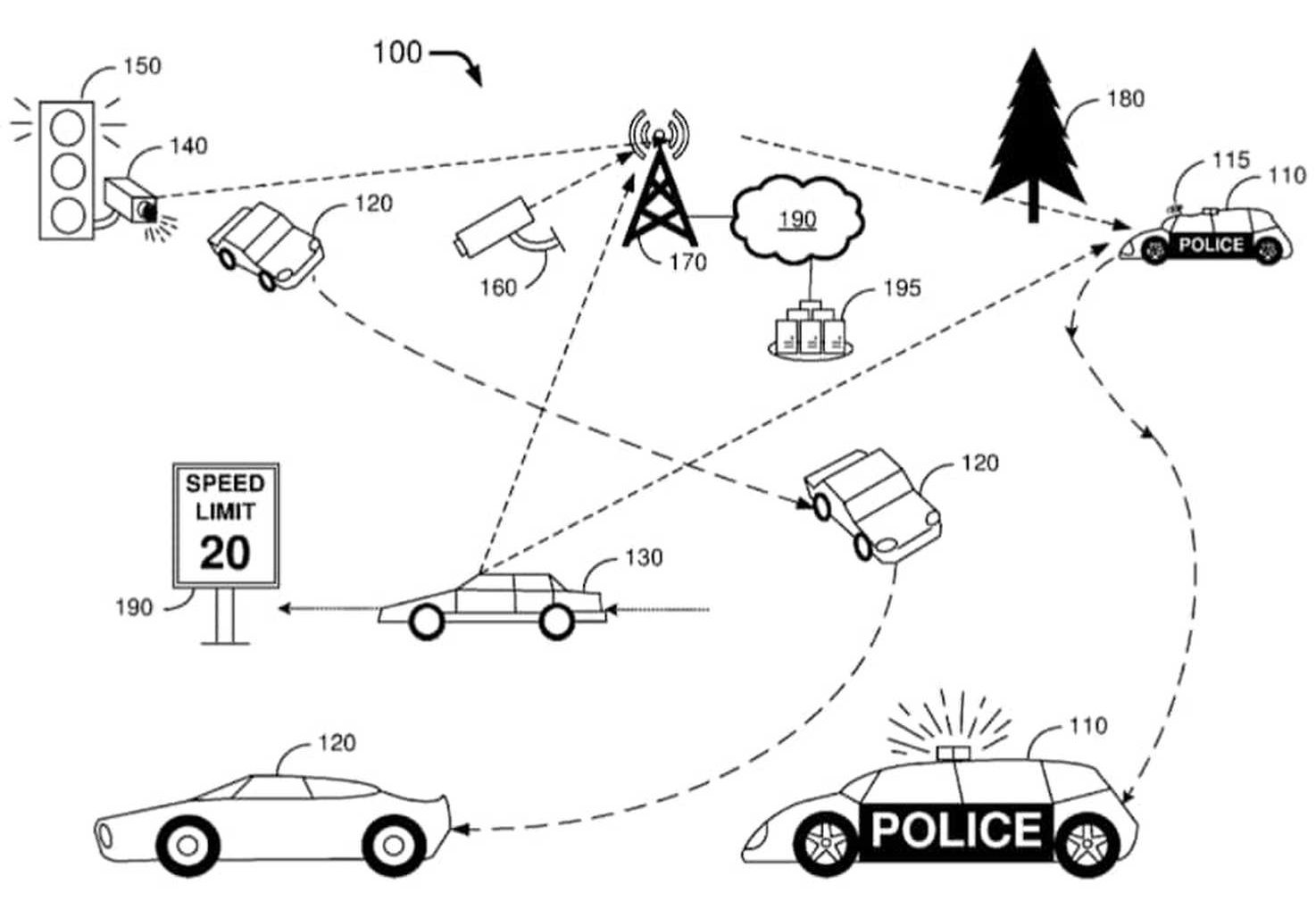
A security company wants to modernize the “backward-looking” and “inherently inefficient” video surveillance industry by offering a blockchain-based system which allows users to react to threats in real time.
Faceter’s decentralized surveillance technology – which it claims is a world first for consumers – “gives brains to cameras” by enabling them to instantly detect faces, objects and analyze video feeds. Although some B2B providers do offer similar features, the company claims they are currently too expensive for smaller firms and the public at large because of the “substantial computing resources” such technology needs.
According to Faceter’s white paper, Blockchain has the potential to make this solution affordable for everyone – as computing power for recognition calculations would be generated by a network of miners.