Q-Dot demand in Healthcare is predicted to be high.
http://embedded-computing.com/news/rising-quantum-dots-market/#
Quantum Dots Market is driven by increasing demand for energy efficient displays and lighting solutions, North America accounted for largest quantum dots market share, use of quantum dots in solar cells and VLSI design is expected to open new possibilities for quantum dots market.
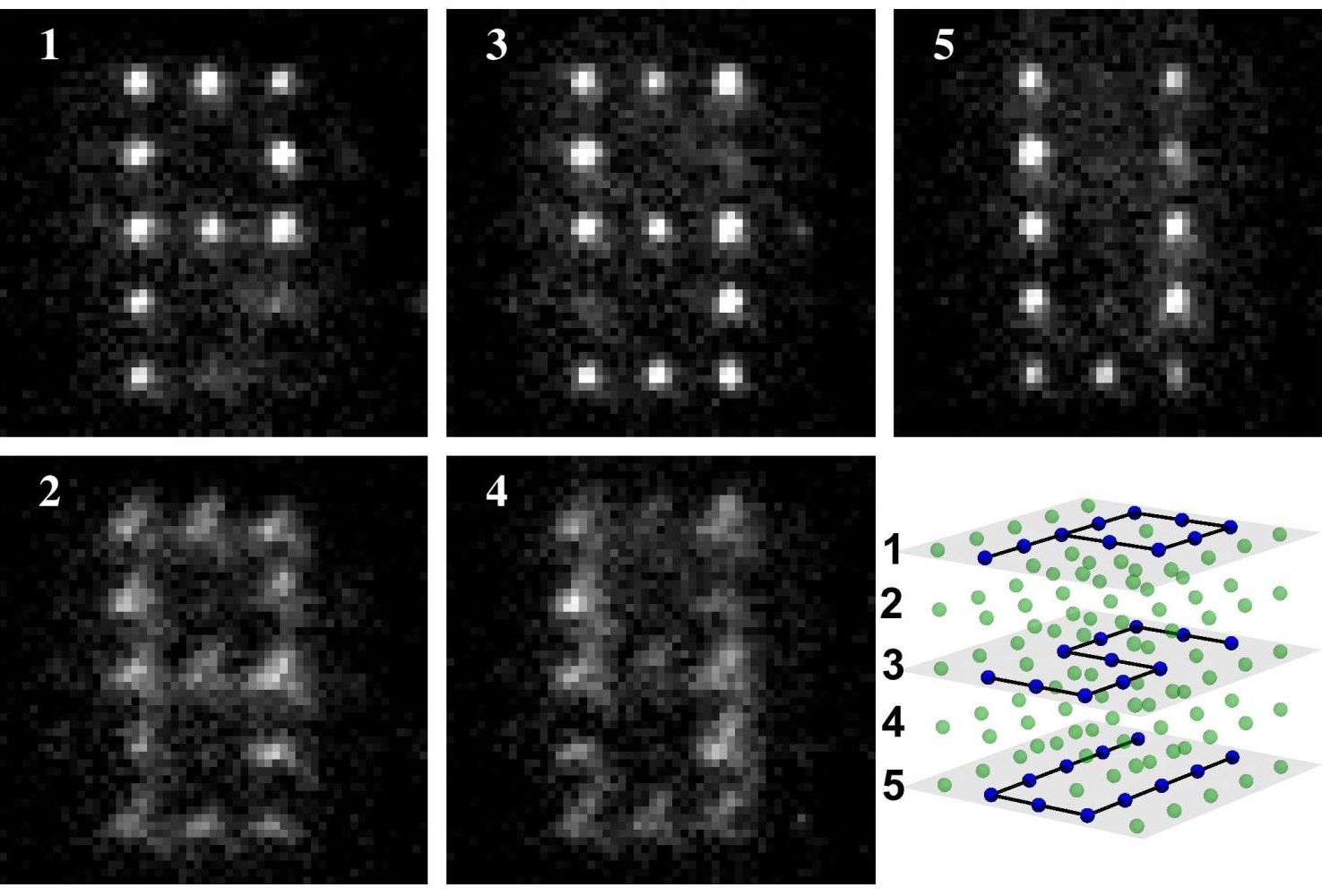
Quantum dots are semiconducting nanoparticles that range from 1nm to 10nm diameter in size and demonstrate quantum mechanical properties. The peculiarity of quantum dots is that they have ability to unite their semiconductor properties with those of nanomaterials. In addition, tunable nanocrystal size and superior optical properties have made quantum dots attractive semiconducting material for variety of applications in the field of healthcare, optoelectronics, solar energy, and security among others.



 © iStock/ Getty Images undefined How much storage do you have around the house? A few terabyte hard drives? What about USB sticks and old SATA drives? Humanity uses a staggering amount of storage, and our needs are only expanding as we build data centers, better cameras, and all sorts of other data-heavy gizmos. It’s a problem scientists from companies like IBM, Intel, and Microsoft are trying to solve, and the solution might be in our DNA.
© iStock/ Getty Images undefined How much storage do you have around the house? A few terabyte hard drives? What about USB sticks and old SATA drives? Humanity uses a staggering amount of storage, and our needs are only expanding as we build data centers, better cameras, and all sorts of other data-heavy gizmos. It’s a problem scientists from companies like IBM, Intel, and Microsoft are trying to solve, and the solution might be in our DNA.