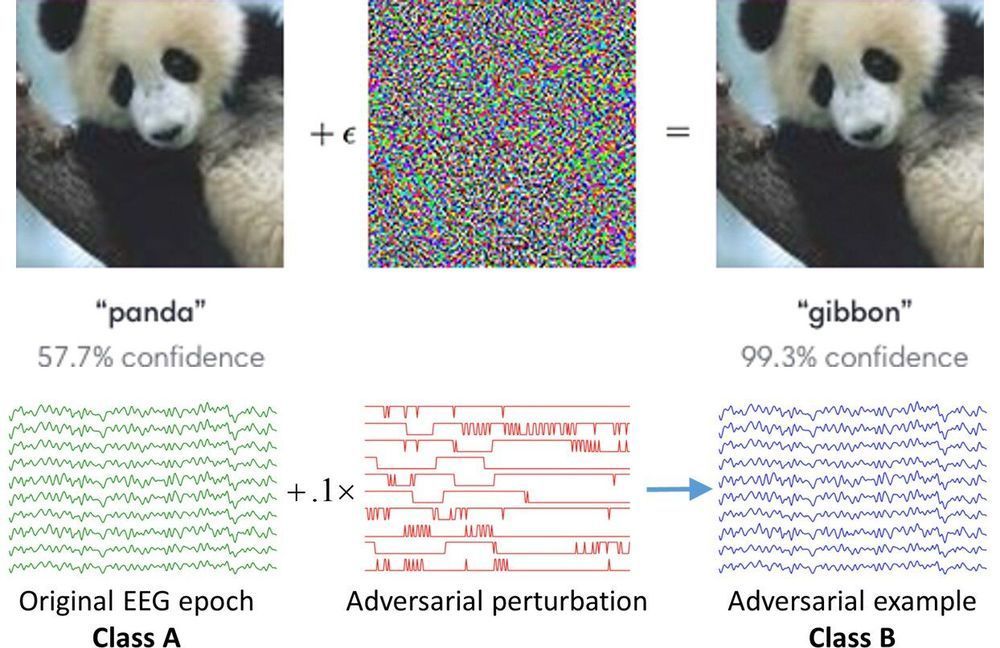
As American drone operators try to understand how the U.S. Federal Aviation Administration’s (FAA) drone Remote Identification proposal would affect them, one of the most concerning issues is proving to be the requirement that every drone transmit the location of its pilot in near-real time.
The ability to locate a drone pilot is extremely useful for police, airports and other authorities to quickly resolve safety and security challenges, but we also understand why some drone pilots don’t want their location available to just anyone. DJI, like other companies innovating Remote ID systems, must follow the FAA’s lead on pilot location, so our demonstration solutions have made that information available to anyone with a smartphone. But that requirement isn’t final.
Now, two new developments are shining a spotlight on the FAA’s proposed pilot location requirement – and at just the right time when American drone pilots can make their voices heard about it.