Last week, U.S. Senator Richard Blumenthal grilled wireless industry representatives, who admitted the industry has done ZERO health & safety studies on 5G technology. Meanwhile, dozens of independent studies indicates that 5G is a risk to all biological life. Watch the video above, on YouTube here, or on Facebook here.
Category: internet – Page 247

Judge approves $26 billion merger of T-Mobile and Sprint
Several state attorneys general had argued that combining the No. 3 and No. 4 carriers would limit competition and result in higher prices for consumers.
Sprint and T-Mobile say their merger will help them compete against top players AT&T and Verizon, and advance efforts to build a nationwide 5G network. Andrew Harrer / Bloomberg via Getty Images file.
Information theft via manipulating screen brightness in air-gapped computers
Data can be stolen from an air gapped personal computer just by using variations in screen brightness. Researchers at Ben-Gurion University wrote a paper on it.
As the team defines them, “Air-gapped computers are systems that are kept isolated from the Internet since they store or process sensitive information.”
That they have come up with yet another discovery on how to wrest sensitive data from a computer came as no shock to Naked Security, which recognized that “Researchers at Ben-Gurion University of the Negev have made a name for themselves figuring out how to get data out of air-gapped computers. They’ve dreamed up ways to communicate using speakers, blinking LEDs in PCs, infrared lights in surveillance cameras, and even computer fans.”

Sun’s surface
No, these are not pictures of caramel corn—they’re the new close-ups of the sun, taken by the largest solar telescope ever built, and they’re what the Internet has been abuzz about for a week. The Daniel K. Inouye Solar Telescope (DKIST) is able to capture imagery three times more detailed than anything we’ve seen before. What we’re looking at here in this video are huge bubbling cells as big as Texas, transferring heat from the sun’s interior to its surface, but the telescope can also resolve tiny features as small as Manhattan Island within the cells!
The DKIST is about 13 feet wide and has a better-than-bird’s-eye-view at 10,000 feet above sea-level on the summit of Haleakala, a massive shield volcano on Hawaii’s island Maui. The area covered in this image is about 22,600 miles by 22,600 miles, but the cell-like structures shown are about the size of Texas.
This is only the first time it’s been used so far, and scientists are hoping that in the future it will be helpful in predicting solar weather. Scientists still have a lot of questions about the dynamical processes in the sun and space weather is a focus that can have significant impact on the everyday individual. Space weather has a huge influence on our air travel and satellite communication, sometimes causing power outages and system failures, and our technology has only given us about 48 minutes’ notice until now. The DKIST will help us predict solar flares 48 hours in advance and understand space weather like we never have before.

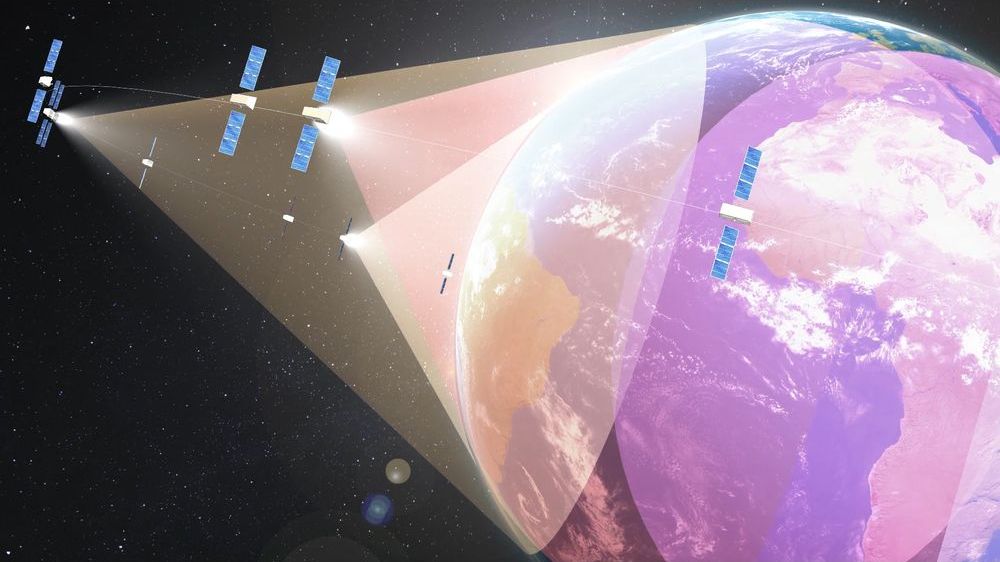
Expanded Partnership with SES to Give Princess Cruises First Access to Ground-Breaking O3b mPOWER Satellite-Based Communications System
Princess Cruises to host a series of events in 2020 to demonstrate elite global connectivity.
LUXEMBOURG & SANTA CLARITA, Calif. — Princess Cruises, a leading brand of the Carnival Corporation & plc (NYSE/LSE: CCL; NYSE: CUK), has announced a new dimension in its connectivity partnership with SES (PAR/LuxSE: SESG) and will become the first global cruise ship fleet with early access to SES’s ground-breaking O3b mPOWER network augmenting the Princess MedallionClass™ experience as it scales across the fleet.
SES is enabling global, high-performance connectivity to Princess Cruises using its hybrid medium earth orbit (MEO) and geostationary (GEO) network. The combination of the globally-deployed Princess MedallionClass ships, the Ocean Guest Experience “Cloud Connected” Platform and SES’s multi-constellations satellite network not only creates unmatched and ubiquitous global Wi-Fi service levels, but ensures seamless land/sea digital experience enablement including OceanView® TV (OTT, Mobile and VOD) and is disrupting the traditional commodity satellite bandwidth model.

OneWeb joins the satellite Internet gold rush this week
It’s a model the company believes makes sense because the right answer for getting regulatory approval and delivering service in the United States or the Philippines or Indonesia will vary, Steckel said. “We’re going to be doing business with partners around the world,” Steckel said. “Our style is not confrontational. We’re using a different model. It’s a big world.”
OneWeb plans to offer its first customer demonstrations by the end of 2020 and provide full commercial global services in 2021.
How one entrepreneur is tackling humanity’s most pressing problems
Braintree founder Bryan Johnson, MBA’07, invests in bold ventures on the next frontier.
Bryan Johnson is determined to explore the depths of your mind and help save humanity from its direst threats.
“The biggest revolutions that have happened over the past couple of decades have largely been done on silicon—the transistors we build, the computers we have, the internet, our smartphones,” said Johnson, MBA’07. “The next great revolutions will be evolving our cognition and predictably engineering atoms, molecules, organisms and complex systems.”

Elephant rescued from well with physics principle. ‘What an idea,’ says Twitter
How interesting. Very adorable.
A heartwarming rescue of a baby elephant with the help of physics is winning the Internet. A tweet by IFS officer Ramesh Pandey gives a glimpse of the rescue efforts made by people and officials in Gumla, Jharkhand.
According to the tweet, the forest department along with people from the nearby village rescued the elephant using the Archimedes principle. Officials and locals filled the well with water to help the elephant out. The elephant was rescued without any injury.
“Heartwarming pictures of how intelligently the team @dfogumla and villagers used Archimedes’s physical law of buoyancy to save an elephant calf who fell in a well. They pumped water into well to float the elephant to surface. Great work,” says the caption posted by Pandey.