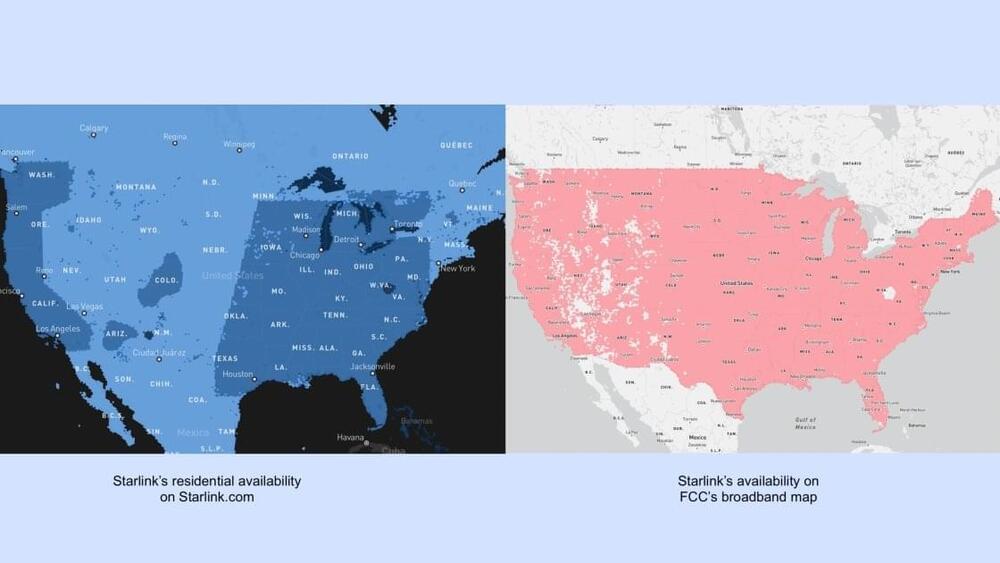
SpaceX writes to the FCC after people notice that the FCC’s official broadband maps say Starlink is available in areas where users face long waitlists.

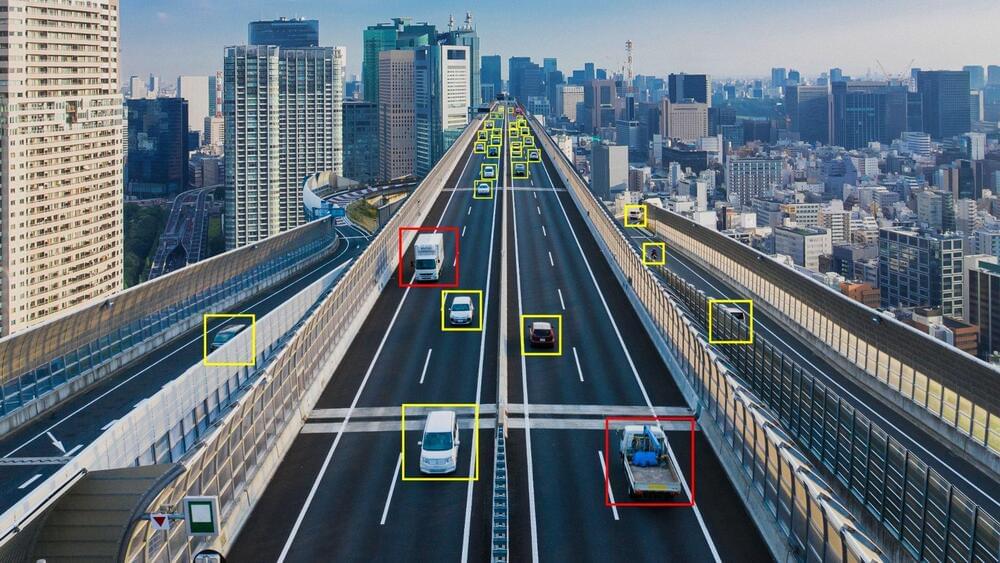
The Connected Car Data Initiative aims to reduce traffic congestion & CO2 emissions.
Nippon Telegraph and Telephone Corporation (NTT) is planning to commercialize its Connected Car Data Initiative to reduce traffic congestion & CO2 emissions. The initiative was developed by its subsidiary firm named NTT Data, which is a global digital and IT services provider based in Japan.
As a trusted global innovator, NTT DATA is leading the way for our retail and automotive clients to unlock the full potential of connected car data.
Metamorworks/iStock.
The technology provides the ability to monitor and analyze data from millions of cars connected to the internet. The setup can be ready as early as the end of 2023.

Yuli Ban is talking about the prediction and emergence of generative AIs, the extent to which those can disrupt humanities reliance on creativity and productivity. He mentions ‘the dead internet theory’ that postulates that most content is autogenerated, obfuscating the actual people using the internet and reducing their actual exposure.
I think we already see this in social media, internet forums and other areas where fake content and profiles are detected. and this can spread to youtube and short form video platforms, telemarketing and scams. as well as use by political groups and states.
Yuli also mentions the long term implications — peaking human population and the notion of Transhumanism where humans merge with an infinitely more capable AI which assumes control. he mentions how biology is a quality many would like to preserve, to varying degrees.

To coincide with the rollout of the ChatGPT API, OpenAI today launched the Whisper API, a hosted version of the open source Whisper speech-to-text model that the company released in September.
Priced at $0.006 per minute, Whisper is an automatic speech recognition system that OpenAI claims enables “robust” transcription in multiple languages as well as translation from those languages into English. It takes files in a variety of formats, including M4A, MP3, MP4, MPEG, MPGA, WAV and WEBM.
Countless organizations have developed highly capable speech recognition systems, which sit at the core of software and services from tech giants like Google, Amazon and Meta. But what makes Whisper different is that it was trained on 680,000 hours of multilingual and “multitask” data collected from the web, according to OpenAI president and chairman Greg Brockman, which lead to improved recognition of unique accents, background noise and technical jargon.

Meta’s AR glasses could be launched in 2027.
Mark Zuckerberg’s Meta Platforms is doubling down on its virtual reality (VR) products and plans to rope in augmented reality (AR) experiences. It looks to define its position in the technology industry a few years from now. Thousands of employees of the Reality Labs Division at Meta were recently presented with a roadmap for the company’s products, which was then shared with The Verge.
VR, AR, and neural interfacesAlthough Zuckerberg has spoken mainly of the metaverse that the company would build as the future of the internet, Meta now seems to have taken its foot off the pedal to make the metaverse itself and focus on the tools instead and improving them.
Coming out later this year is the Meta Quest 3, the flagship product from the company. It is expected to be twice as powerful but half the thickness of its predecessor—the Quest 2. Meta has sold more than 20 million Quest headsets so far, so the Quest 3 sales will be a benchmark to determine if customers are interested in these products.
Priced at $400, Quest 3 will also feature front-facing cameras that will make it less immersive than its predecessors but add the ability to deliver mixed reality experiences to users. Meta is hopeful that this will prompt users to keep the headsets on for longer and plans to ship 41 new apps and games with this headset.

The new Starlink satellites are a precursor for larger models that will eventually launch aboard Starship.
SpaceX lifted the first batch of its new Starlink “V2 mini” satellites to orbit on Monday, February 27. The private space firm launched 21 of the new generation satellites aboard a Falcon 9 rocket that also came down to perform the 100th successful booster landing in a row for the company.
The Starlink mission took to the skies at 6:13 pm EST (2313 GMT) from Florida’s Cape Canaveral Space Force Station. The launch was delayed roughly five hours before liftoff due to “a space weather concern,” SpaceX explained on Twitter.
Twitter / SpaceX
The private space firm launched 21 of the new generation satellites aboard a Falcon 9 rocket that also came down to perform the 100th successful booster landing in a row for the company.
This is the second of two articles on Celesta Capital’s TechSurge Summit on February 13, 2023. In this article I will include discussions of a semiconductor panel and also some comments by Internet Legend, Vint Cerf on ethical use of technology and how to get AI to be more useful.
Jason DiLullo, President of Qatalyst Partners chaired a session at the TechSurge Summit talking about the semiconductor market. This panel included Sanjay Mehrotra, President and CEO of Micron,;Rene Haas, CEO of Arm and Ronnie Chatterji, the White House CHIPS Act Coordinator.
Sanjay had a number of things to say regarding the semiconductor industry and in particular the semiconductor memory industry.
However, AI programs such as alpha fold, which predicts how proteins will fold, is enormously helpful. He also mentioned that making information available on things that don’t work could be very helpful and suggested that we should publish our mistakes as well as our successes. This is also a good lesson for entrepreneurs, if something doesn’t work find this out as soon as possible and change or adapt your goals if needed.
A big challenge for AI is to get the system to formulate a working model of what it knows. He gave an example. Any two-year old understands what a table is, but computers have a hard time understanding things about the real world. This is gained by interacting and working with the real world, something that John McCarthy worked on in the early years of AI research.
Sanjay Mehrotra of Micron, spoke about the importance of memory to the semiconductor industry and with Rene Haas and Ronnie Chatterji discussed topics such as the CHIPS act, chiplets and the IP industry. Vint Cerf spoke about an ethical Internet and how to make better AI.

However, these ones are different to the several thousand Starlink satellites that are already circling Earth.
That’s because they sport a more modern and powerful design that gives them four times the capacity for serving customers compared to the original design, SpaceX said. So, yes, it means faster internet speeds for customers.
SpaceX chief Elon Musk confirmed the successful deployment of the new satellites in a tweet.

Yesterday was an example of how things are speeding up at SpaceX. First, they had a launch scrubbed due to problems with its lighter fluid then they had a launch scrubbed due to weather. Then they had a launch delayed due to space weather. Finally, the delayed launch did get off the ground. The point being that SpaceX is so busy these days that even with two scrubs and one delay, they still launched to orbit!
This launch featured the first Starlink 2.0 satellites. Besides a 4 times increase in capacity compared to version 1.5 satellites, they also include brand new ion engines which are the first ion engines to use argon that have ever been produced.
Finally, this launch ended in the 100th successful landing in a row for SpaceX. Almost no other space company has completed 100 successful launches, forget about landings! (Currently everyone else is crashing and burning all their orbital rockets.)
The company offers more details about satellites for its second-generation Starlink network, which promises to offer even better broadband quality.