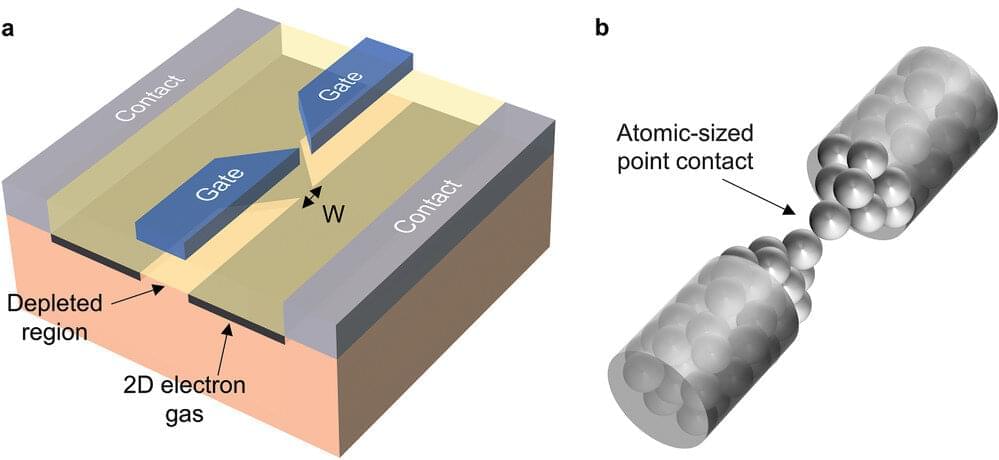
At the nanoscale, the laws of classical physics suddenly become inadequate to explain the behavior of matter. It is precisely at this juncture that quantum theory comes into play, effectively describing the physical phenomena characteristic of the atomic and subatomic world. Thanks to the different behavior of matter on these length and energy scales, it is possible to develop new materials, devices and technologies based on quantum effects, which could yield a real quantum revolution that promises to innovate areas such as cryptography, telecommunications and computation.
The physics of very small objects, already at the basis of many technologies that we use today, is intrinsically linked to the world of nanotechnologies, the branch of applied science dealing with the control of matter at the nanometer scale (a nanometer is one billionth of a meter). This control of matter at the nanoscale is at the basis of the development of new electronic devices.
Among these, memristors are considered promising devices for the realization of new computational architectures emulating functions of our brain, allowing the creation of increasingly efficient computation systems suitable for the development of the entire artificial intelligence sector, as recently shown by Istituto Nazionale di Ricerca Metrologica (INRiM) researchers in collaboration with several international universities and research institutes.