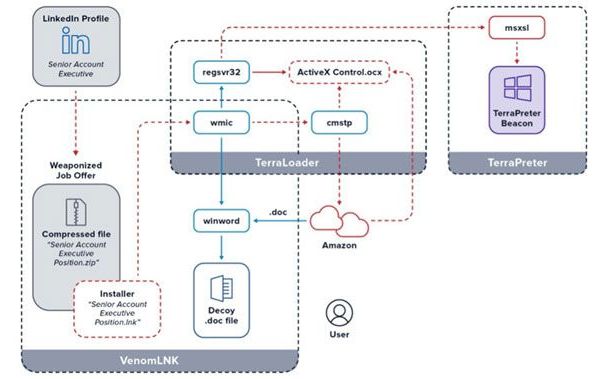
A new spear-phishing campaign is targeting professionals on LinkedIn with weaponized job offers in an attempt to infect targets with a sophisticated backdoor trojan called “more_eggs.”
To increase the odds of success, the phishing lures take advantage of malicious ZIP archive files that have the same name as that of the victims’ job titles taken from their LinkedIn profiles.
“For example, if the LinkedIn member’s job is listed as Senior Account Executive—International Freight the malicious zip file would be titled Senior Account Executive—International Freight position (note the ‘position’ added to the end),” cybersecurity firm eSentire’s Threat Response Unit (TRU) said in an analysis. “Upon opening the fake job offer, the victim unwittingly initiates the stealthy installation of the fileless backdoor, more_eggs.”