Researchers exploit ring interconnect to develop new side-channel attacks on intel cpus.


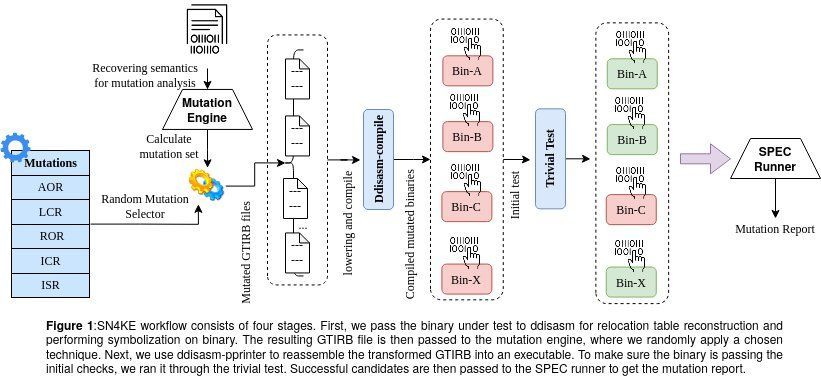
When developers deliver software to their clients, they often also provide what is known as a ‘test suite.’ A test suite is a tool that allows users to test software, unveil any bugs it might have and give developers a chance to fix these bugs or other potential issues.
In addition to evaluating software, therefore, developers also need to ascertain the efficacy of a test suite in identifying bugs and errors. One way to run test suite evaluations is via mutation testing, a technique that generates several ‘mutants’ of a program by slightly modifying its original code. While mutation testing tools have proved to be incredibly helpful, most of them cannot be applied to software that is only available in binary code (a way of representing texts or instructions for computers using two symbols, generally ‘0’ and ‘1’).
Researchers at Arizona State University, Worcester Polytechnic Institute and the University of Minnesota have recently developed SN4KE, a framework that can be used to carry out mutation analyses at a binary level. This framework, presented at the Binary Analysis Research (BAR) NDSS symposium ‘21 in February, is a new tool to efficiently test suites for software based on binary codes.

A new type of supply chain attack unveiled last month is targeting more and more companies, with new rounds this week taking aim at Microsoft, Amazon, Slack, Lyft, Zillow, and an unknown number of others. In weeks past, Apple, Microsoft, Tesla, and 32 other companies were targeted by a similar attack that allowed a security researcher to execute unauthorized code inside their networks.
The latest attack against Microsoft was also carried out as a proof-of-concept by a researcher. Attacks targeting Amazon, Slack, Lyft, and Zillow, by contrast, were malicious, but it’s not clear if they succeeded in executing the malware inside their networks. The npm and PyPi open source code repositories, meanwhile, have been flooded with more than 5000 proof-of-concept packages, according to Sonatype, a firm that helps customers secure the applications they develop.
“Given the daily volume of suspicious npm packages being picked up by Sonatype’s automated malware detection systems, we only expect this trend to increase, with adversaries abusing dependency confusion to conduct even more sinister activities,” Sonatype researcher Ax Sharma wrote earlier this week.
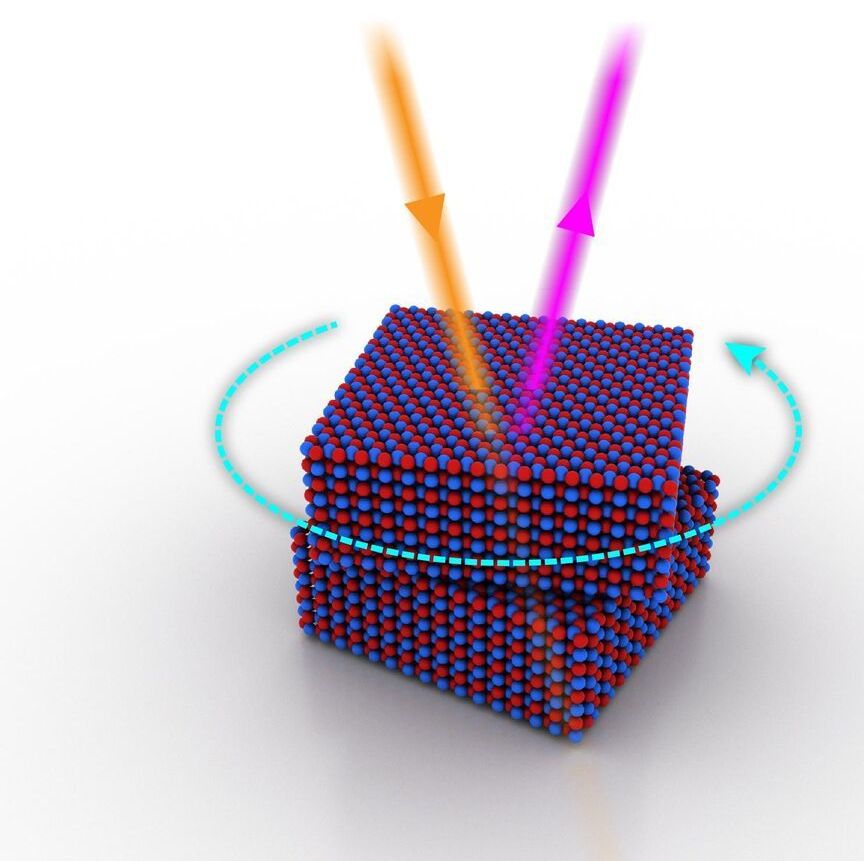
Columbia researchers engineer first technique to exploit the tunable symmetry of 2D materials for nonlinear optical applications, including laser, optical spectroscopy, imaging, and metrology systems, as well as next-generation optical quantum information processing and computing.
Nonlinear optics, a study of how light interacts with matter, is critical to many photonic applications, from the green laser pointers we’re all familiar with to intense broadband (white) light sources for quantum photonics that enable optical quantum computing, super-resolution imaging, optical sensing and ranging, and more. Through nonlinear optics, researchers are discovering new ways to use light, from getting a closer look at ultrafast processes in physics, biology, and chemistry to enhancing communication and navigation, solar energy harvesting, medical testing, and cybersecurity.
Columbia Engineering researchers report that they developed a new, efficient way to modulate and enhance an important type of nonlinear optical process: optical second harmonic generation — where two input photons are combined in the material to produce one photon with twice the energy — from hexagonal boron nitride through micromechanical rotation and multilayer stacking. The study was published online on March 32021, by Science Advances.
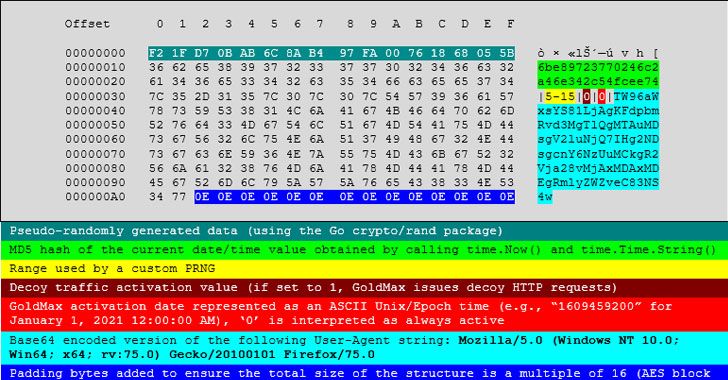
FireEye and Microsoft on Thursday said they discovered three more malware strains in connection with the SolarWinds supply-chain attack, including a “sophisticated second-stage backdoor,” as the investigation into the sprawling espionage campaign continues to yield fresh clues about the threat actor’s tactics and techniques.
Dubbed GoldMax (aka SUNSHUTTLE), GoldFinder, and Sibot, the new set of malware adds to a growing list of malicious tools such as Sunspot, Sunburst (or Solorigate), Teardrop, and Raindrop that were stealthily delivered to enterprise networks by alleged Russian operatives.



Under our RADICS program, researchers developed tools to aid in the rapid recovery of our power grids amidst a cyberattack. Today we’re spotlighting the program’s many accomplishments: https://www.darpa.mil/news-events/2021-02-23
Under our RADICS program, researchers developed tools to aid in the rapid recovery of our power grids amidst a cyberattack. Today we’re spotlighting the program’s many accomplishments: https://t.co/ki0VV5bKlI pic.twitter.com/c1dSVewK2b
— DARPA (@DARPA) February 23, 2021

