Sagnac interferometer has the potential to outperform today’s chip-based technologies.


Journalist Chip Walter visited our friends at Willoughby-Eastlake Public Library earlier this month to discuss his new book, “Immortality, Inc.” Walter discusses the resources (both the brilliant people and astonishing amount of money) being dedicated to seeing if people do, in fact, have to die.

In the era of modern world, medicals advances are evident everywhere. Recently, a team of doctors, researchers and scientists have collaborated to create an electronic biosensor which can be incorporated inside a brain to measure or determine the pH, temperature, flow rates and pressure of the brain. Moreover, it dissolves when no longer needed without the need of any surgical procedure. It is widely applicable in Neuroscience field as brain trauma and injuries kill around 50,000 people per year in the USA alone. These kinds of injuries often cause the brain to swell, which constricts the flow of blood and oxygen, and can lead to permanent damage. So surgeons need reliable ways of monitoring the pressure inside their patients’ head. Earlier, sensors that existed were usually large, heavy and solid, thus had to be removed once the patient recovered. But bioresorbable wireless brain sensors are light, handy and could be easily inserted inside the brain to monitor intracranial pressure and temperature. Once the implantable device is not needed, it is absorbed by the body, eliminating the need of surgically removing the device.
Request sample PDF Brochure Here
Wireless brain sensors are devices that help monitoring the temperature, detecting the intracranial pressure, and record brain signaling in the form of brain waves. The essential aim of this wireless brain sensor is of securing the person from emergency situations. The devices are primarily used for patients experiencing conditions such as sleep disorders, traumatic brain injury, dementia, Parkinson’s disease, and other neurological conditions. These devices aid in observing and monitoring the neurological deviations and provide support for improving the cognitive functionalities. Accessibility of these sensors is easy from a remote area through wireless connectivity and be integrated with smart phones, tablets and computers, consequently be monitored intermittently from a homecare environment, making the device more cost-efficient.

The advancements that are being made in battery technology are pretty mind boggling. We are seeing devices that are drawing power from just about every source that is imaginable, and now there is battery technology from researchers at Imperial College London that may actually have devices that create their own power. From cell phones to cars and everything in between, there may eventually be nothing more needed that to actually use the device.
This incredible new battery technology works because of the material that is being used in the actual construction of the items. The reason that the new material is making headlines is because of the fact that it can be integrated into the design of an automobile and would make it lighter and more fuel efficient, but could actually supply power to recharge the battery of an electric car.
With the material being able to be strong enough for the construction of a car, there are many other possibilities for its use. Right off the bat, devices such as cell phones, iPods, laptops and anything else that you can think of that would use battery power would be able to benefit from this new battery technology.
Quantum computing isn’t yet far enough along that it could have helped curb the spread of this coronavirus outbreak. But this emerging field of computing will almost certainly help scientists and researchers confront future crises.
“Can we compress the rate at which we discover, for example, a treatment or an approach to this?” asks Dario Gil, the director of IBM Research. “The goal is to do everything that we are doing today in terms of discovery of materials, chemistry, things like that, (in) factors of 10 times better, 100 times better,”
And that, he says, “could be game-changing.”
Essentially the microchip that heals article turns the normal process of healing into an accelerated way but eventually crispr could be used to make super fast healing and regeneration.
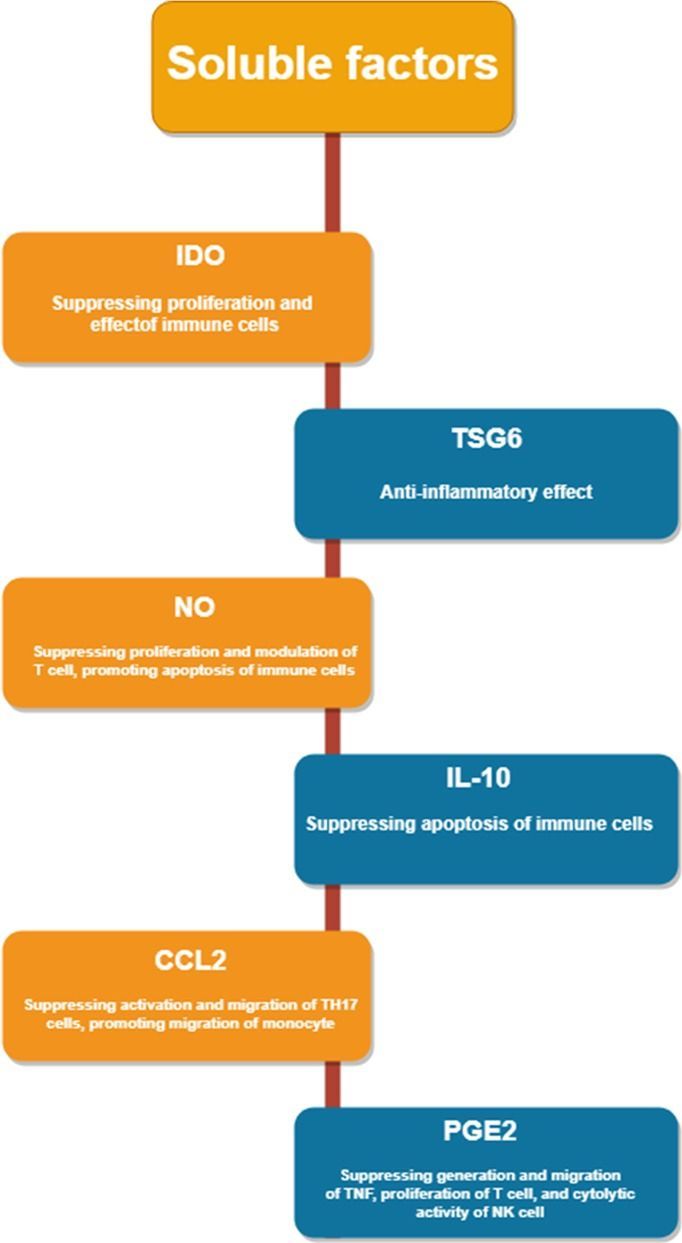
Normal wound healing is a dynamic and complex multiple phase process involving coordinated interactions between growth factors, cytokines, chemokines, and various cells. Any failure in these phases may lead wounds to become chronic and have abnormal scar formation. Chronic wounds affect patients’ quality of life, since they require repetitive treatments and incur considerable medical costs. Thus, much effort has been focused on developing novel therapeutic approaches for wound treatment. Stem-cell-based therapeutic strategies have been proposed to treat these wounds. They have shown considerable potential for improving the rate and quality of wound healing and regenerating the skin. However, there are many challenges for using stem cells in skin regeneration. In this review, we present some sets of the data published on using embryonic stem cells, induced pluripotent stem cells, and adult stem cells in healing wounds. Additionally, we will discuss the different angles whereby these cells can contribute to their unique features and show the current drawbacks.
Circa 2002 4 lines of code to solve everything.
… But first it cracked him. The inside story of how Stephen went from boy genius to recluse to science renegade.
Word had been out that Stephen, the onetime enfant terrible of the science world, was working on a book that would Say It All, a paradigm-busting tome that would not only be the definitive account on complexity theory but also the opening gambit in a new way to view the universe. But no one had read it.
Though physically unimposing with a soft, round face and a droll English accent polished at Eton and Oxford, had already established himself as a larger-than-life figure in the gossipy world of science. A series of much-discussed reinventions made him sort of the Bob Dylan of physics. He’d been a child genius, and at 21 had been the youngest member of the storied first class of MacArthur genius awards. After laying the groundwork for a brilliant career in particle physics, he’d suddenly switched to the untraditional pursuit of studying complex systems, and, to the establishment’s dismay, dared to pioneer the use of computers as a primary research tool. Then he seemed to turn his back on that field. He started a software company to sell Mathematica, a computer language he’d written that did for higher math what the spreadsheet did for business. It made him a rich man. Now he had supposedly returned to science to write a book that would make the biggest splash of all.

Electric supply is one of the lacking necessity in certain parts of the world even until today. Thinking to overcome this problem, these three siblings from the Philippines came out with one genius invention.
Aisa Mijeno is a computer engineering graduate who came out with the idea to make a lamp that runs on salt water together with her brothers Ralph Mijeno and Oscar Bryan Magtibay.
Aisa Mijeno is currently a member of the engineering faculty of the De La Salle University in Lipa, Batangas.

My most recent post, “Living in a Computer Simulation,” elicited some insightful comments from a reader skeptical of the possibility of mind uploading. Here is his argument with my own brief response to it below.
My comment concerns a reductive physicalist theory of the mind, which is the view that all mental states and properties of the mind will eventually be explained by scientific accounts of physiological processes and states … Basically, my argument is that for this view of the mind, mind uploading into a computer is completely impractical due to accumulation of errors.
In order to replicate the functioning of a “specific” human mind within a computer, one needs to replicate the functioning of all parts of that specific brain within the computer. [In fact, the whole human body needs to be represented because the mind is a product of all sensations of all parts of the body coalescing within the brain. But, for the sake of argument, let’s just consider replicating only the brain.] In order to represent a specific human brain in the computer, each neuron in the brain would need a digital or analog representation, instantiated in hardware, software or a combination of the two. Unless this representation is an exact biological copy (clone), it will have some inherent “error” associated with it. So, let’s do a sort of “error analysis” (admittedly non-rigorous).