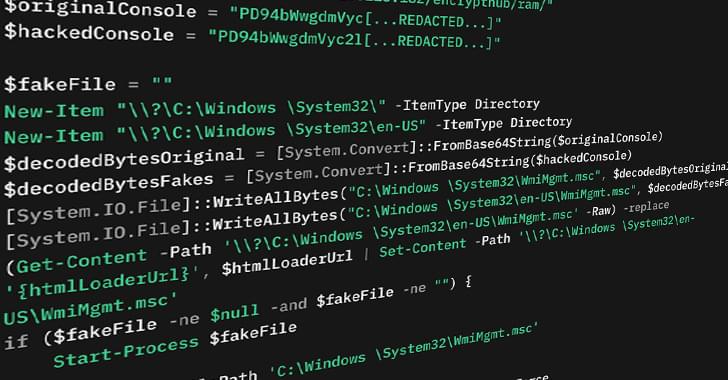
The threat actor known as EncryptHub exploited a recently-patched security vulnerability in Microsoft Windows as a zero-day to deliver a wide range of malware families, including backdoors and information stealers such as Rhadamanthys and StealC.
“In this attack, the threat actor manipulates.msc files and the Multilingual User Interface Path (MUIPath) to download and execute malicious payload, maintain persistence and steal sensitive data from infected systems,” Trend Micro researcher Aliakbar Zahravi said in an analysis.
The vulnerability in question is CVE-2025–26633 (CVSS score: 7.0), described by Microsoft as an improper neutralization vulnerability in Microsoft Management Console (MMC) that could allow an attacker to bypass a security feature locally. It was fixed by the company earlier this month as part of its Patch Tuesday update.