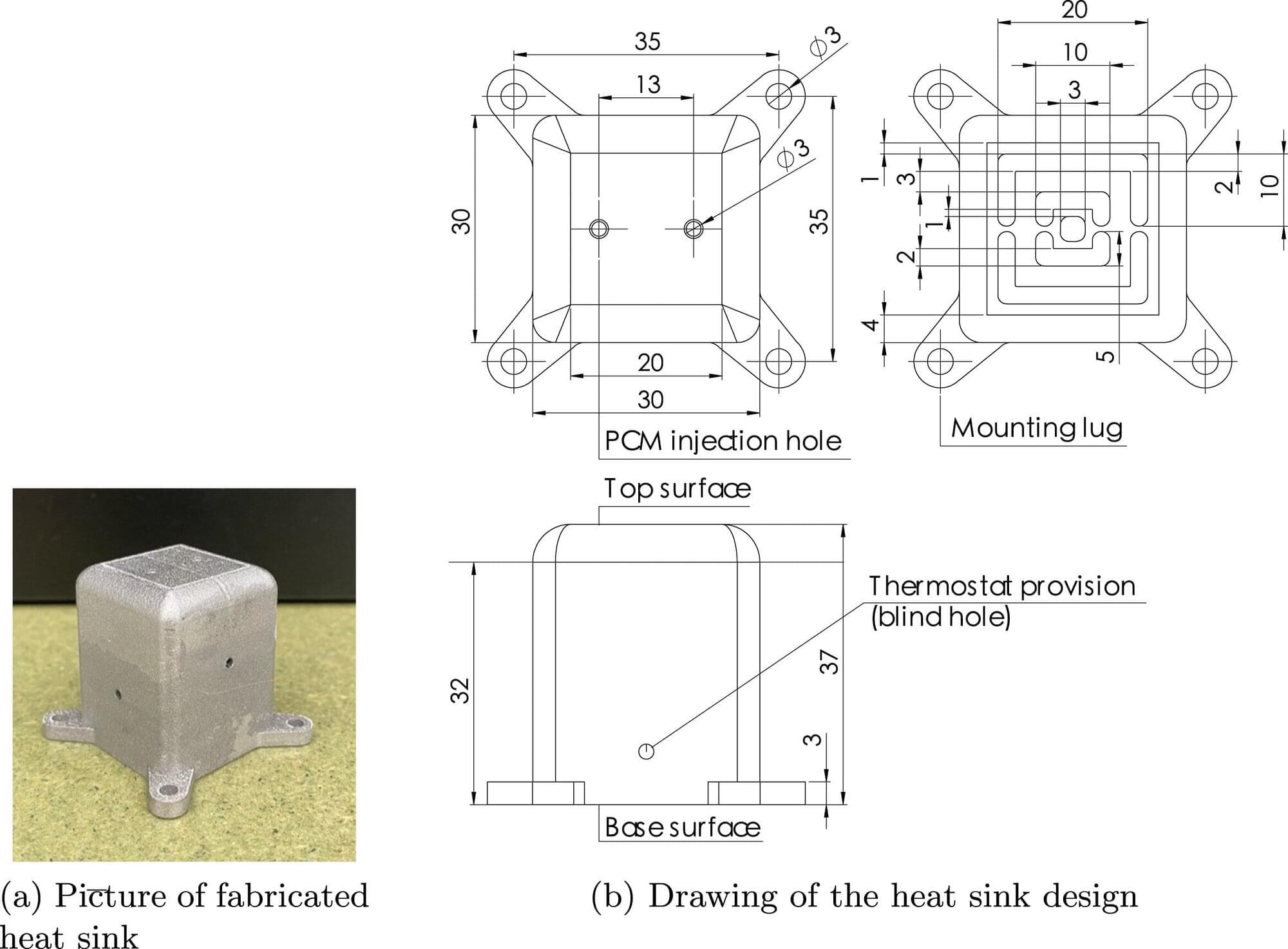
An interdisciplinary research team including mechanical science and engineering professor Mickey Clemon from the Grainger College of Engineering at the University of Illinois Urbana-Champaign is investigating cooling methods for heat sinks by performing experiments onboard a satellite currently orbiting Earth.
“University-sponsored satellites have a very low success rate of making it into space, so we’re very happy that we made it into space and that our system works,” Clemon said.
The team has published the recent findings from their ongoing study, “Investigating the performance of a heat sink for satellite avionics thermal management: From ground-level testing to space-like conditions,” in the International Journal of Heat and Mass Transfer.