A study by Baylor University and Dell Medical School reveals a surprising link between technology use and a reduced risk of dementia in older adults. As the first generation to grow up with digital technology enters an age where dementia risk becomes more relevant, researchers are asking an impor
NASA and partners are building the first quantum gravity sensor for space, a breakthrough instrument that uses ultra-cold atoms to detect tiny shifts in Earth’s gravity from orbit. With potential applications ranging from mapping hidden aquifers to exploring distant planets, this compact, highly
The Ambisonics algorithm generates immersive virtual soundscapes by utilizing a dome-shaped array of loudspeakers. Surround-sound systems can enhance a multimedia experience, but imagine a speaker setup capable of fully recreating a three-dimensional sound environment. Enter the AudioDome — no
Multi-stage phishing attack in Dec 2024 used. JSE, PowerShell, and AutoIt to deliver Agent Tesla.
AI use in SaaS tools bypasses security controls, creating shadow integrations and real breach risks.
XorDDoS malware targeted 71.3% of U.S. systems in latest wave; Docker, IoT, and Linux bots fuel rise.
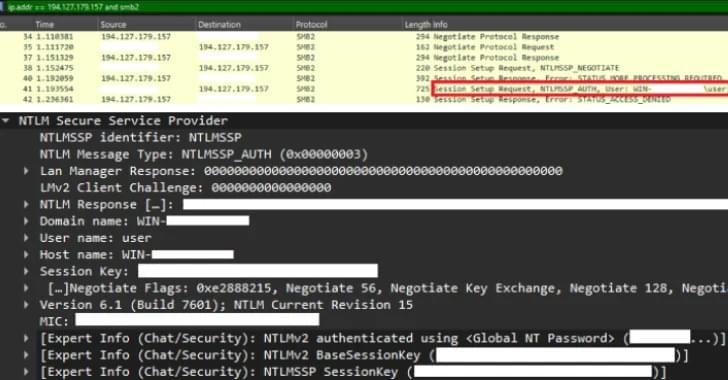
Windows flaw CVE-2025–24054 actively exploited since March 19 to leak NTLM hashes via phishing attacks.
The Interlock ransomware gang now uses ClickFix attacks that impersonate IT tools to breach corporate networks and deploy file-encrypting malware on devices.
ClickFix is a social engineering tactic where victims are tricked into executing dangerous PowerShell commands on their systems to supposedly fix an error or verify themselves, resulting in the installation of malware.
Though this isn’t the first time ClickFix has been linked to ransomware infections, confirmation about Interlock shows an increasing trend in these types of threat actors utilizing the tactic.
A remote code execution vulnerability affecting SonicWall Secure Mobile Access (SMA) appliances has been under active exploitation since at least January 2025, according to cybersecurity company Arctic Wolf.
This security flaw (CVE-2021–20035) impacts SMA 200, SMA 210, SMA 400, SMA 410, and SMA 500v devices and was patched almost four years ago, in September 2021, when SonicWall said it could only be exploited to take down vulnerable appliances in denial-of-service (DoS) attacks.
However, the company updated the four-year-old security advisory on Monday to flag the security bug as exploited in attacks, expand the impact to include remote code execution, and upgrade the CVSS severity score from medium to high severity.
ASUS is warning about an authentication bypass vulnerability in routers with AiCloud enabled that could allow remote attackers to perform unauthorized execution of functions on the device.
The vulnerability, tracked under CVE-2025–2492 and rated critical (CVSS v4 score: 9.2), is remotely exploitable via a specially crafted request and requires no authentication, making it particularly dangerous.
“An improper authentication control vulnerability exists in certain ASUS router firmware series,” reads the vendor’s bulletin.