Einride estimates its autonomous pods will save GE around 970 tons of carbon dioxide emissions in the first year, with that number increasing over time.


Mike straight, founder & CEO of farmpod.
Up next ►► Vertical farms could take over the world https://youtu.be/J4SaSfnHK3I Instead of shipping food all around the world, imagine your own food coming from your farm in a shipping container, just outside your backdoor. That’s the vision of FarmPod, a St. Croix-based startup looking to completely redefine our relationship with food with a fully automated vertical aquaponic system. This self-contained, solar powered farming method uses a fraction of the water and space of a traditional farm, and even uses zero pesticides. The closed loop system essentially mimics nature’s ecosystems, like a pond. Lettuce, strawberries, kale, collard greens and more can grow in the pod. And, since the produce doesn’t need to be picked early to be shipped to a grocery store, the owner can enjoy their harvest at its peak nutritional value and taste. Produce isn’t all — FarmPod can provide an aquaponic home for tilapia, catfish, crayfish, koi, and freshwater prawns. FarmPod uses automated software and hardware to make their pod’s aquaponics system as easy to run as possible. Mike Straight, the creator and CEO of FarmPod, wants to provide a healthy, hyper-localized source of food with a minimal carbon footprint. “We’re trying to feed the world one pod at a time by hyper-localizing farming, and taking the farm and putting it right in front of the place that needs to use it,” says Straight. Read the full story here ►►
https://www.freethink.com/series/challengers/aquaponics ◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠Read more of our stories on aquaponics and sustainable farming:
Vertical farms could take over the world.
►► https://www.freethink.com/series/hard-reset?media_id=avWfzm8Q
How vertical farming can save the planet and feed the world.
►► https://www.freethink.com/series/make-it-count?media_id=bEIXKavd.
New startup takes vertical farming underground — literally.
►► https://www.freethink.com/environment/underground-farm ◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠◠About Freethink.
No politics, no gossip, no cynics. At Freethink, we believe the daily news should inspire people to build a better world. While most media is fueled by toxic politics and negativity, we focus on solutions: the smartest people, the biggest ideas, and the most ground breaking technology shaping our future.◡◡◡◡◡◡◡◡◡◡◡◡◡◡◡◡◡◡◡Watch our original series:
► Hard Reset: https://freeth.ink/youtube-hard-reset.
► Just Might Work: https://freeth.ink/youtube-just-might-work.
► Challengers: https://freeth.ink/youtube-challengers Enjoy Freethink on your favorite platforms:
► Daily editorial features: http://www.freethink.com
► Solutions-based stories, straight to your inbox: https://www.freethink.com/subscribe.
► Facebook: https://www.facebook.com/freethinkmedia
► Instagram: https://www.instagram.com/freethink
► Twitter: https://twitter.com/freethinkmedia
► Join the Freethink form: http://www.facebook.com/groups/freethinkforum
A new type of plastic can rapidly heal itself under water, even in harsh conditions. It maintains its strength after self-healing, so it may be useful in emergencies at sea.
Lili Chen at Tsinghua University in China and her colleagues developed this material, called Rapid Underwater Self-healing Stiff Elastomer (RUSSE) because most self-healing polymers don’t work very well under water. “Room temperature self-healing polymers generally have a poor underwater stability, low healing strength and a slow healing process,” says Chen.
RUSSE is made of small chunks of a type of soft polymer used in some paints connected by nanometre-sized chains of a tougher polymer. The researchers tested the material’s properties by stretching it, cutting it and bashing it with a hammer.
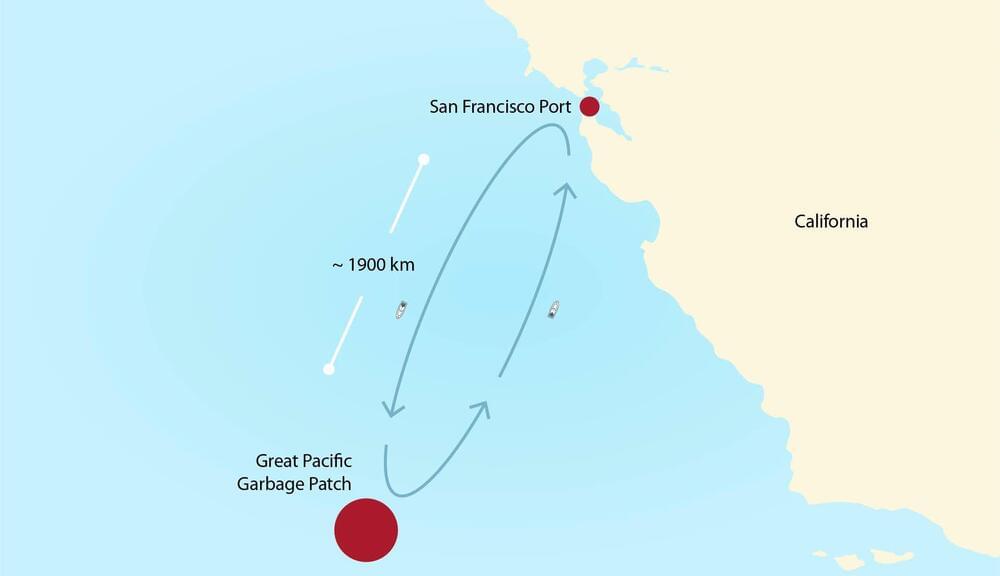
A team of researchers from Worcester Polytechnic Institute, Woods Hole Oceanographic Institution and Harvard University believes that the plastic amassing in floating islands in the oceans could be used to power the ships that are sent to clean them up. In their paper published in Proceedings of the National Academy of Sciences, the group describes how ocean plastics could be converted to ship fuel.
Prior research has shown that millions of tons of plastics enter the ocean each year—some of it is ground into fragments and disperses, and some of it winds up in colossal garbage patches floating in remote parts of the ocean. Because of the danger that such plastics present to ocean life, some environmentalists have begun cleanup operations. Such operations typically involve sending a ship to a garbage patch, collecting as much as the ship will hold and then bringing it back to port for processing. In this new effort, the researchers suggest it would be far more efficient and greener to turn the plastic into fuel for both a processing machine and for uninterrupted operation of the ships.
The researchers note that the plastic in a garbage dump could be converted to a type of oil via hydrothermal liquefaction (HTL). In this process, the plastic is heated to 300–550 degrees Celsius at pressures 250 to 300 times that of sea-level conditions. The researchers have calculated that a ship carrying an HTL converter would be capable of producing enough oil to run the HTL converter and the ship’s engine. Under their scenario, plastic collection booms would be permanently stationed at multiple sites around a large garbage patch, able to load the plastic it collects onto ships.

O,.o circa 2014.
When we hear the term ‘parallel universe’, we often cite the classic science fiction picture of a parallel universe; something that acts as a mirror, where on one day, in this universe, you didn’t manage to have the guts to ask that girl out, but in the parallel universe, not only did ‘you’ ask her out, but a decade later, she became your wife. We all like to subscribe to such fascinating ideas, but for a while, it was relegated to the domain of sci-fi creators/fans. The real picture tells us something a lot more interesting.
AN INFINITE NUMBER OF ‘YOUS’;
The concept of parallel universes is an idea that arises from the multiverse theory, suggesting that our universe is one of many existing universes that, in a manner of speaking, lie parallel to each other. Max Tegmark, a professor at MIT (Massachusetts Institution Technology), has cleverly put out the idea that there are four distinct types of parallel universe. Building on this notion, Dr. Michio Kaku has suggested that if these ideas become reality, depending on which one of the four types of parallel universes that truly exist, there are virtual copies of you in another region of space. One interesting aspect of this to consider, which catches the attention of scientists and philosophers alike, is the issue of morality. How is this relevant? Well; to paraphrase Dr. Michio Kaku, “Why shouldn’t you do something that is considered to be morally wrong in this universe, if you can get away with it in an other?” As striking as that sounds, I wouldn’t get too ahead of the game just yet.

To understand why Mark Zuckerberg thinks “the metaverse” is the next frontier, consider the case of Sam Peurifoy. The 27-year-old chemistry PhD from Columbia University left his job at Goldman Sachs at the height of the pandemic and is now seeking out his fortune in crypto by playing video games.
He has recruited dozens of people from Mexico to the Philippines to a “Guild” that plays under the command of “Captain” Peurifoy. In exchange, he ponies up the funds needed to enter Axie Infinity, a game where players collect Smooth Love Potion — a digital token that can potentially be converted into real money.

Many of the malware campaigns we have detected over the last year have been global at scale, targeting anyone with little regard to their location. Recently, we discovered and began monitoring the activity behind PhoneSpy, a spyware aimed at South Korean residents with Android devices. With more than a thousand South Korean victims, the malicious group behind this invasive campaign has had access to all the data, communications, and services on their devices.
Unlike other spyware campaigns we have covered that take advantage of vulnerabilities on the device, PhoneSpy hides in plain sight, disguising itself as a regular application with purposes ranging from learning Yoga to watching TV and videos, or browsing photos. But in reality, the application is stealing data, messages, images, and remote control of Android phones. The data stolen from victim devices ranged from personal photos to corporate communications. The victims were broadcasting their private information to the malicious actors with zero indication that something was amiss.
While the victims have been limited to South Korea, PhoneSpy is an example of how malicious applications can disguise their true intent. When installed on victims’ devices, they leave personal and corporate data at risk. With mobile devices playing critical roles in distributed and remote work, it is no surprise that spyware campaigns like PhoneSpy are on the rise.

TOKYO, Oct 26 (Reuters) — A Japanese startup backed by soccer player Keisuke Honda hopes to persuade wealthy consumers to swap their supercar for a 77.7 million yen ($680,000) hoverbike which went on sale on Tuesday.
The “XTurismo Limited Edition” from Tokyo-based drone startup A.L.I. Technologies is equipped with a conventional engine and four battery-powered motors and promises to fly for 40 minutes at up to 100 kph (62 mph).
“Until now the choice has been to move on the ground or at scale in the sky. We hope to offer a new method of movement,” Chief Executive Daisuke Katano told Reuters.

Last weekend, the Financial Times reported that China had tested in August a weapon system that used a Long March 2 rocket to boost a nuclear-capable weapon into low-earth orbit, giving it effectively unlimited range.
From this lofty vantage, the system de-orbited a hypersonic glide vehicle towards a target, which it ended up missing by twenty-four miles. A spokesperson from China’s foreign ministry has since claimed that the test had purely civilian purposes.
China’s alleged test of an exotic orbital nuclear weapon system rang alarm bells, even if that initial test demonstrated poor accuracy. Such a system seems intended to literally circumnavigate existing U.S. missile defense radars and interceptors by attacking from an unexpected angle.
