Making the exchange of a message invulnerable to eavesdropping doesn’t strictly require quantum resources. All you need to do is to encrypt the message using a one-use-only random key that is at least as long as the message itself. What quantum physics offers is a way to protect the sharing of such a key by revealing whether anyone other than sender and recipient has accessed it.
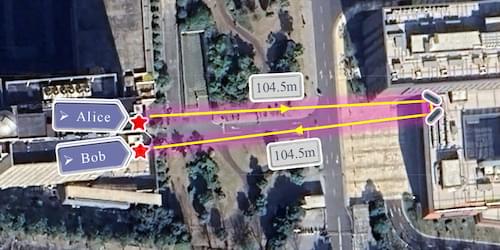
Imagine that a sender (Alice) wants to send a message to a recipient (Bob) in the presence of an eavesdropper (Eve). First, Alice creates a string of random bits. According to one of the most popular quantum communication protocols, known as BB84, Alice then encodes each bit in the polarization state of an individual photon. This encoding can be performed in either of two orientations, or “bases,” which are also chosen at random. Alice sends these photons one at a time to Bob, who measures their polarization states. If Bob chooses to measure a given photon in the basis in which Alice encoded its bit, Bob’s readout of the bit will match that of Alice’s. If he chooses the alternative basis, Bob will measure a random polarization state. Crucially, until Alice and Bob compare their sequence of measurement bases (but not their results) over a public channel, Bob doesn’t know which measurements reflect the bits encoded by Alice. Only after they have made this comparison—and excluded the measurements made in nonmatching bases—can Alice and Bob rule out that eavesdropping took place and agree on the sequence of bits that constitutes their key.
The efficiency and security of this process depend on Alice’s ability to generate single photons on demand. If that photon-generation method is not reliable—for example, if it sometimes fails to generate a photon when one is scheduled—the key will take longer to share. If, on the other hand, the method sometimes generates multiple photons simultaneously, Alice and Bob run the risk of having their privacy compromised, since Eve will occasionally be able to intercept one of those extra photons, which might reveal part of the key. Techniques for detecting such eavesdropping are available, but they involve the sending of additional photons in “decoy states” with randomly chosen intensities. Adding these decoy states, however, increases the complexity of the key-sharing process.