SpaceX is counting on Starship rockets to carry more than 100 metric tons of cargo and crew per launch and help build out the company’s prized Starlink unit.
A harsh sun shines down through a cloudless sky, across a vast and unforgiving landscape. It’s covered in gray rock, giant ice sculptures and expansive fields of spiky, yellow and orange bushes. In the distance, intimidating mountain peaks dominate the desolate scene, many miles from the nearest town. Yet alpacas roam freely and flamingos seek out scarce water, both unexpected sights in this wild world.
The extreme environment resembles something from a sci-fi film or another planet, but it’s right here on Earth, on the flanks of the world’s highest active volcano, 22,615-foot Ojos del Salado. Here, on the border of Argentina and Chile, a team of CU Boulder scientists seek to discover how tiny organisms persist at one of the driest and highest points on the planet.
This first-of-its-kind project may ultimately help inform the search for existing and extinct life on other planets.
It’s at least the third strain of wiper since the conflict began.
Researchers from cybersecurity firm ESET have discovered a new destructive wiper malware, dubbed CaddyWiper, that is affecting computer networks in Ukraine.
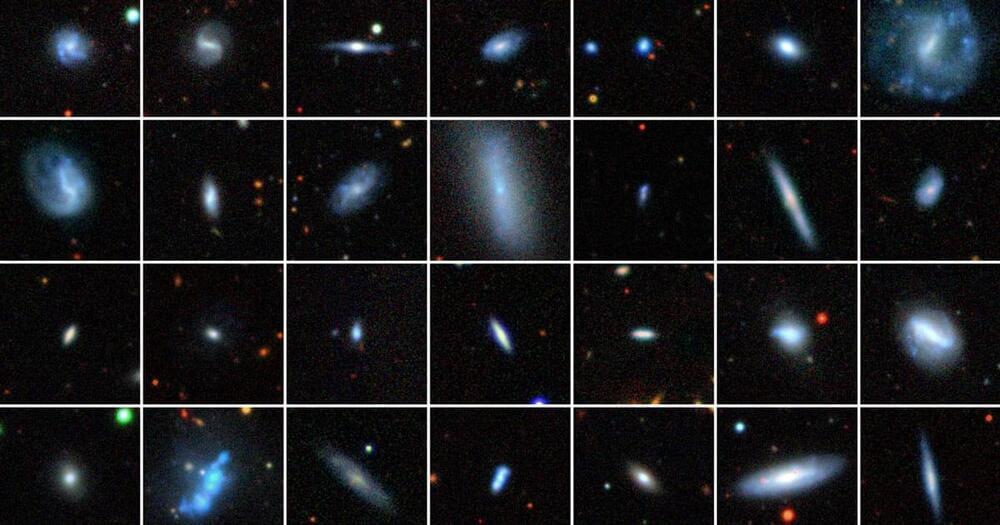
“People keep finding more of them,” said Ryan Hickox, an astronomer at Dartmouth College who recently helped locate one himself. “There may be a lot more of these things in these galaxies than we could find using the traditional techniques.”
Off the Map
Dwarf galaxies are relatively uncharted astronomical territory. Ten to 100 times lighter than the Milky Way, they lack the gravitational moxie to pull themselves into the tidy round shapes amenable to theorizing. They’re also patchy, dim and generally hard to study in detail. “They’re a total mess,” Volonteri said.
New battery material offers promise for the development of all-solid batteries.
In the quest for the perfect battery, scientists have two primary goals: create a device that can store a great deal of energy and do it safely. Many batteries contain liquid electrolytes, which are potentially flammable.
As a result, solid-state lithium-ion batteries, which consist of entirely solid components, have become increasingly attractive to scientists because they offer an enticing combination of higher safety and increased energy density — which is how much energy the battery can store for a given volume.
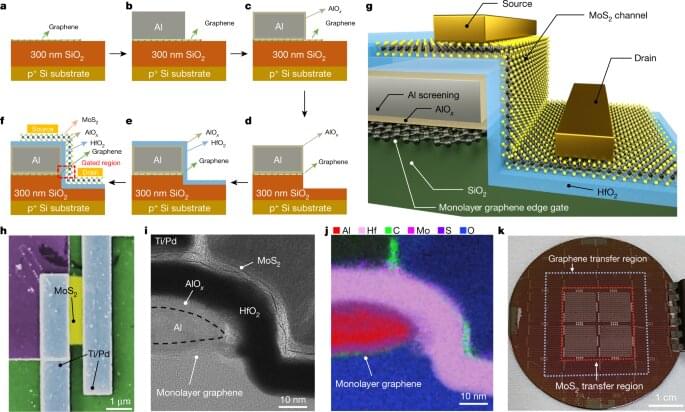
A team of researchers working at Tsinghua University in China has created a sub-1-nm gate in a MoS2 transistor. In their paper published in the journal Nature, the group outlines how they created the super tiny gate and explains why they believe it will be difficult for anyone to beat their record.
For most of the history of microcomputing, Moore’s Law has held up—researchers and engineers have managed to double the speed and capability of computers regularly by reducing the size of their components. But more recently, it has grown increasingly difficult to make components smaller as scientists now run into physical limitations. In this new effort, the researchers believe they may have bumped up against the ultimate limit—they have built a gate that is just one atom in length.
At their most basic, transistors are a source and a drain, with a gate controlling the flow of electricity between them. It switches on and off depending on how much electricity is applied. The push to reduce the size of the components has led to the testing of materials such as carbon nanotubes, which are approximately 1nm, for use as gates. In this new effort, the researchers have unrolled the carbon nanotube and used its graphene edge as the gate—reducing its length to just 0.34 nm.
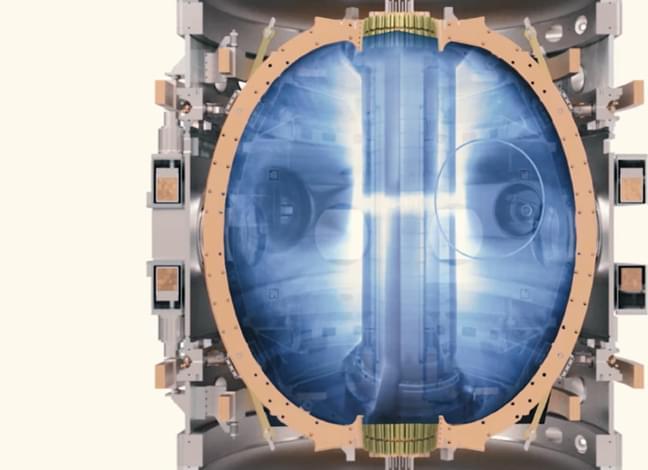
Tokamak Energy, based near Oxford, UK, has demonstrated a world-first with its privately-funded ST40 spherical tokamak. The reactor achieved a plasma temperature of 100 million degrees Celsius, the threshold required for commercial fusion energy.
At nearly seven times hotter than the centre of the Sun, this is by far the highest temperature ever generated within a spherical tokamak and also by any privately-funded tokamak. The ST40 had previously achieved a temperature of 15 million degrees in June 2018. While several government laboratories have reported plasma temperatures above 100 million degrees in conventional tokamaks, this milestone has been achieved in just five years, for a cost of less than £50m ($70m) and in a much more compact fusion device. This provides further proof that spherical tokamaks are a viable route to the delivery of clean, secure, low cost, scalable fusion energy.
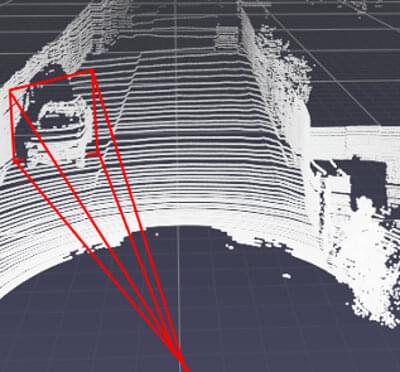
Researchers at Duke University have demonstrated the first attack strategy that can fool industry-standard autonomous vehicle sensors into believing nearby objects are closer (or further) than they appear without being detected.
The research suggests that adding optical 3D capabilities or the ability to share data with nearby cars may be necessary to fully protect autonomous cars from attacks.
The results will be presented Aug. 10–12 at the 2022 USENIX Security Symposium, a top venue in the field.
Little did he know that we would one day have telescopes powerful enough to image distant galaxies.
“[Einstein] had a sense of the natural sublime.”
The first known image of an Einstein ring was captured in 1987 at the Very Large Array radio observatory in New Mexico. A little over a decade later, Hubble found the first complete one. Since then astronomers have found many more of Einstein Rings including this one, which Tommaso Treu’s group in the Department of Physics and Astronomy at the University of Californa, Los Angeles, produced with the Hubble.
Fully vaccinated people will need a fourth shot later in 2022, according to the head of Pfizer Inc., who said that COVID-19 is not going to just go away in the coming years.
Albert Bourla told CBS News anchor Margaret Brennan on “Face the Nation” that people are going to have to learn to live with the virus.
He said a fourth dose — that is, a second booster — is necessary “right now.”