Tesla CEO Elon Musk thinks the automaker’s market capitalization is directly tied to whether the automaker is able to solve autonomous driving.



It seems that Google doesn’t trust any AI chatbot, including its own Bard AI bot. In an update to its security measures, Alphabet Inc., Google’s parent company has asked its employees to keep sensitive data away from public AI chatbots, including their own Bard AI.
According to sources familiar with the matter, Alphabet Inc, the parent organisation of Google, is advising its employees to be cautious when using chatbots, including its own program called Bard, even as it continues to promote the software globally.
The company has updated a longstanding policy to protect confidential information, instructing employees not to input sensitive materials into AI chatbots. These chatbots, such as Bard… More.

Current artificial intelligence systems like ChatGPT do not have human-level intelligence and are not even as smart as a dog, Meta’s AI chief Yann LeCunn said. LeCun talked about the limitations of generative AI, such as ChatGPT, and said they are not very intelligent because they are solely trained on language.
Meta’s LeCun said that, in the future, there will be machines that are more intelligent than humans, which should not be seen as a threat.
Current artificial intelligence systems like ChatGPT do not have human-level intelligence and are barely smarter than a dog, Meta’s AI chief said, as the debate over the dangers of the fast-growing technology rages on.
Meta’s AI chief said the company is working on training AI on video, rather than just on language, which is a tougher task.
In another example of current AI limitations, he said a five-month-old baby would look at an object floating and not think too much of it. However, a nine-month year old baby would look at this item and be surprised, as it realizes that an object shouldn’t float.
LeCun said we have “no idea how to reproduce this capacity with machines today. Until we can do this, we are not going to have human-level intelligence, we are not going to have dog level or cat level [intelligence].”

While the U.K. and U.S. try to block Microsoft’s acquisition of Activision over concerns it will kill competition in games distribution, competition appears to be alive and well in another (smaller) area of gaming: modding and analytics.
Wargraphs, a one-man-band startup behind a popular companion app for League of Legends called Porofessor, which helps players track and improve their playing stats, is getting acquired for up to €50 million ($54 million), half up front and half based on meeting certain earnings and growth targets.
MOBA Networks, a company founded out of Sweden that buys, grows and runs online gaming communities (MOBA is short for “multiplayer online battle arena”), is buying the startup and its existing products. The plan is to expand them to more markets, in particular across Asia, and to build analytics for more titles.
The 12-qubit device will go out to a few academic research labs.
Intel does a lot of things, but it’s mostly noted for making and shipping a lot of processors, many of which have been named after bodies of water. So, saying that the company is set to start sending out a processor called Tunnel Falls would seem unsurprising if it weren’t for some key details. Among them: The processor’s functional units are qubits, and you shouldn’t expect to be able to pick one up on New Egg. Ever.
Tunnel Falls appears to be named after a waterfall near Intel’s Oregon facility, where the company’s quantum research team does much of its work. It’s a 12-qubit chip, which places it well behind the qubit count of many of Intel’s competitors—all of which are making processors available via cloud services. But Jim Clarke, who heads Intel’s quantum efforts, said these differences were due to the company’s distinct approach to developing quantum computers.

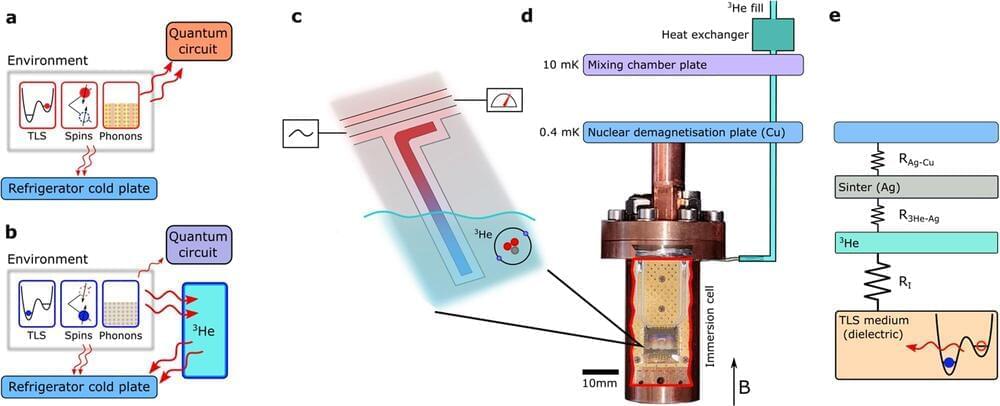
Typical superconducting quantum circuits, such as qubits—basic processing units of a quantum computer, must be operated at very low temperatures, of a few 10s of millikelvin, or hundredths of a degree from absolute zero temperature. These temperatures are today easily accessible in modern refrigerators. However, the intrinsic temperature of devices turns out to be much higher because the materials required to make good qubit circuits are by their nature very poor thermal conductors. This thermalization problem becomes more and more acute as the scale and complexity of circuits grow.
Much like water (or liquid nitrogen) cooling is sometimes used to effectively cool down high-performance digital computers, a quantum computer could benefit from similar liquid cooling. But at the very low temperatures that quantum circuits operate, most liquids will have turned into ice. Only two isotopes of Helium, Helium-3 and Helium-4, remain in the liquid form at millikelvin temperatures.
In recent work published in Nature Communications, researchers from the National Physical Laboratory, Royal Holloway University of London, Chalmers University of Technology and Google developed new technology to cool down a quantum circuit to less than a thousand of a degree above absolute zero, almost 100 times lower temperature than achieved before. This was made possible by immersing the circuit in liquid 3 He, chosen for its superior thermal properties.

A video worth watching. An amazingly detailed deep dive into Sam Altman’s interviews and a high-level look at AI LLMs.
Missed by much of the media, Sam Altman (and co) have revealed at least 16 surprising things over his World Tour. From AI’s designing AIs to ‘unstoppable opensource’, the ‘customisation’ leak (with a new 16k ChatGPT and ‘steerable GPT 4), AI and religion, and possible regrets over having ‘pushed the button’.
I’ll bring in all of this and eleven other insights, together with a new and highly relevant paper just released this week on ‘dual-use’. Whether you are interested in ‘solving climate change by telling AIs to do it’, ‘staring extinction in the face’ or just a deepfake Altman, this video touches on it all, ending with comments from Brockman in Seoul.
I watched over ten hours of interviews to bring you this footage from Jordan, India, Abu Dhabi, UK, South Korea, Germany, Poland, Israel and more.
Altman Abu Dhabi, HUB71, ‘change it’s architecture’: https://youtu.be/RZd870NCukg.
