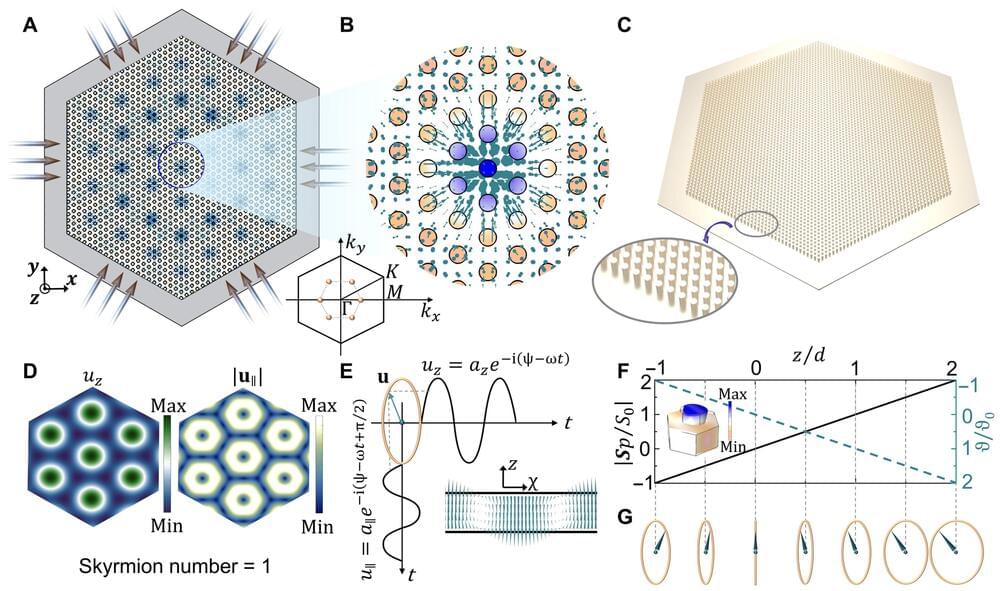
Skyrmions are extremely small with diameters in the nanoscale, and they behave as particles suited for information storage and logic technologies. In 1961, Tony Skyrme formulated a manifestation of the first topological defect to model a particle and coined it as skyrmions. Such particles with topologically stable configurations can launch a promising route toward establishing high-density magnetic and phononic (a discrete unit of quantum vibrational mechanical energy) information processing routes.
In a new report published in Science Advances, Liyun Cao and a team of researchers at the University of Lorraine CNRS, France, experimentally developed phononic skyrmions as new topological structures by using the three-dimensional (3D) hybrid spin of elastic waves. The researchers observed the frequency-independent spin configurations and their progression toward the formation of ultra-broadband phononic skyrmions that could be produced on any solid structure.