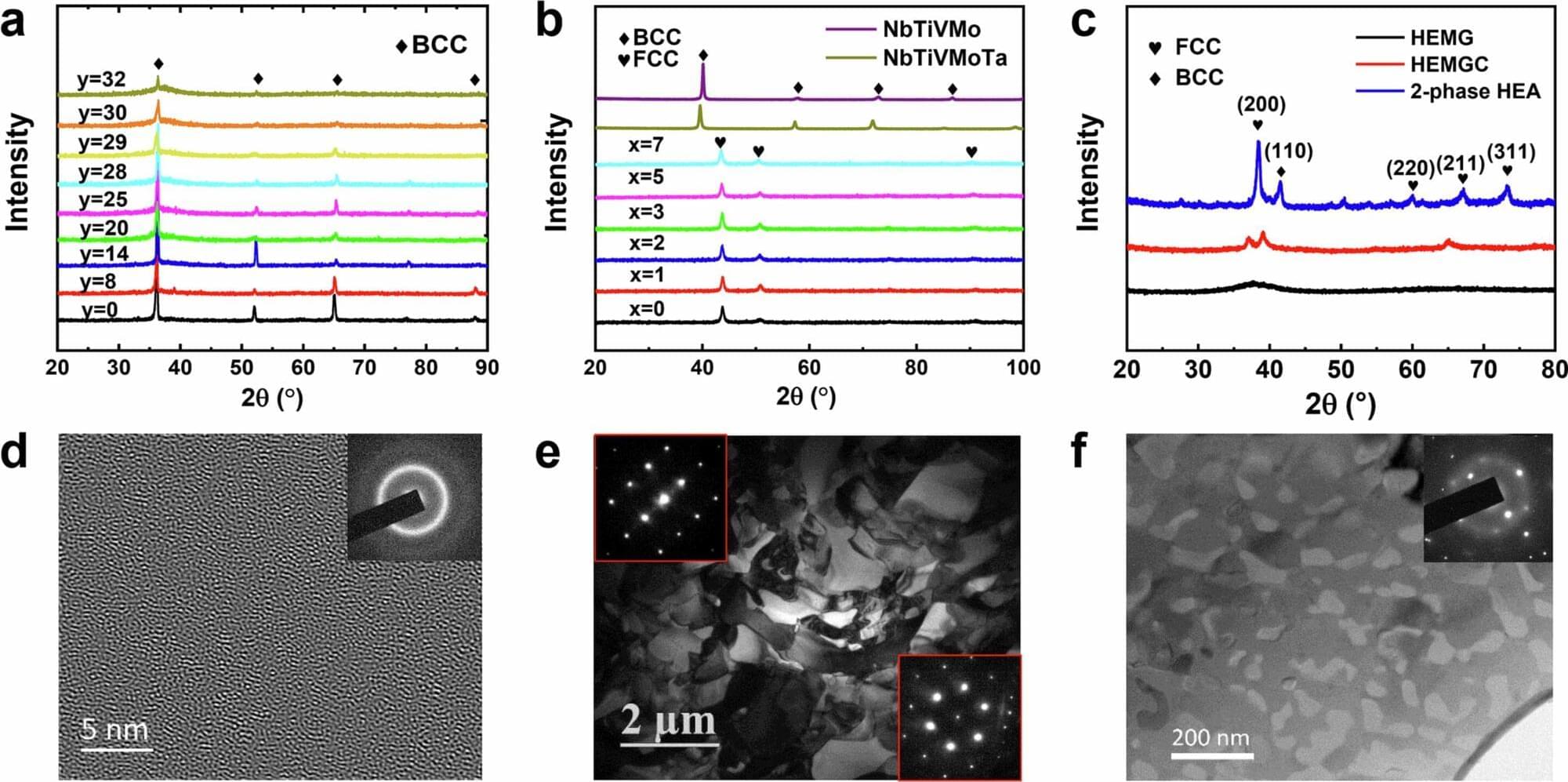
Phonons are sound particles or quantized vibrations of atoms in solid materials. The Debye model, a theory introduced by physicist Peter Debye in 1912, describes the contribution of phonons to the specific heat of materials and explains why the amount of heat required to raise the temperature of solids drops sharply at low temperatures.
The Debye model assumes that vibrational frequencies are continuously distributed in a solid material. Past studies, however, found that when phonons have particularly short wavelengths, some anomalies can emerge.
The first of these reported anomalies, the so-called Van Hove singularity (VHS), is characterized by sharp features in the vibrational density of states (DOS) observed in crystals. The second, known as a boson peak, entails a significant excess in the DOS in amorphous solids or glasses.