Page 4814
May 8, 2022
Apple, Google and Microsoft team up on passwordless logins
Posted by Gemechu Taye in categories: cybercrime/malcode, mobile phones
On the “World Password Day”, which was on May 5, Google, Microsoft and Apple joined hands to “kill” the password.
The three technology giants have vowed to create a future where your phone will be the primary source of online authentication. The new standard is being referred to as “muti-device FIDO credential”.
In a rare show of alliance, Apple, Google and Microsoft have joined forces to expand support for passwordless logins across mobile, desktop and browsers.
Continue reading “Apple, Google and Microsoft team up on passwordless logins” »
May 8, 2022
Explainer: How ‘Common Prosperity’ is Changing China
Posted by Chima Wisdom in category: futurism
China’s drive for “common prosperity” is called a ‘’profound revolution’’ by state media. It has unnerved investors.
May 8, 2022
Today @4 PM Eastern Time!
Posted by Simon Waslander in categories: life extension, Ray Kurzweil
With Raymond Kurzweil’s co-author Dr. Terry Grossman M.D and Dr. The panel will also awnser Longevity questions live. This is your opportunity to get powerful health insights from the World’s leading thinkers in Life Extension.
Sun, May 8 at 3 PM CDT.
Interested.
May 8, 2022
Mouse Study Reveals ‘Master’ Gene to Regrow Lost Ear Hair Cells
Posted by Josh Seeherman in category: futurism
Hearing loss is usually irreversible because there’s no way to grow back the necessary outer and inner ear sensory cells once they’ve been killed off. But we may have started on the path to change, thanks to new research in mice.
Scientists have discovered a single master gene that’s able to regulate whether ear hair cells into the outer or inner types required to restore hearing. That’s a significant step forward in being able to actually carry this out in the lab.
The master gene is called TBX2. Through experiments on mice, the team found that when it’s expressed, ear hair cells become inner hair cells; when it’s blocked, ear hair cells become outer hair cells. It’s a crucial toggle switch.
May 8, 2022
Planning a Career Path in the Face of Disruptive 21st Century Change
Posted by Len Rosen in category: business
Business careers in the 21st century require resilience, flexibility and investment in continuous self-learning.
May 8, 2022
Blood Test Analysis: Italian Centenarians
Posted by Mike Lustgarten in categories: biotech/medical, life extension, robotics/AI, sex
Join us on Patreon!
https://www.patreon.com/MichaelLustgartenPhD
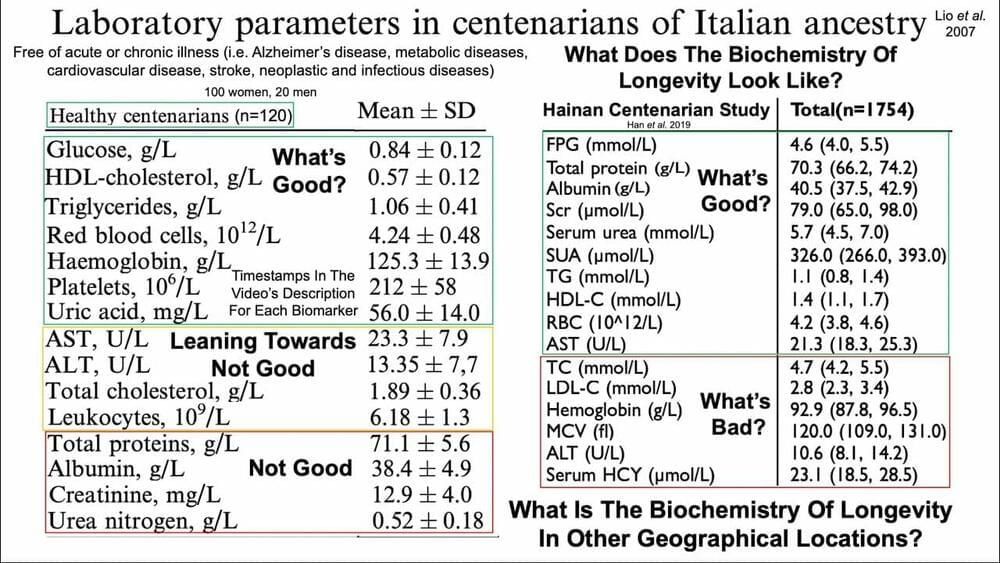
Biomarker timestamps:
Glucose 1:37
HDL 2:43
Triglycerides 4:10
RBCs, Hemoglobin 5:29
Platelets 7:16
Uric Acid 8:37
AST, ALT 11:04
Total Cholesterol 13:55
WBCs 15:47
Total Protein, Albumin, Globulin 17:38
Creatinine 21:27
BUN 22:35
Continue reading “Blood Test Analysis: Italian Centenarians” »
May 8, 2022
Ray Kurzweil — Singularity University GSP09 Metaverse Reunion April 16, 2022
Posted by Kelvin Dafiaghor in categories: Ray Kurzweil, singularity
May 8, 2022
New Hybrid Species Remix Old Genes Creatively
Posted by Shubham Ghosh Roy in category: futurism
Clues from fish diversity suggest that interbreeding between species could be a major mechanism of fast speciation.
May 8, 2022
Cybersecurity reporting mandates could make us more vulnerable, not less
Posted by Shubham Ghosh Roy in categories: cybercrime/malcode, finance, law
Those who call for mandatory reporting have the right intent, but if it’s not implemented in the right way, it will cause more harm than good.
Mandatory reporting almost always puts companies at risk, either legally or through financial penalties. Penalizing an organization for not reporting a breach in time puts it in a worse cybersecurity posture because it is a strong incentive to turn a blind eye to attacks. Alternatively, if a company knows of a breach, it will find ways to “classify” it in a way that falls into a reporting loophole.
The reporting timelines in the law are arbitrary and not based in the reality of effective incident response. The first hours and days after a breach are integral to the actual incident reporting process, but they are chaotic, and teams are sleep-deprived. Working with lawyers to determine how to report and figuring out the evidence that companies do and don’t want to “see” just makes the process harder.