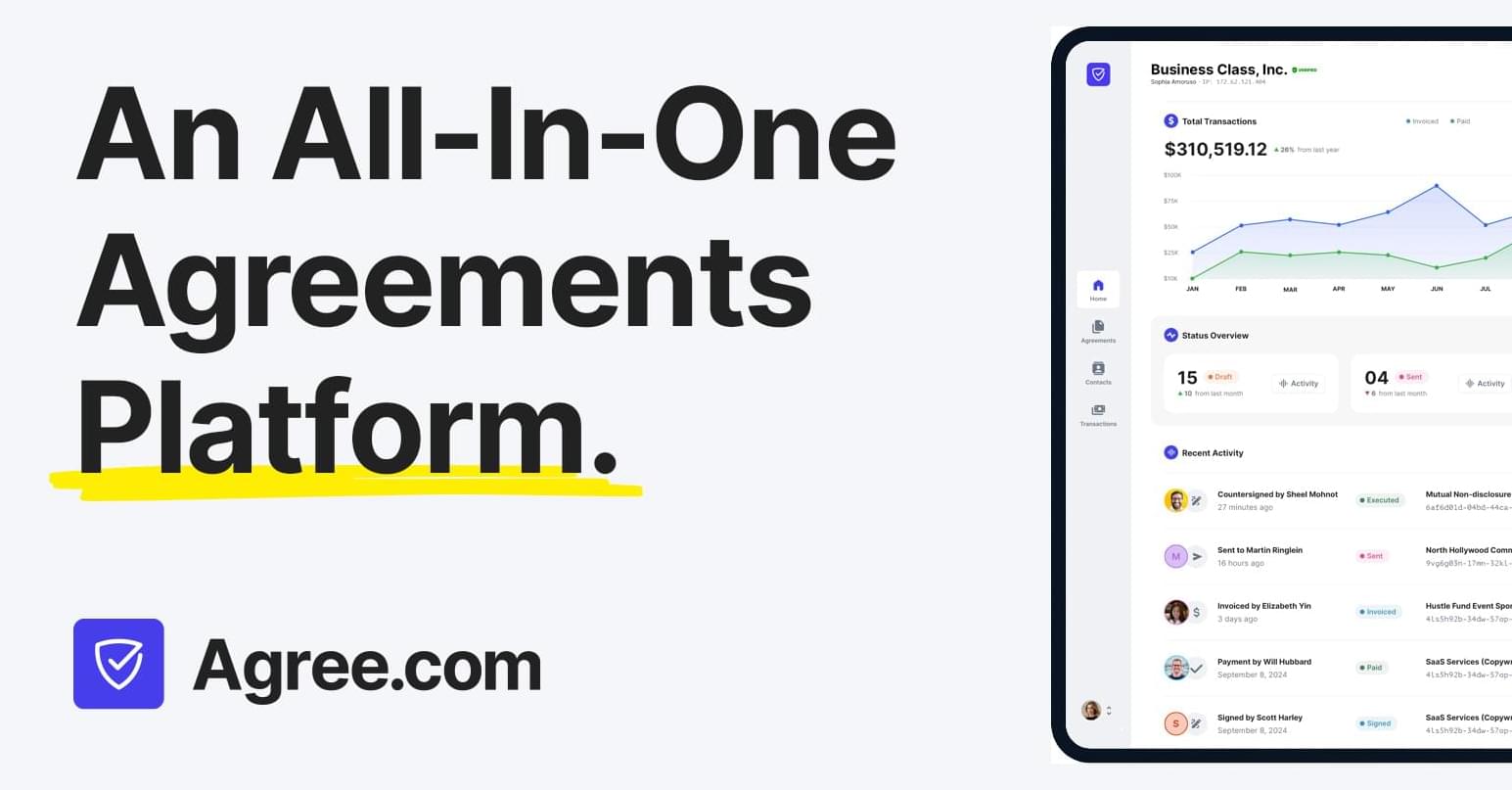
Physicists at University of Miami have created a novel organic molecule that could replace silicon and metal used in computer chip making.


Recent Extinction Rebellion protests saw key sites across London shut down in an attempt to force the government to declare an ‘eco-emergency.’
Our dissatisfaction with breakdown on a global, individual and societal level pushes many of us into activism. Increased numbers of people report suffering from ‘eco-anxiety’, and a recent study showed only 29% of American millennials currently believe that the country is heading in the right direction.
But can decay be completely reversed by human effort?
In this podcast, Tom Cozens speaks with Dr Mark Hocknull, who points out that decay finds its cause in deeper laws governing the physical universe. According to the principle of entropy, breakdown and decay are inescapable aspects of the natural world. The second law of thermodynamics states that decay and disorder are inescapable, and will always increase over time, despite human effort to reverse the process.
In the face of a world inescapably programmed towards breakdown, should we fight back or give up?
Owl in space at https://owlinspace.com
What is time? Speaking time travel, black holes and the remits of science. In this podcast conversation, we speak with Professor David Wilkinson — physicist and author of popular science books on Stephen Hawking to explore the question: can we ever fully understand time through science, or does it open up more mystery?
Owl in space at https://owlinspace.com

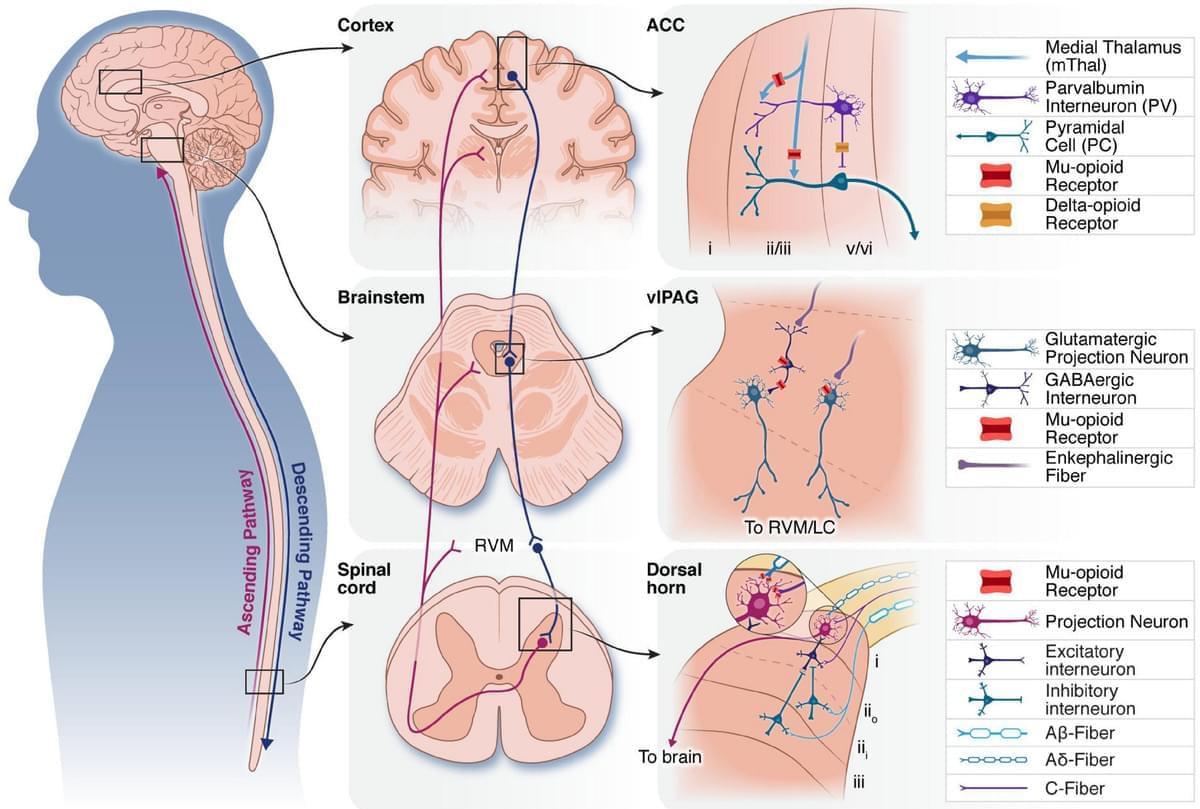
Due to the prevalence of chronic pain worldwide, there is an urgent need to improve pain management strategies. While opioid drugs have long been used to treat chronic pain, their use is severely limited by adverse effects and abuse liability. Neurostimulation techniques have emerged as a promising option for chronic pain that is refractory to other treatments. While different neurostimulation strategies have been applied to many neural structures implicated in pain processing, there is variability in efficacy between patients, underscoring the need to optimize neurostimulation techniques for use in pain management. This optimization requires a deeper understanding of the mechanisms underlying neurostimulation-induced pain relief. Here, we discuss the most commonly used neurostimulation techniques for treating chronic pain. We present evidence that neurostimulation-induced analgesia is in part driven by the release of endogenous opioids and that this endogenous opioid release is a common endpoint between different methods of neurostimulation. Finally, we introduce technological and clinical innovations that are being explored to optimize neurostimulation techniques for the treatment of pain, including multidisciplinary efforts between neuroscience research and clinical treatment that may refine the efficacy of neurostimulation based on its underlying mechanisms.
Over 20% of people worldwide suffer from chronic pain disorders (Goldberg and McGee, 2011). In response to an unmet need for effective pain management, opioid drugs have been widely adopted. Opioid drugs harness the body’s endogenous opioid receptors, which are dispersed throughout the central and peripheral nervous system to modulate pain perception. While prescription opioids often provide effective pain relief, they have undesirable and potentially dangerous side effects including abuse liability and respiratory depression. Their contribution to the ongoing opioid epidemic and the enormous negative impact of chronic pain underscore the need for safe and effective pain therapies (Manchikanti et al., 2012). Neurostimulation therapies are potential alternatives for managing medically refractory pain. However, these therapies are hampered by inconsistent pain relief across patients and diminishing analgesic effects over time (Kumar K. et al., 1998).


How do you distinguish a galaxy from a mere cluster of stars? That’s easy, right? A galaxy is a large collection of millions or billion of stars, while a star cluster only has a thousand or so. Well, that kind of thinking won’t get you a Ph.D. in astronomy! Seriously, though, the line between galaxy and star cluster isn’t always clear. Case in point, UMa3/U1.
It’s easy to distinguish galaxies such as Andromeda and the Milky Way. They are large, gravitationally bound, and dominated by dark matter. It’s also easy to distinguish star clusters such as the Pleiades. They are loosely bound star groupings without dark matter. But for a type of small dwarf galaxy known as Ultra-Faint Dwarfs (UFDs) the dividing line gets fuzzy.
UFDs are dominated by dark matter. The mass of the Milky Way, for example, is about 85% dark matter. An ultrafaint dwarf galaxy, however, can have a thousand times more dark matter than luminous matter. This is why they are so faint. Since UFDs often contain some of the oldest stars in the Universe, astronomers love to study them for clues on the origins of galaxies. Which brings us to UMa3/U1.

Who knew that magnetic fields could be so useful? Astronomers are able to use magnetic fields to map our environment within the Milky Way using a technique called Faraday rotation.
It works like this. There’s a bunch of dust—literal dust grains—floating within the galaxy.
Well, I say there’s a lot of dust, but it’s at very, very low densities. Thankfully, the volumes within interstellar space are so vast that the total amount of dust can really add up. And all these little dust grains have little magnetic fields associated with them, because all the grains are made of electric charges and they’re spinning around themselves.