A lab-made diet sparked a 15-fold boom in bee reproduction, pointing to a possible solution for collapsing colonies.
Get the latest international news and world events from around the world.


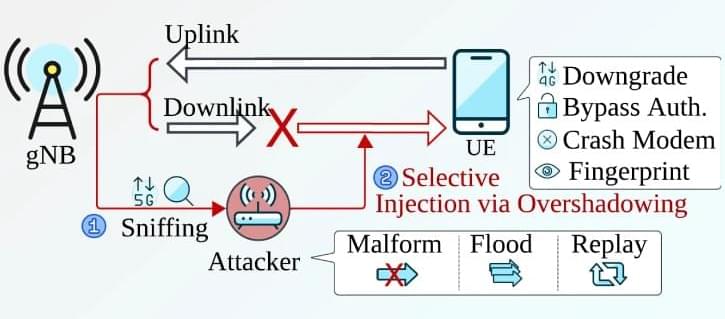
New Sni5Gect Attack Crashes Phones and Downgrades 5G to 4G without Rogue Base Station
“As opposed to using a rogue base station, which limits the practicality of many 5G attacks, SNI5GECT acts as a third-party in the communication, silently sniffs messages, and tracks the protocol state by decoding the sniffed messages during the UE attach procedure,” the researchers said. “The state information is then used to inject a targeted attack payload in downlink communication.”
The findings build upon a prior study from ASSET in late 2023 that led to the discovery of 14 flaws in the firmware implementation of 5G mobile network modems from MediaTek and Qualcomm, collectively dubbed 5Ghoul, that could be exploited to launch attacks to drop connections, freeze the connection that involves manual reboot, or downgrade the 5G connectivity to 4G.
The Sni5Gect attacks are designed to passively sniff messages during the initial connection process, decode the message content in real-time, and then leverage the decoded message content to inject targeted attack payloads.




Google to verify all Android devs to block malware on Google Play
Google is introducing a new defense for Android called ‘Developer Verification’ to block malware installations from sideloaded apps sourced from outside the official Google Play app store.
For apps on Google Play, there was already a requirement for publishers to provide a D-U-N-S (Data Universal Numbering System) number, introduced on August 31, 2023.
Google says this has had a notable effect in reducing malware on the platform. However, the system didn’t apply to the vast developer ecosystem outside the app store.
Silk Typhoon hackers hijack network captive portals in diplomat attacks
State-sponsored hackers linked to the Silk Typhoon activity cluster targeted diplomats by hijacking web traffic to redirect to a malware-serving website.
The hackers used an advanced adversary-in-the-middle (AitM) technique to hijack the captive portal of the network and send the target to the first-stage malware.
Google Threat Intelligence Group (GTIG) tracks the threat actor as UNC6384 and, based on tooling, targeting, and infrastructure, believes it is associated with the Chinese threat actor TEMP.Hex, also known as Mustang Panda and Silk Typhoon.

Nevada closes state offices as cyberattack disrupts IT systems
Nevada remains two days into a cyberattack that began early Sunday, disrupting government websites, phone systems, and online platforms, and forcing all state offices to close on Monday.
The impact of the attack was first felt on Sunday morning, with the Governor’s Technology Office stating that a ‘network issue’ began around 1:52 AM PT, affecting the state’s IT systems.
The Governor’s Technology Office warned that websites, online services, and phone lines could be slow or unavailable as teams worked to restore service.