Electrons can be elusive, but Cornell researchers using a new computational method can now account for where they go—or don’t go—in certain layered materials.
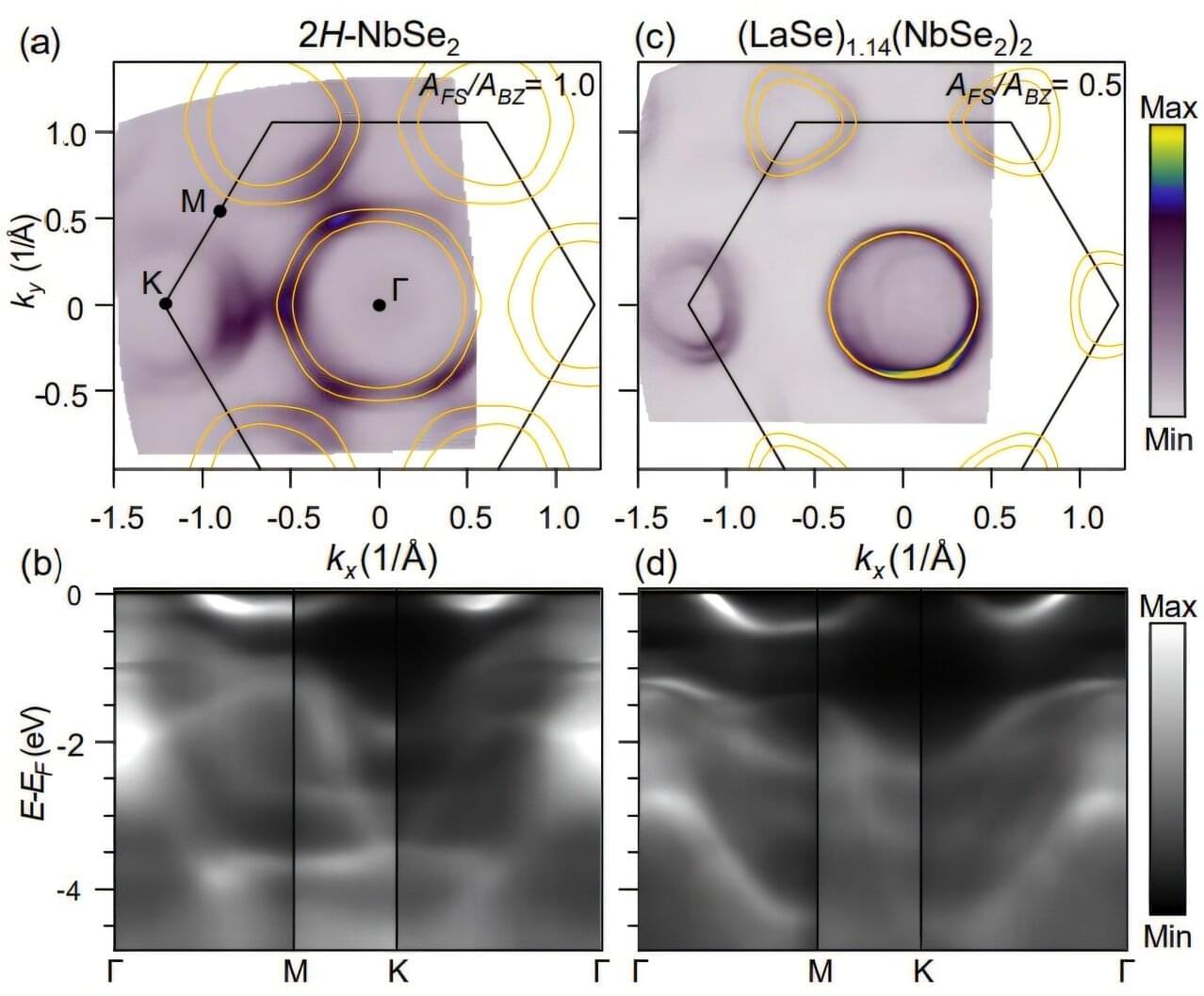
Physics and engineering researchers have confirmed that in certain quantum materials, known as “misfits” because their crystal structures don’t align perfectly—picture LEGOs where one layer has a square grid and the other a hexagonal grid—electrons mostly stay in their home layers.
This discovery, important for designing materials with quantum properties including superconductivity, overturns a long-standing assumption. For years, scientists believed that large shifts in energy bands in certain misfit materials meant electrons were physically moving from one layer to the other. But the Cornell researchers have found that chemical bonding between the mismatched layers causes electrons to rearrange in a way that increases the number of high-energy electrons, while few electrons move from one layer to the other.