He’s just like me, for real.


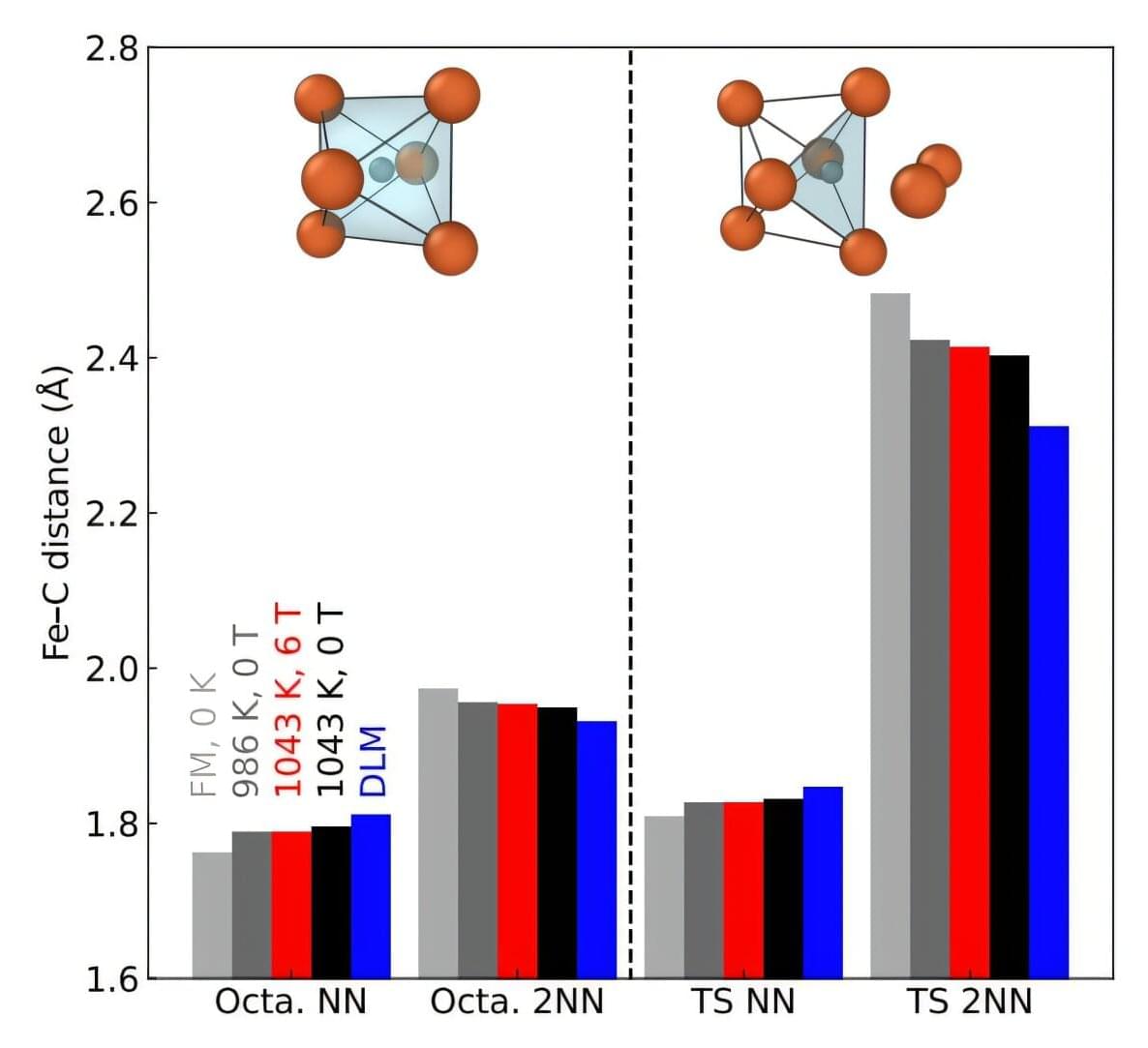
Professor Dallas Trinkle and colleagues have provided the first quantitative explanation for how magnetic fields slow carbon atom movement through iron, a phenomenon first observed in the 1970s but never fully understood. Published in Physical Review Letters, their computer simulations reveal that magnetic field alignment changes the energy barriers between atomic “cages,” offering potential pathways to reduce the energy costs and CO2 emissions associated with steel processing.
An alloy of iron and carbon, steel is one of the most-used building materials on the planet. Engineering its microstructure requires high temperatures; as a result, most steel processing consumes significant energy. In the 1970s, scientists noted that some steels exhibited better properties when heat treated under a magnetic field—but their ideas explaining this behavior were only conceptual. Understanding the mechanism behind this phenomenon could improve engineers’ ability to control heat treatment, improving material processing and potentially lowering energy costs.
“The previous explanations for this behavior were phenomenological at best,” said Trinkle, the Ivan Racheff Professor of Materials Science and Engineering and the senior author of the paper. “When you’re designing a material, you need to be able to say, ‘If I add this element, this is how (the material) will change.’ And we had no understanding of how this was happening; there was nothing predictive about it.”



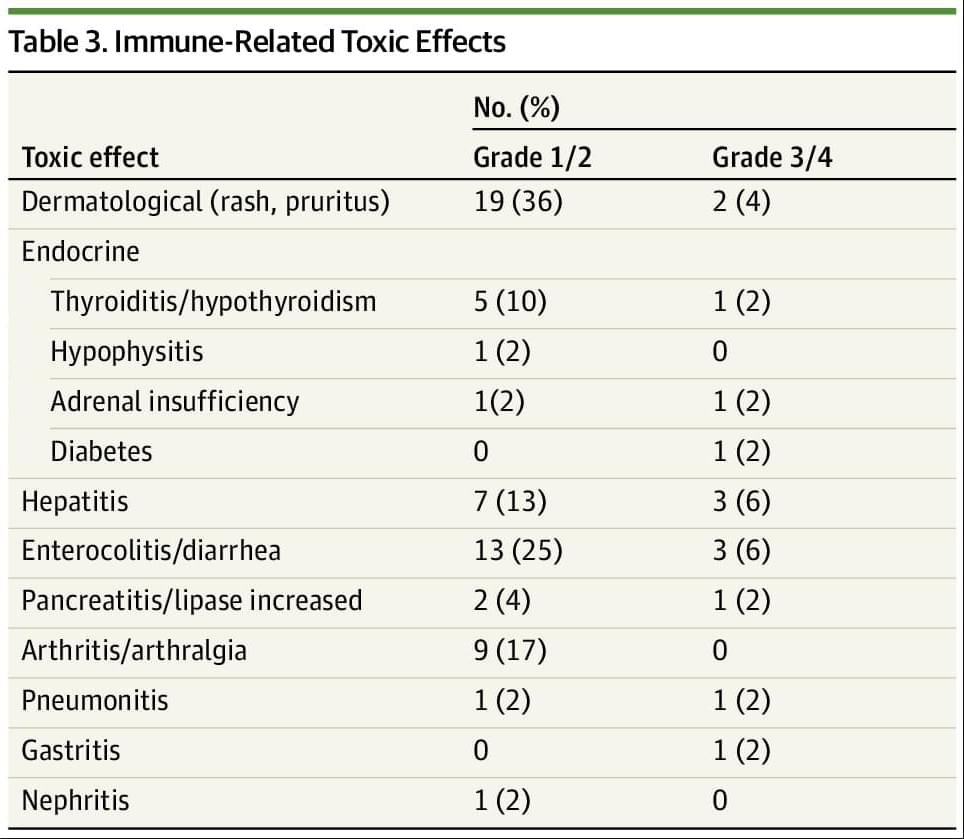
In a nonrandomized phase 2 trial of adults with advanced dMMR/MSI-H noncolorectal cancers, combined nivolumab/ipilimumab showed an objective response rate of 63% and 6-month progression-free survival rate of 71%.
Main Outcomes and Measures The co-primary end points were objective response rate (ORR) and 6-month progression-free survival (6-PFS) as assessed by Response Evaluation Criteria in Solid Tumors (RECIST) version 1.1, with the secondary end points being median overall survival (mOS), progression-free survival (PFS), and treatment-related toxic effects.
Results Overall, 52 participants were included. The median (range) age of participants was 62 (29−84) years; 41 (79%) were female individuals and 11 (21%) were male individuals. Overall, 52 patients representing 17 tumor types were enrolled, with the most common tumor type being endometrial cancer (26 [50%]). Twenty-seven patients (52%) were pretreated for metastatic disease. ORR was 63% (95% CI, 50% to 75%) with the median duration of response not being reached and 79% of responses being ongoing. The median PFS and OS have not been reached and the 6-month PFS was 71% (95% CI, 57%-81%). Overall, 12 patients (23%) experienced a grade 3/4 immune-related adverse event.
Conclusions and Relevance This nonrandomized clinical trial found that combined anti–PD-1/CTLA-4 blockade was associated with a high rate of durable responses in dMMR/MSI-H noncolorectal cancers, comparing favorably to published trials using anti–PD-1/programmed cell death ligand 1 monotherapy. Anti–PD-1/CTLA-4 blockade using nivolumab and ipilimumab may represent an alternative treatment option to monotherapy in this patient population.


Despite its diminutive size, the organ packs almost 500 feet of wiring and 54.5 million synapses into the size of a grain of sand — an astonishing feat of computational neurology research that allows scientists to better understand how signals travel throughout the brain.
And thanks to significant advances of some of the world’s most capable supercomputers, researchers at the Jülich Research Centre in Germany are now aiming their sights at a far more ambitious goal: a simulation at the scale of the entire human brain.
Previous attempts, dating back a decade, like the Human Brain Project, fell largely flat, despite considerable government funding. But as New Scientist reports, the Jülich researchers think they can push things forward. The idea is to bring together several models of smaller regions of the brain with a supercomputer to run simulations of billions of firing neurons.
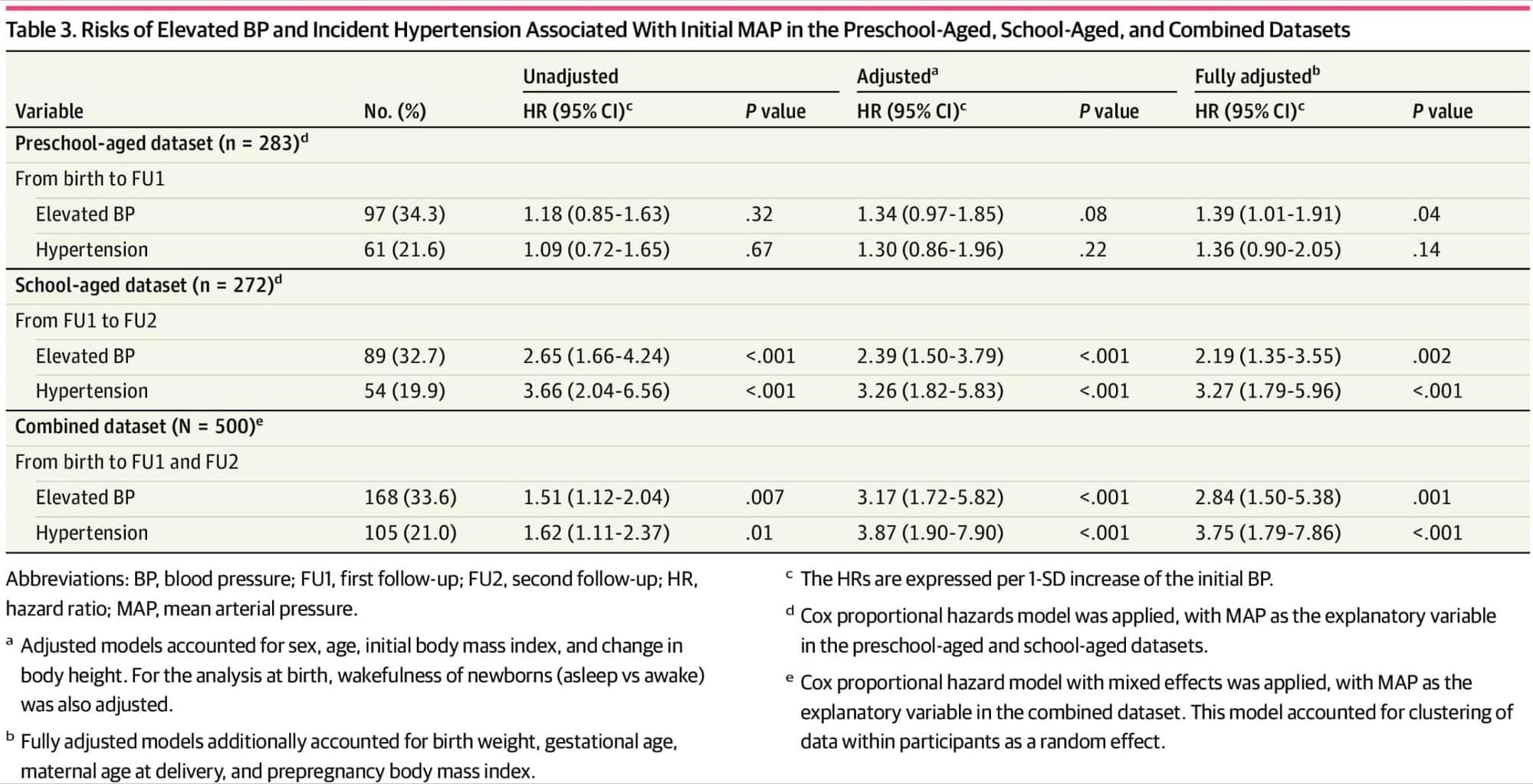
Higher blood pressure at birth and childhood was associated with a higher risk of hypertension later in life in this ENVIRONAGE study, which tracked BP from birth through childhood.
Question Is blood pressure (BP) at birth and in early childhood associated with BP in later childhood?
Findings In this cohort study of 500 children with BP measured at birth, preschool age (4−6 years), and school age (9−11 years), BP tracked over time. The risk of elevated BP and hypertension at preschool age and school age was associated with BP levels at birth and early childhood.