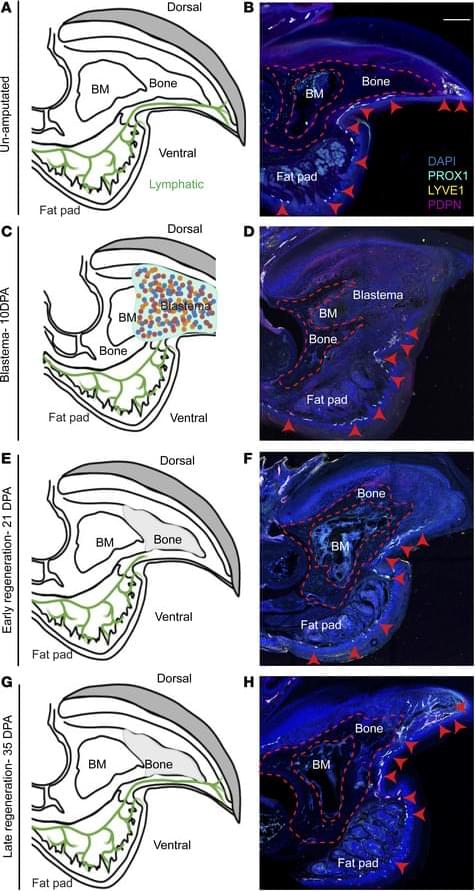
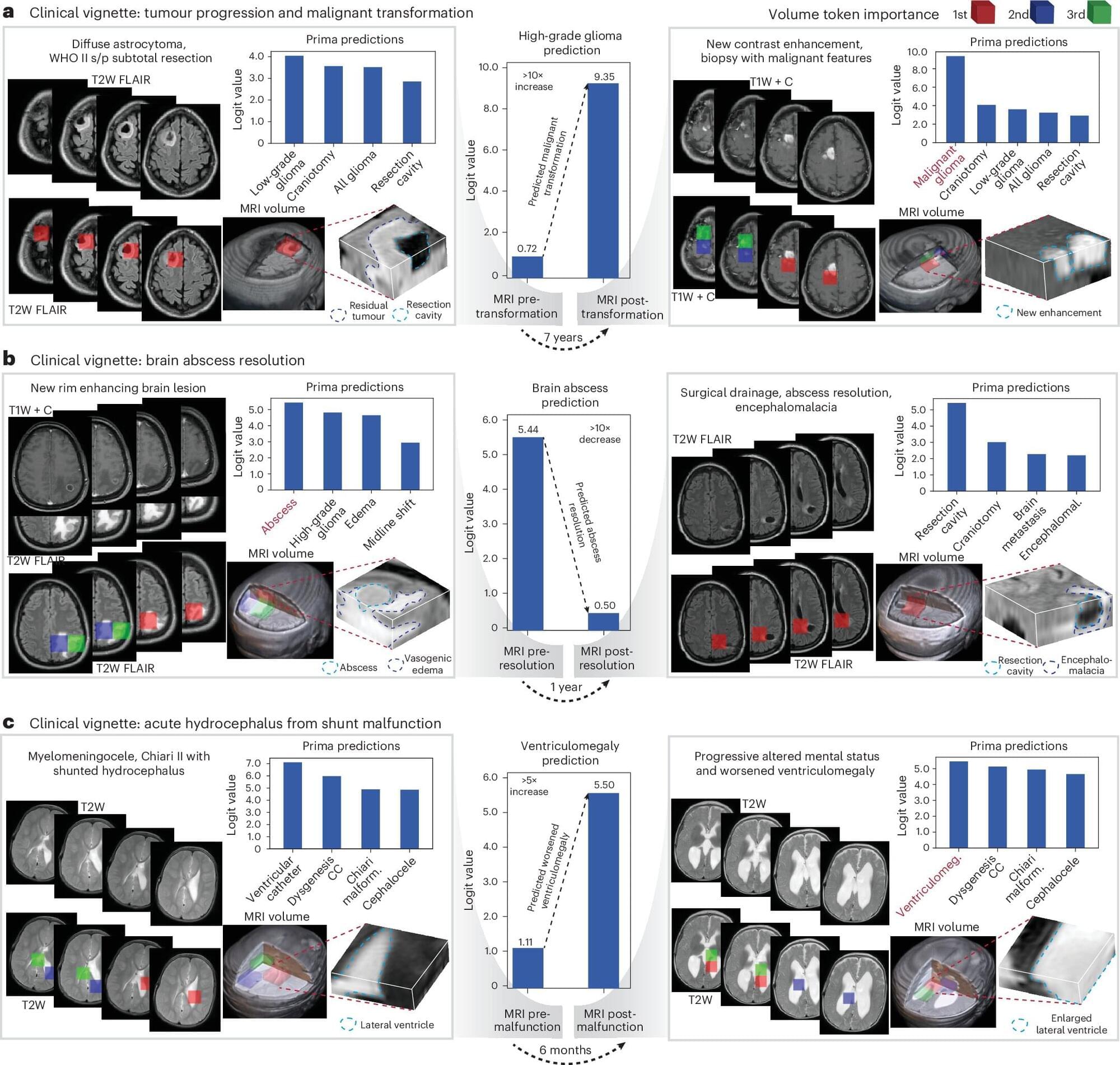
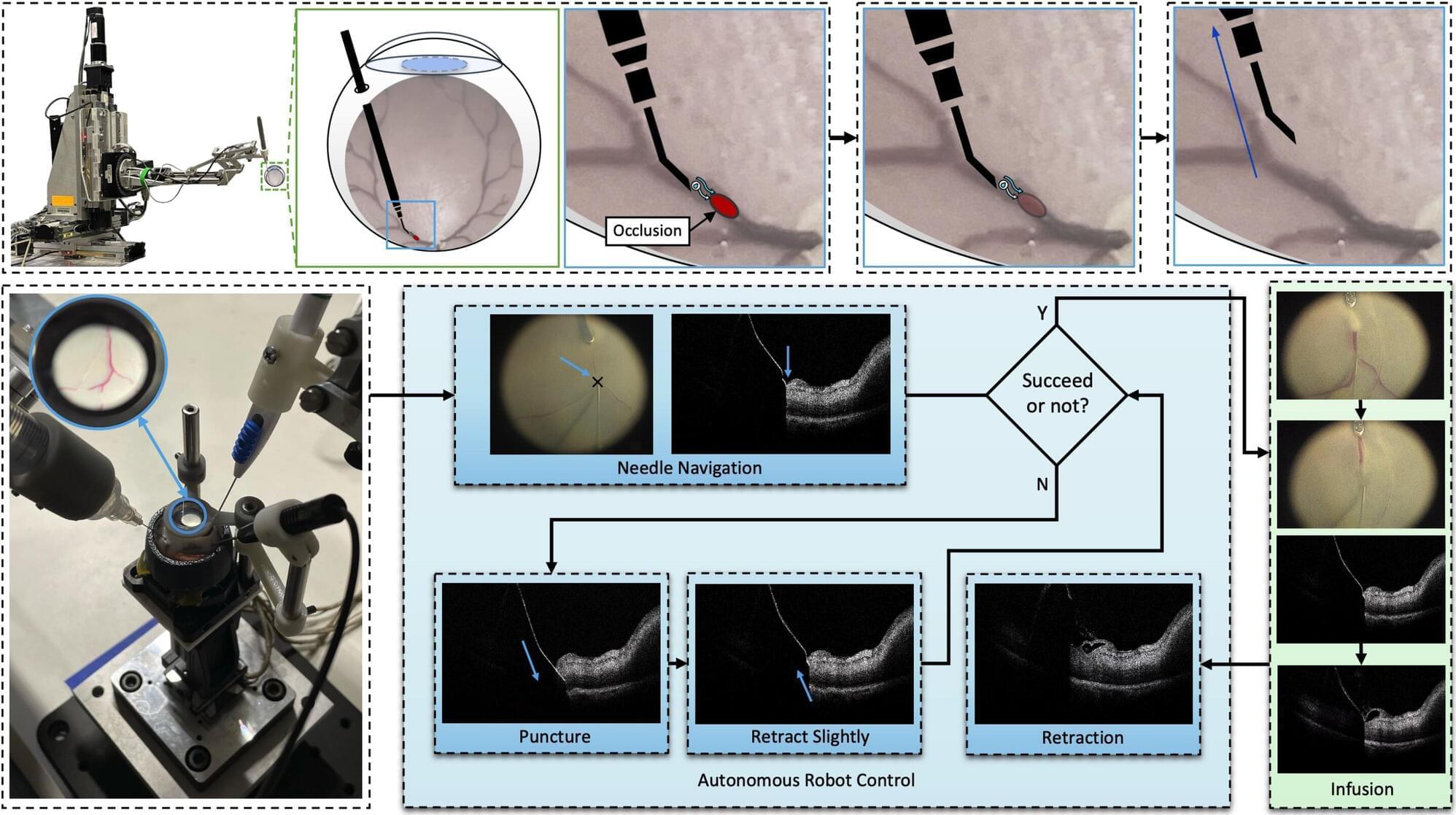
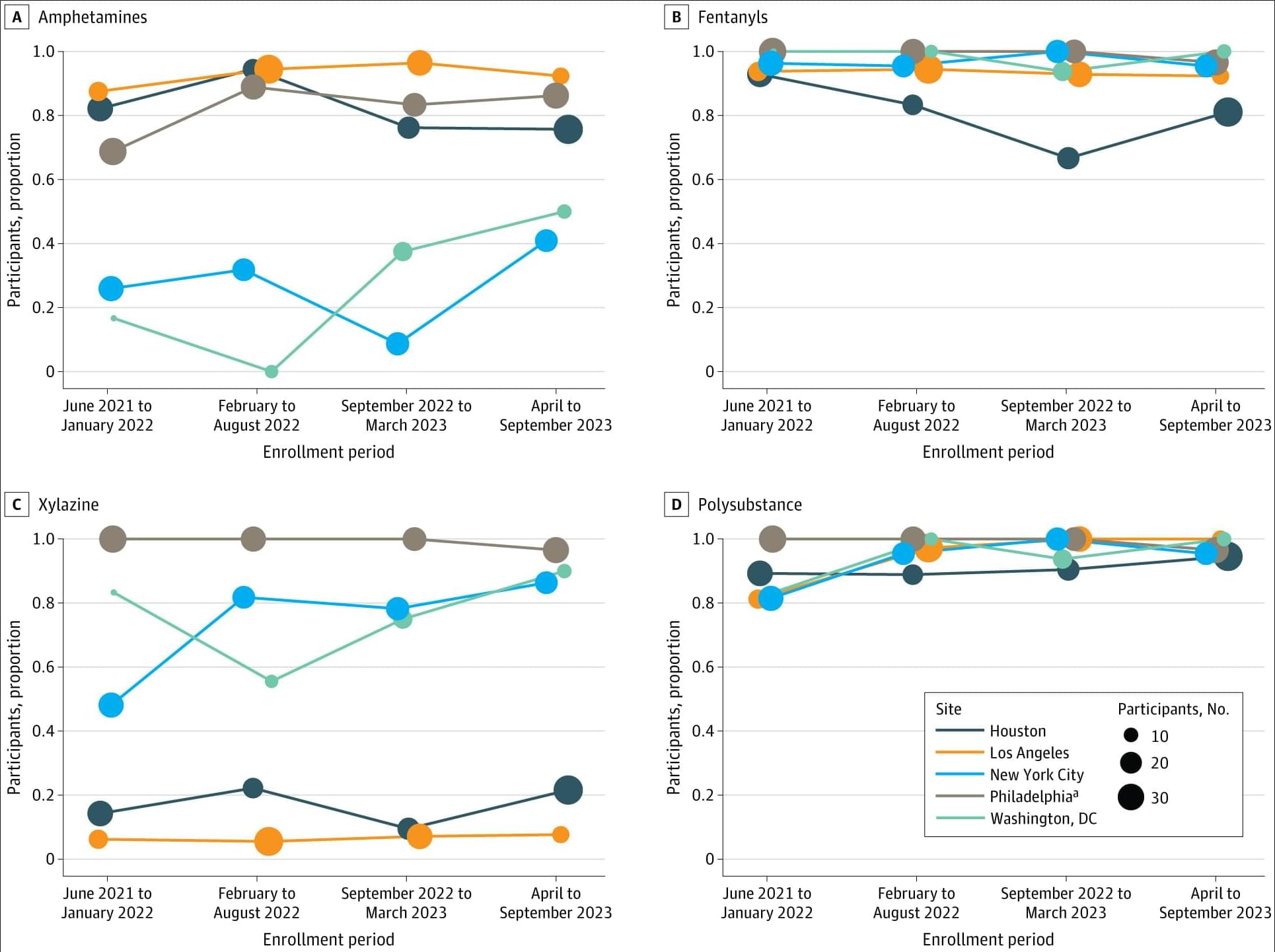
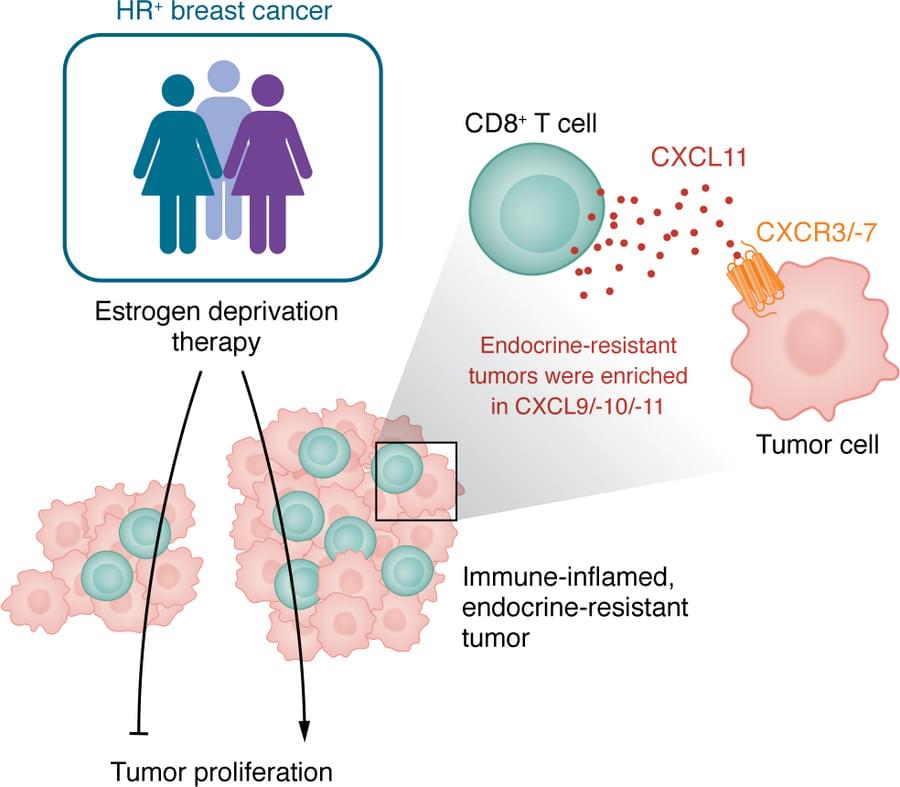
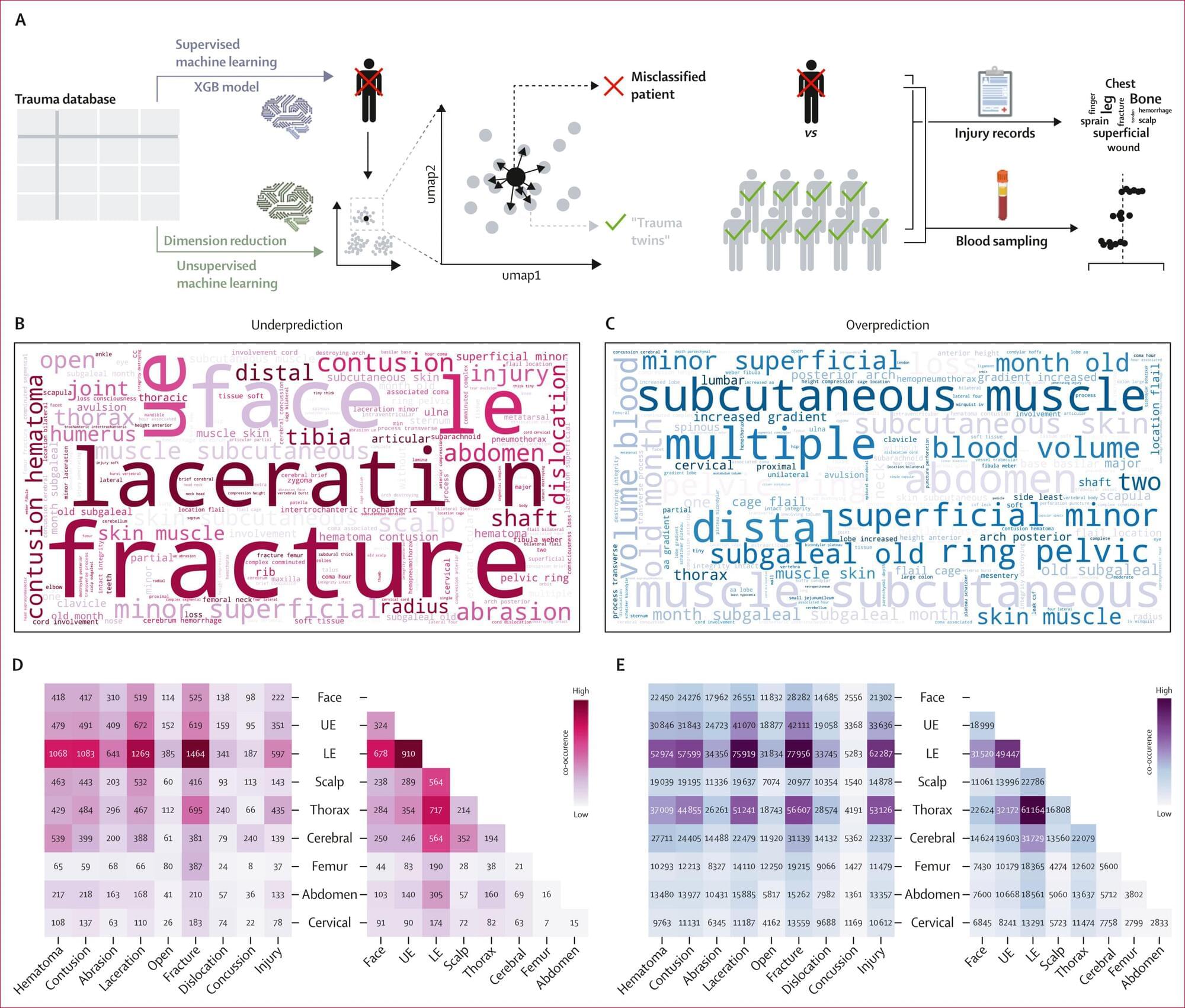
Matthijs Luxen et al. comment on Neda Vishlaghi et al.: https://doi.org/10.1172/JCI201199
Address correspondence to: Benjamin Levi, Department of Surgery, University of Texas Southwestern, 6,000 Harry Hines Blvd., Dallas, Texas 75,235, USA. Phone: 214.648.9017; Email: Benjamin. [email protected].
Find articles by Vishlaghi, N. in: | Google Scholar
1Department of Surgery, University of Texas Southwestern Medical Center, Dallas, Texas, USA.