For quantum computers to outperform their classical counterparts, they need more quantum bits, or qubits. State-of-the-art quantum computers have around 1,000 qubits. Columbia physicists Sebastian Will and Nanfang Yu have their sights set much higher.
“We are laying critical groundwork to enable quantum computers with more than 100,000 qubits,” Will said.
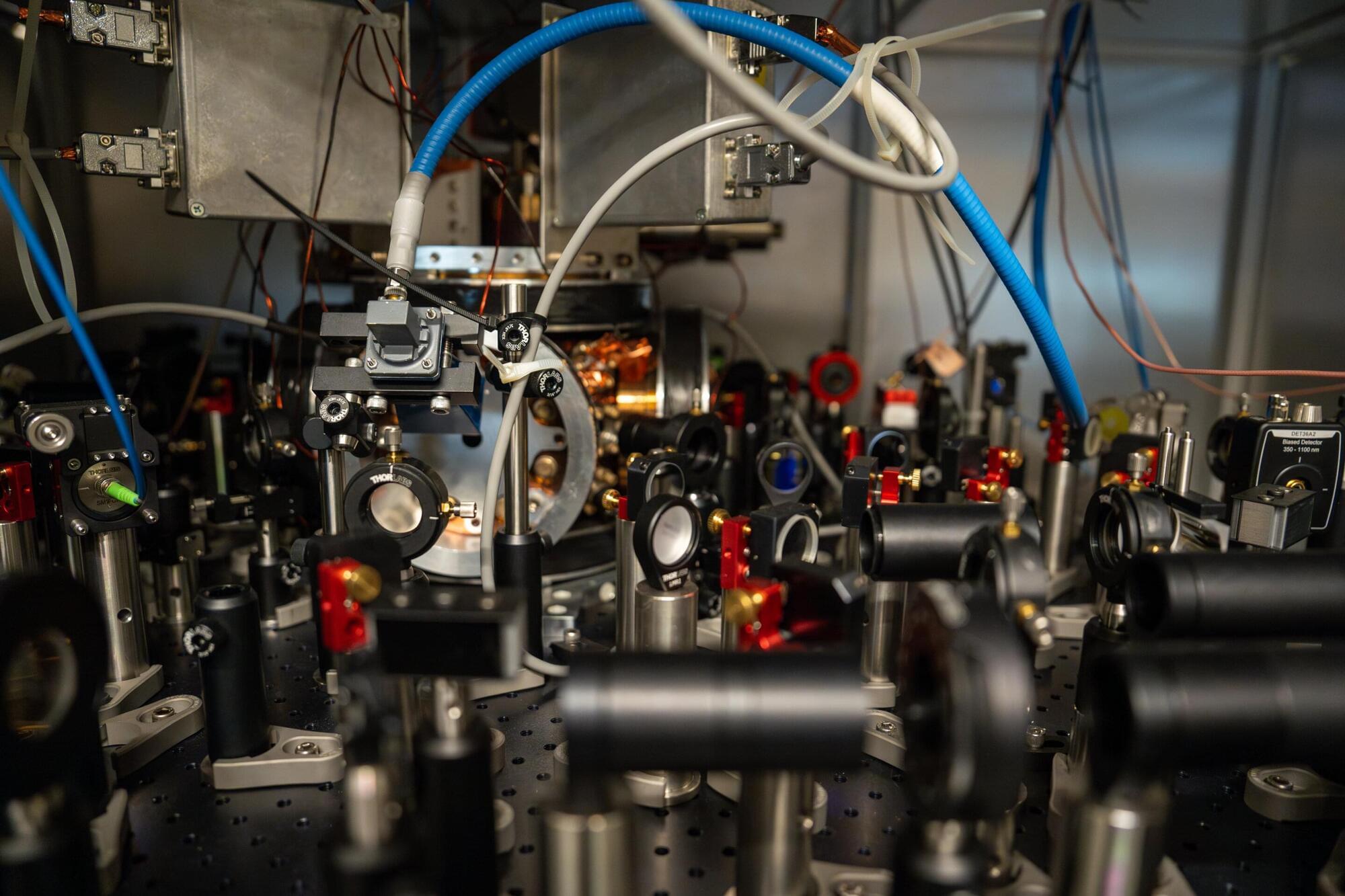
In a paper published in Nature, Will, Yu, and their colleagues combine two powerful technologies— optical tweezers and metasurfaces—to dramatically scale the size of neutral-atom arrays.