Page 3839
Jun 30, 2022
Graphene-like structure created from a fullerene
Posted by Shubham Ghosh Roy in category: materials
Jun 30, 2022
AI Is Learning Twice as Fast This Year Than Last
Posted by Shubham Ghosh Roy in category: robotics/AI
According to the best measures we’ve got, a set of benchmarks called MLPerf, machine learning systems can be trained nearly twice as quickly they could last year. It’s a figure that outstrips Moore’s Law by quite a ways.
Jun 30, 2022
Google Blocks Dozens of Malicious Domains Operated
Posted by Saúl Morales Rodriguéz in category: cybercrime/malcode
Google’s Threat Analysis Group (TAG) blocks as many as 36 malicious domains operated by hack-for-hire groups from India, Russia and UAE.
Shadow IT refers to the practice of users deploying unauthorized technology resources in order to circumvent their IT department.
Jun 30, 2022
What is Shadow IT and why is it so risky?
Posted by Saúl Morales Rodriguéz in categories: internet, security
Shadow IT refers to the practice of users deploying unauthorized technology resources in order to circumvent their IT department. Users may resort to using shadow IT practices when they feel that existing IT policies are too restrictive or get in the way of them being able to do their jobs effectively.
An old school phenomenon
Shadow IT is not new. There have been countless examples of widespread shadow IT use over the years. In the early 2000s, for example, many organizations were reluctant to adopt Wi-Fi for fear that it could undermine their security efforts. However, users wanted the convenience of wireless device usage and often deployed wireless access points without the IT department’s knowledge or consent.
Jun 30, 2022
Ex-Canadian Government Employee Pleads Guilty Over NetWalker Ransomware Attacks
Posted by Saúl Morales Rodriguéz in categories: cybercrime/malcode, government
A former Canadian government employee pleaded guilty in the U.S. to charges related to his involvement with the NetWalker ransomware syndicate.
Jun 30, 2022
New YTStealer Malware Aims to Hijack Accounts of YouTube Content Creators
Posted by Saúl Morales Rodriguéz in category: cybercrime/malcode
Researchers are warning about a new YouTube hijacking malware, dubbed YTStealer, believed to be sold as a service on the dark web.
Jun 30, 2022
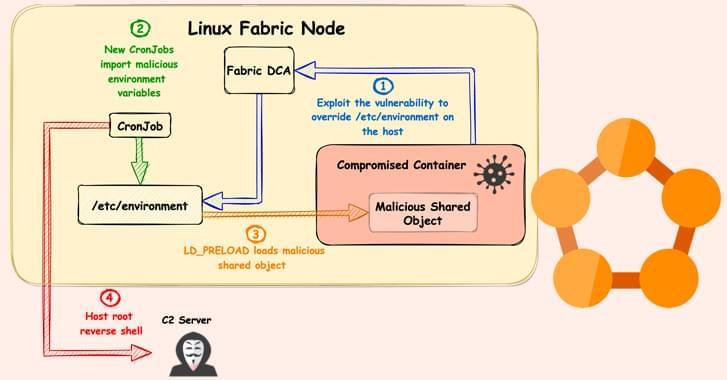
New ‘FabricScape’ Bug in Microsoft Azure Service Fabric Impacts Linux Workloads
Posted by Saúl Morales Rodriguéz in category: computing
Researchers reveal details about a new vulnerability in Microsoft’s Service Fabric that could be exploited to gain elevated privileges on Linux.
Jun 30, 2022
CISA Warns of Active Exploitation of ‘PwnKit’ Linux Vulnerability in the Wild
Posted by Saúl Morales Rodriguéz in category: cybercrime/malcode
U.S. cybersecurity agency CISA has added the PwnKit Linux vulnerability to its catalog of known exploited vulnerabilities.
Jun 30, 2022
Better, Stronger, Faster: The Future of the Bionic Body
Posted by Dan Breeden in categories: biotech/medical, chemistry, cyborgs, engineering, mobile phones, neuroscience, transhumanism

In the future, a woman with a spinal cord injury could make a full recovery; a baby with a weak heart could pump his own blood. How close are we today to the bold promise of bionics—and could this technology be used to improve normal human functions, as well as to repair us? Join Bill Blakemore, John Donoghue, Jennifer French, Joseph J. Fins, and P. Hunter Peckham at “Better, Stronger, Faster,” part of the Big Ideas Series, as they explore the unfolding future of embedded technology.
This program is part of the Big Ideas Series, made possible with support from the John Templeton Foundation.
Continue reading “Better, Stronger, Faster: The Future of the Bionic Body” »