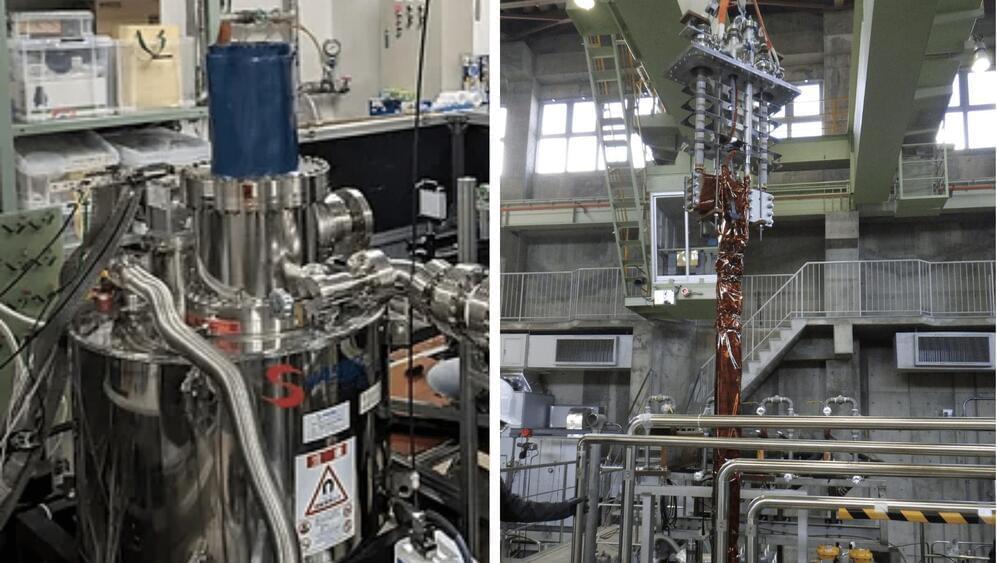
Physicists Successfully Demonstrate Quantum Energy Teleportation in Lab Experiments
TL;DR
Bob finds himself in need of energy — he wants to charge that fanciful quantum battery — but all he has access to is empty space. Fortunately, his friend Alice has a fully equipped physics lab in a far-off location. Alice measures the field in her lab, injecting energy into it there and learning about its fluctuations. This experiment bumps the overall field out of the ground state, but as far as Bob can tell, his vacuum remains in the minimum-energy state, randomly fluctuating. But then Alice texts Bob her findings about the vacuum around her location, essentially telling Bob when to plug in his battery. After Bob reads her message, he can use the newfound knowledge to prepare an experiment that extracts energy from the vacuum — up to the amount injected by Alice.