That’s not just cool. It’s ultracool.


US researchers send quantum entangled signal over commercial fiber optic network without requiring any downtime, a major achievement.



A $7 billion all-electric light rail project is underway in the Capital City. The Austin Light Rail now has a team in place to build the city’s first light rail system, set to shakeup the city’s public transportation in the near future.
Last month, the Austin Transit Partnership selected AECOM, a Dallas-based infrastructure consulting firm, to bring the first phase of the approximately 10-mile light rail to life in Austin, according to a release. Now AECOM is preparing to offer more updates to public on the project’s progress as the organization continues to implement the plan.
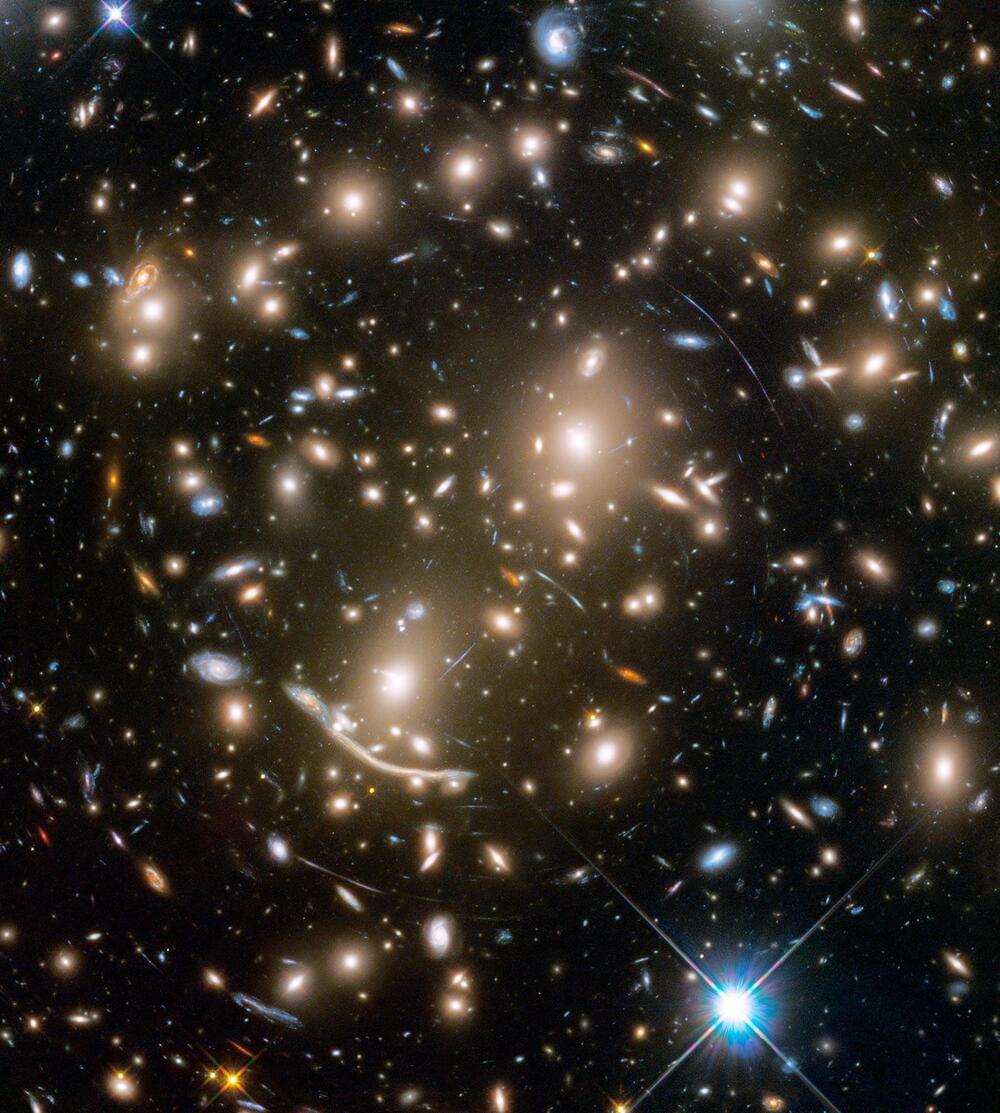
In an astronomical feat, using NASA
NASA, the National Aeronautics and Space Administration, is the United States government agency responsible for the nation’s civilian space program and for aeronautics and aerospace research. Established in 1958 by the National Aeronautics and Space Act, NASA has led the U.S. in space exploration efforts, including the Apollo moon-landing missions, the Skylab space station, and the Space Shuttle program.


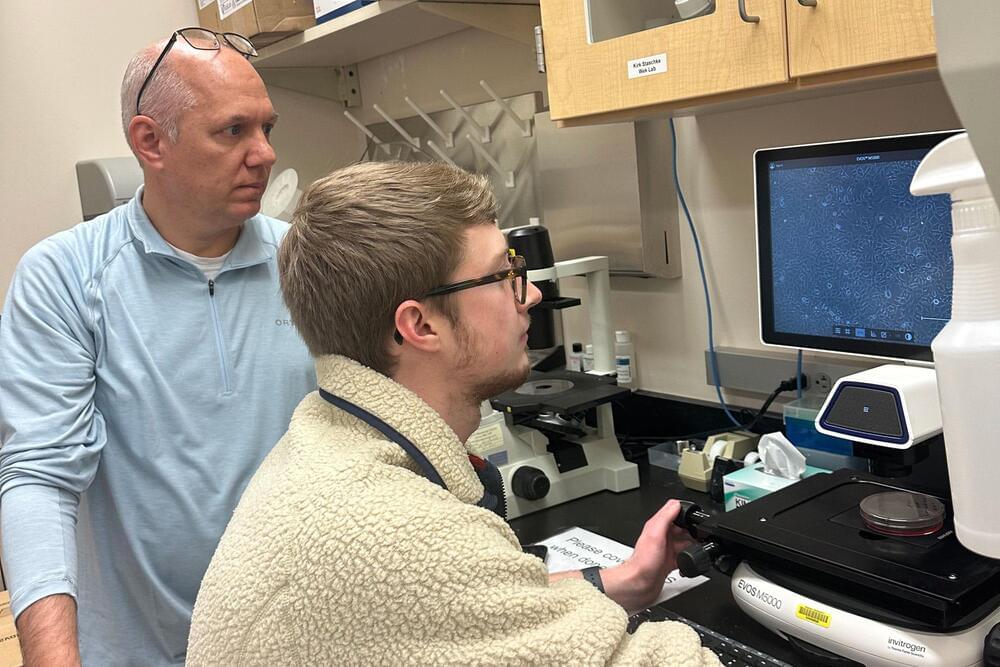
New research by a team of Indiana University School of Medicine scientists and their collaborators has uncovered a novel vulnerability in prostate cancer animal models that starves prostate tumors of critical nutrients and stunts their growth, which could lead to the development of new treatments for the deadly disease.
Led by IU School of Medicine’s Kirk Staschke, Ph.D., assistant research professor of biochemistry and molecular biology, and Ronald C. Wek, Ph.D., Showalter Professor of Biochemistry, the study was recently published in Science Signaling.
Prostate cancer is a leading cause of cancer deaths in American men. Current treatments target the hormone testosterone, which prostate cancer cells need to grow. Unfortunately, prostate tumors frequently become resistant to these treatments, leaving doctors with few options to stop the disease.