On May 7, 2025, the Sun erupted in a massive display of energy, releasing a solar filament that stretched across its eastern limb.




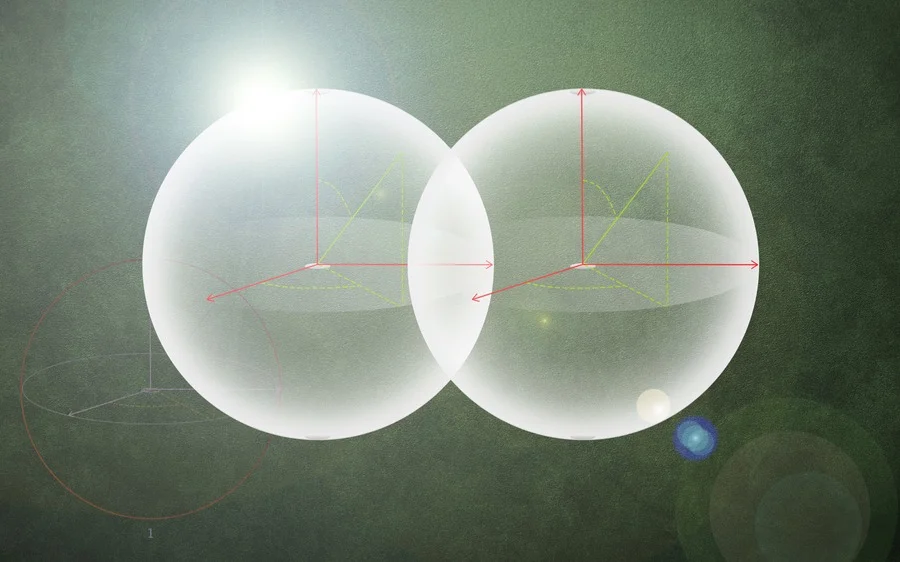
Repulsive gravity at the quantum scale would have flattened out inhomogeneities in the early universe.
In classical physics, gravity is universally attractive. At the quantum level, however, this may not always be the case. If vast quantities of matter are present within an infinitesimally small volume – at the centre of a black hole, for example, or during the very earliest moments of the universe – spacetime becomes curved at scales that approach the Planck length. This is the fundamental quantum unit of distance, and is around 1020 times smaller than a proton.
In these extremely curved regions, the classical theory of gravity – Einstein’s general theory of relativity – breaks down. However, research on loop quantum cosmology offers a possible solution. It suggests that gravity, in effect, becomes repulsive. Consequently, loop quantum cosmology predicts that our present universe began in a so-called “cosmic bounce”, rather than the Big Bang singularity predicted by general relativity.

China’s Origin Quantum has launched its fourth-generation quantum control system, a move signaling the country’s increasing push to industrialize and scale quantum computing capabilities.
The new system, dubbed Origin Tianji 4.0, supports over 500 qubits and serves as the central control for superconducting quantum computers, according to The Global Times, a media outlet under the Chinese Communist Party (CCP). The system, unveiled this week in Hefei, is positioned as a critical enabler for mass-producing quantum computers with more than 100 qubits.
The control system is considered the “neural center” of a quantum computer. It generates, acquires and controls the precise signals that manage quantum chips, which are the computational heart of a quantum system. With the Tianji 4.0 upgrade, Origin Quantum claims major improvements in integration, automation and scalability compared to its previous version, which powered the country’s third-generation superconducting quantum computer, Origin Wukong.
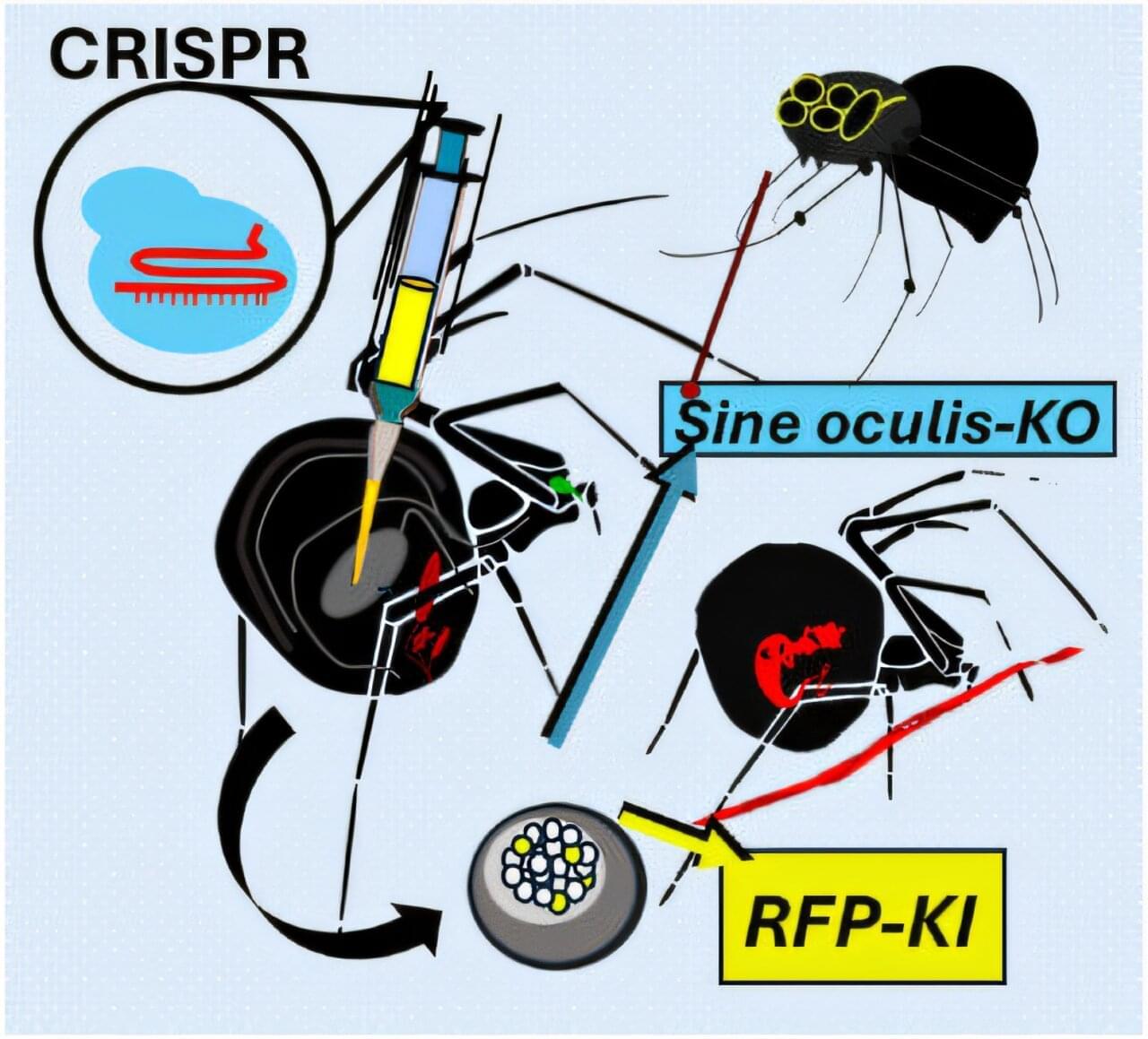
The University of Bayreuth’s Biomaterials research group has, for the first time, successfully applied the CRISPR-Cas9 gene-editing tool to spiders. Following the genetic modification, the spiders produced red fluorescent silk.
The findings of the study have been published in the journal Angewandte Chemie.
Spider silk is one of the most fascinating fibers in the field of materials science. In particular, its dragline thread is extremely tear-resistant, while also being elastic, lightweight and biodegradable. If scientists succeed in influencing spider silk production in vivo—in a living animal—and thereby gain insights into the structure of the dragline thread, it could pave the way for the development of new silk functionalities for a wide range of applications.
A Scientific dive into Depression and Anxiety.
In this video, we explore how depression affects the brain and uncover the science behind brain depression and anxiety. Backed by neuroscience and psychology, this deep dive reveals how depression rewires three major areas of your brain: the prefrontal cortex, hippocampus, and amygdala—and how these changes impact memory, mood, and decision-making.
If you’ve ever wondered what part of the brain is affected by depression, or how anxiety and depression are connected, this video explains it all—clearly and scientifically.
🌿 Why Watch This Video?
✔️ Understand the brain science behind depression.
✔️ Learn how depression and anxiety alter brain structure and function.
✔️ Discover healing methods like neuroplasticity, exercise, and therapy.
✔️ Boost your awareness of mental health and self-healing strategies.
📌 What You’ll Learn:
🔹 How the amygdala becomes overactive during depression.
🔹 Why the hippocampus shrinks, leading to memory loss.
🔹 How the prefrontal cortex struggles with focus and planning.
🔹 Ways to rewire your brain for emotional resilience.
📌 Timestamps:
00:00 – The Science of Depression 🧠
00:45 – How Depression Affects Decision-Making.
02:17 – Memory Loss & Brain Fog Explained.
04:03 – Anxiety & The Overactive Amygdala.
05:49 – How to Heal Your Brain Naturally.
💡 If this video helped you, drop a “🧠” in the comments & share with someone who needs it!

An annual blood test could prevent around half of cancer cases from reaching an advanced stage, new research suggests.
Scientists are currently trying to determine the effectiveness of simple blood tests in detecting cancer before symptoms appear, and whether such early detection improves survival rates.
The NHS is currently trialling such tests, including the Galleri test and miONCO-Dx test, with experts predicting a nationwide rollout of a universal cancer screening program within the next decade.
Leading physicist Raphael Bousso joins Brian Greene to explore the almost unreasonable capacity of our theories of gravity to give deep insights into quantum physics.
This program is part of the Big Ideas series, supported by the John Templeton Foundation.
Participant: Raphael Bousso.
Moderator: Brian Greene.
0:00:00 — Introduction.
00:01:12 Are there any cracks in Quantum Mechanics?
00:03:18 Bousso’s Case for Measurement-Driven Physics.
00:06:00 Does Quantum Mechanics Describe Reality?
00:09:37 How Decoherence Hides Quantum Weirdness.
00:15:05 Difference between Quantum and Classical Mechanics.
00:17:50 What Would Einstein Think of Modern Quantum Theory?
00:21:19 Entanglement’s Place in the Weird World of Quantum Theory.
00:26:45 Bousso’s Intuition for How Entanglement Works.
00:29:12 Einstein’s EPR Worries — What Do We Make of Them Now?
00:33:22 What Is a Singularity in a Black Hole?
00:38:06 How Oppenheimer and Snyder Modeled a Collapsing Star.
00:44:27 Insights Into Hawking Radiation — When Black Holes Began to Evaporate.
00:55:24 Gravity’s Quantum Secrets.
01:01:16 What Does Holography Say About Reality?
01:04:28 Rethinking How We Talk About Unification.
01:08:48 Bousso & Wall: The Quantum Focusing Conjecture.
01:14:33 From Theory to Test: Holography Gets Real.
01:19:34 The Value of String Theory Beyond Being ‘Right’
01:22:06 Penrose and the Proof That Singularities Are Real.
01:28:02 Hawking’s Theorem and the Rise of Singularities.
01:32:41 Is Gravity the Missing Piece in Quantum Theory?
01:39:07 How Bousso and Polchinski Rethought the Cosmological Constant.
01:51:10 Will the Universe Ever Give Up This Secret?
01:53:31 Credits.
VISIT our Website: http://www.worldsciencefestival.com.
FOLLOW us on Social Media:
Facebook: / worldsciencefestival.
Twitter: / worldscifest.
Instagram: / worldscifest.
TikTok: / worldscifest.
LinkedIn: / world-science-festival.
#worldsciencefestival #briangreene #gravity #astrophysics #quantumgravity #quantumphysics