https://paper.li/e-1437691924#/
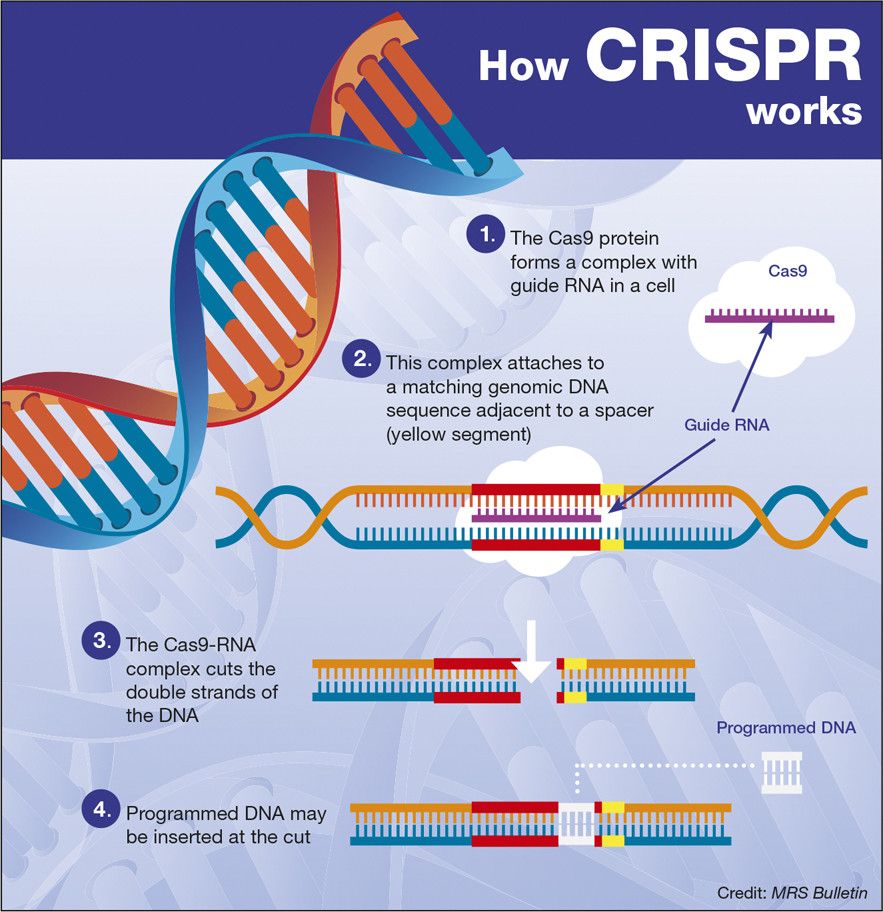
In a newly released report, an influential UK ethics council concludes that editing human embryos is “morally permissible.”

https://paper.li/e-1437691924#/
In a newly released report, an influential UK ethics council concludes that editing human embryos is “morally permissible.”

But even though money is necessary, it’s not sufficient to provide human beings a sense of satisfaction, Obama cautioned. As more and more tasks and services become automated with the rise of artificial intelligence, “that’s going to make the job of giving everybody work that is meaningful tougher, and we’re going to have to be more imaginative, and the pace of change is going to require us to do more fundamental re-imagining of our social and political arrangements, to protect the economic security and the dignity that comes with a job.”
The former president says “we’re going to have to consider new ways of thinking” as technology threatens current labor markets.

Cancer and rodent studies were on the crew’s timeline today to help doctors and scientists improve the health of humans in space and on Earth. The crew also conducted an emergency drill aboard the International Space Station.
Flight Engineer Serena Auñón-Chancellor examined endothelial cells through a microscope for the AngieX Cancer Therapy study. The new cancer research seeks to test a safer, more effective treatment that targets tumor cells and blood vessels. Commander Drew Feustel partnered with astronaut Alexander Gerst and checked on mice being observed for the Rodent Research-7 (RR-7) experiment. RR-7 is exploring how microgravity impacts microbes living inside organisms.
Astronaut Ricky Arnold and Gerst collected and stowed their blood samples for a pair of ongoing human research studies. Arnold went on to work a series of student investigations dubbed NanoRacks Module-9 exploring a variety of topics including botany, biology and physics.
Mankind is about to get closer to the sun than ever before.
Jupiter already had the most moons in the solar system — but they just found another dozen.
This Blue Origin rocket went higher than any previous rocket launched by Jeff Bezos’s company.
Our Fast Lightweight Autonomy program recently completed Phase 2 flight tests, demonstrating advanced algorithms designed to turn small air and ground systems into team members that can autonomously perform tasks dangerous for humans — such as pre-mission reconnaissance in a hostile urban setting or searching damaged structures for survivors following an earthquake.

Friends, I’m super excited to announce I’m launching a new #transhumanism column at The Maven, a new site out that features leaders in their field writing about their lives and activities. My column (or channel as The Maven editors call them) is titled: Transhumanist Wager. And I’ll be posting every day on it, often with original stories. Here’s my first one, just out! Give it a read!
Transhumanism—the social movement of merging people with machines & synthetic parts—is turning dangerously hard left.

“Will machines replace humans?” This question is on the mind of anyone with a job to lose. Daniel Susskind confronts this question and three misconceptions we have about our automated future, suggesting we ask something else: How will we distribute wealth in a world when there will be less — or even no — work?