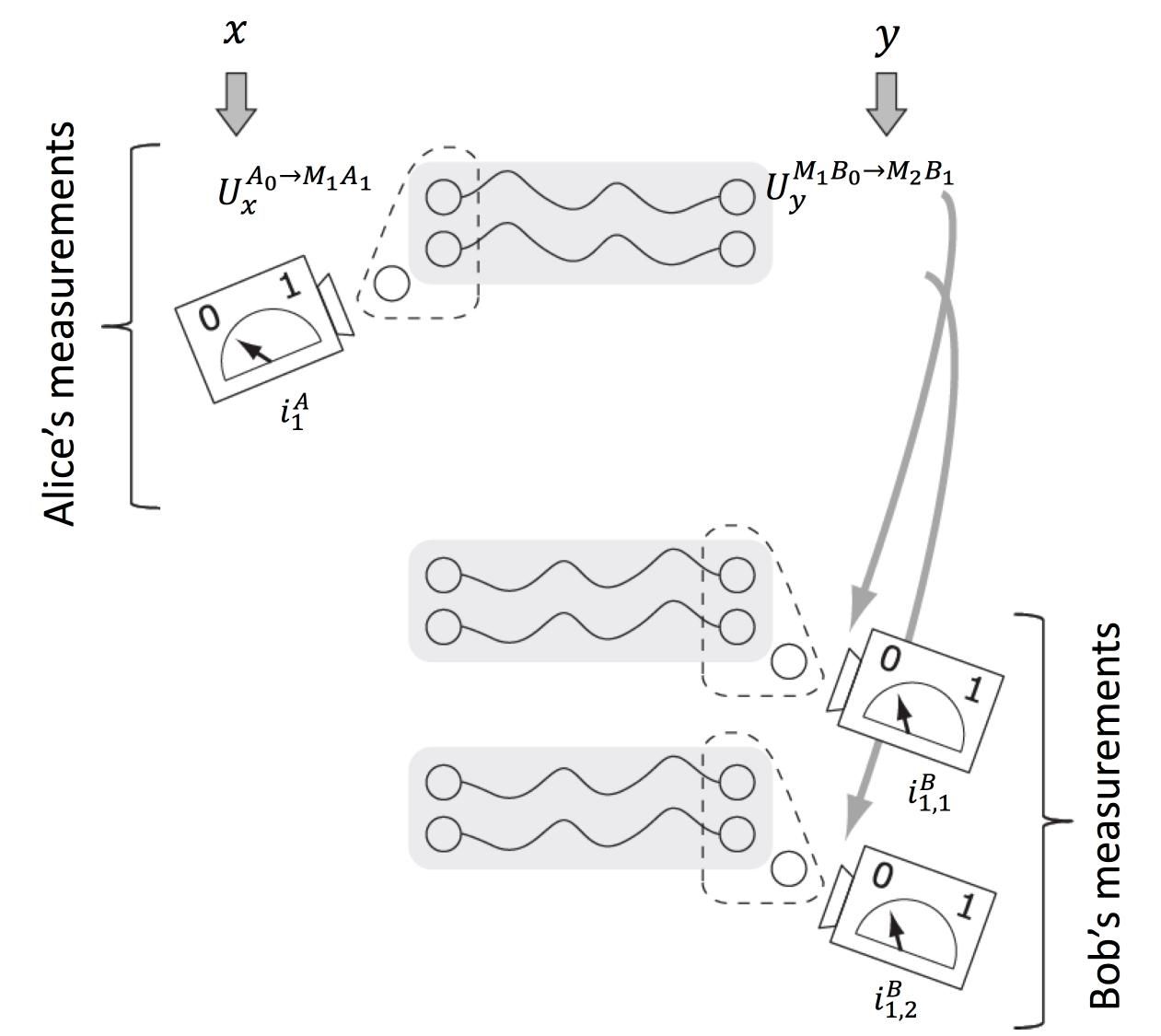
(Phys.org)—The relationship between communication complexity problems, Bell nonlocal correlations and the advantage of quantum over classical strategies has long been recognized, but has been confirmed in only two problems. Recently, however, scientists at University of Cambridge, University of Amsterdam, CWI, QuSoft, Gdansk University, Gdansk University of Technology, Adam Mickiewicz University, and Jagiellonian University employed a two-part method based on port-based teleportation – a scheme of quantum teleportation where a receiver has multiple (N) output ports and obtains the teleported state by merely selecting one of the N ports1,2. The researchers used the quantum protocol based on the given communication complexity game to construct a set of quantum measurements on a maximally entangled state to show that any large advantage over the best known classical strategy makes use of Bell nonlocal correlations. In so doing, the researchers assert, they have provided the missing link to the fundamental equivalence between Bell nonlocality and quantum advantage. Moreover, their results have significant implications for classical information processing and the development of more efficient teleportation protocols.
Dr. Sergii Strelchuk discussed the paper, “Quantum communication complexity advantage implies violation of a Bell inequality,” that he and his colleagues published in Proceedings of the National Academy of Sciences. Two of the challenges the scientists faced were encountered in demonstrating that any large advantage over the best known classical strategy makes use of Bell nonlocal correlations, and in providing the “missing link” (in the form of a general connection) between a large quantum advantage in communication complexity and Bell nonlocality. “One conceptual issue was finding a procedure that converts any quantum strategy for a given communication complexity problem into a set of correlations – that is, probability distributions corresponding to the measurement outcomes during the protocol,” Strelchuk tells Phys.org.
Read more







