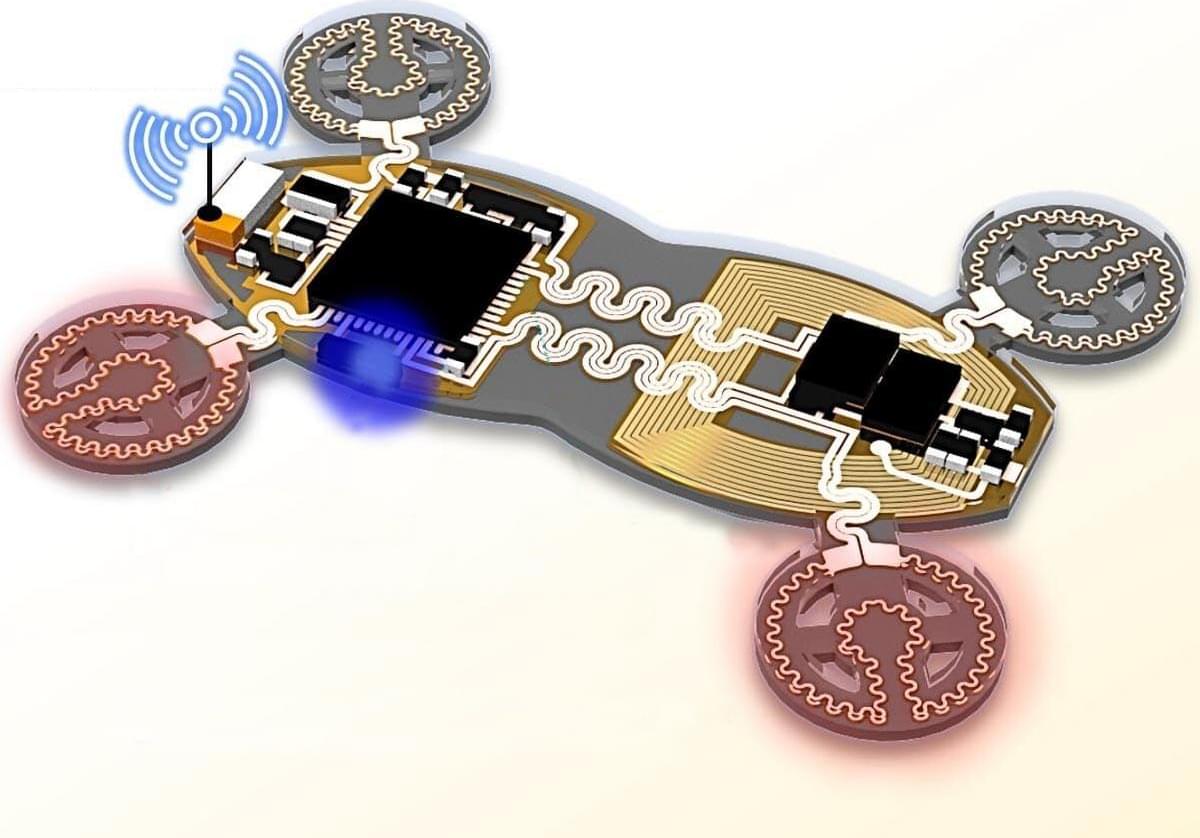
A flexible, semi-autonomous robot could potentially locate disaster victims trapped under rubble and deliver medication within the human body. A small, soft, and flexible robot capable of crawling through earthquake debris to locate trapped victims, or navigating the human body to deliver medicin
A new model has been developed to simulate interstellar activity within our solar system and the nearby Alpha Centauri system. Interstellar material has been found within our solar system, but scientists are still working to determine its origin and how it arrived here. A recent study from Wes
The approach uses lasers and holograms to detect misalignments as small as 0.017 nanometers. Researchers at the University of Massachusetts Amherst have developed a new method for aligning 3D semiconductor chips by shining a laser through concentric metalenses patterned onto the chips, creating a
In a surprising twist, a graduate student at UMass Amherst discovered a strange new fluid behavior that seems to defy thermodynamics.
While experimenting with oil, water, and magnetized nickel particles, he found that no matter how hard the mixture was shaken, it would always return to the same elegant urn shape. This behavior sparked curiosity among physicists, who eventually traced the cause to unusually strong magnetism altering the way the fluids interact. Though it has no immediate use, the finding opens new frontiers in soft-matter science.
A surprising discovery in soft matter.
A surprising link between the immune system and brain behavior is emerging, as new research reveals how a single immune molecule can affect both anxiety and sociability depending on which brain region it acts upon.
Scientists found that IL-17 behaves almost like a brain chemical, influencing neuron activity in ways that alter mood and behavior during illness. These findings suggest the immune system plays a much deeper role in shaping our mental states than previously thought, opening new doors for treating conditions like autism and anxiety through immune-based therapies.
Immune Molecules and Brain Behavior.
Scientists have uncovered the strongest evidence yet for the existence of elusive intermediate-mass black holes (IMBHs), long thought to be the missing link between stellar-mass and supermassive black holes. By tracking a hypervelocity star, J0731+3717, that appears to have been ejected from the
Scientists in Japan have uncovered a surprising twist, literally, in how molecules organize themselves. By introducing tiny leftover fragments from previous assemblies, they discovered a way to flip the direction of helical molecular structures.
Using specific intensities of UV and visible light, they controlled whether these molecules formed left-handed or right-handed spirals, revealing a new method to fine-tune optical and electronic properties. This groundbreaking insight could unlock novel ways to engineer smarter, more responsive materials.
Revealing the power of molecular self-assembly.
Fortinet warns attackers used symlink exploits to retain access post-patch, prompting urgent FortiOS updates and SSL-VPN mitigations.
The threat actor known as Paper Werewolf has been observed exclusively targeting Russian entities with a new implant called PowerModul.
The activity, which took place between July and December 2024, singled out organizations in the mass media, telecommunications, construction, government entities, and energy sectors, Kaspersky said in a new report published Thursday.
Paper Werewolf, also known as GOFFEE, is assessed to have conducted at least seven campaigns since 2022, according to BI.ZONE, with the attacks mainly aimed at government, energy, financial, media, and other organizations.
The clone websites identified by DTI include a carousel of images that, when clicked, download a malicious APK file onto the user’s device. The package file acts as a dropper to install a second embedded APK payload via the DialogInterface. OnClickListener interface that allows for the execution of the SpyNote malware when an item in a dialog box is clicked.
“Upon installation, it aggressively requests numerous intrusive permissions, gaining extensive control over the compromised device,” DTI said.
“This control allows for the theft of sensitive data such as SMS messages, contacts, call logs, location information, and files. SpyNote also boasts significant remote access capabilities, including camera and microphone activation, call manipulation, and arbitrary command execution.”