Using this technique, microrobots could deliver stem cells to hard-to-reach places.
Category: robotics/AI – Page 2,345

Promise in the Gloom? How Bleak Future Scenarios for Employment Might Save the Environment
How might future changes in the structure of business and the nature of work impact the environment?
While governments around the world are wrestling with the potential for massive on-rushing technological disruption of work and the jobs market, few are extending the telescope to explore what the knock-on impacts might be for the planet. Here we explore some dimensions of the issue.
Although replacing humans with robots has a dystopian flavor, what, if any positives are there from successive waves of artificial intelligence (AI) and other exponentially developing technologies displacing jobs ranging from banker to construction worker? Clearly, the number of people working and the implications for commuting, conduct of their role and their resulting income-related domestic lifestyle all have a direct bearing on their consumption of resources and emissions footprint. However, while everyone wants to know the impact of smart automation, the reality is that we are all clueless as to the outcome over the next twenty years, as this fourth industrial revolution has only just started.
There is a dramatic variation in views on the extent to
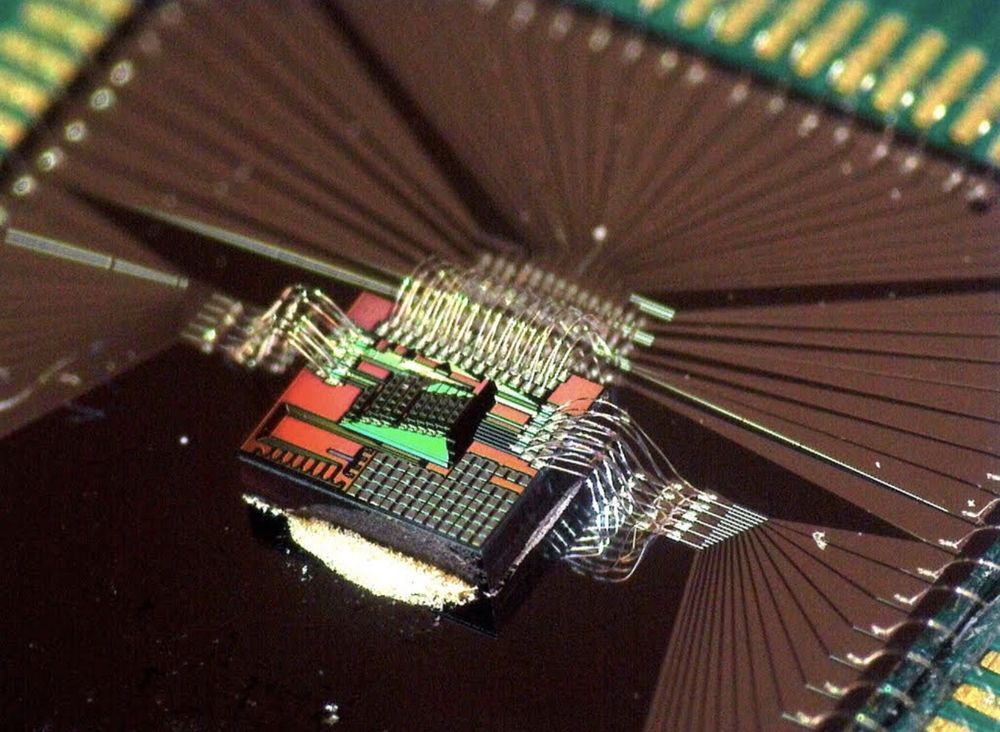
Bill Gates, NEO, Gigafund backing Luminous in photonics supercomputer moonshot
Luminous Computing, a one-year-old startup, is aiming to build a photonics chip that will handle workloads needed for AI at the speed of light. It’s a moonshot and yet, the young company already has a number of high-profile investors willing to bet on the prospect.
The company has raised $9 million in a seed round led by Bill Gates, NEO’s Ali Partovi and Luke Nosek and Steve Oskoui of Gigafund.
The round also attracted other new investors, including Travis Kalanick’s fund 10100, BoxGroup, Uber CEO Dara Khosrowshahi, and Emil Michael as well as pre-seed investors Class 5 Global, Joshua Browder, Ozmen Ventures, Schox Investments and Third Kind Venture Capital.

Pinoy students’ space suit wins gold award at int’l contest in Turkey
A space suit conceptualized and invented by Filipino students bagged the gold award at an international robotics contest in Turkey last week. Current latest trending Philippine headlines on science, technology breakthroughs, hardware devices, geeks, gaming, web/desktop applications, mobile apps, social media buzz and gadget reviews.
This Short Film Is Written Entirely By AI
Viva Space Ship Day
For 10% off your first purchase, go to
http://www.squarespace.com/austinmcconnell
PATREON: http://patreon.com/austinmcconnell
TWITTER: http://twitter.com/austinmcconnell

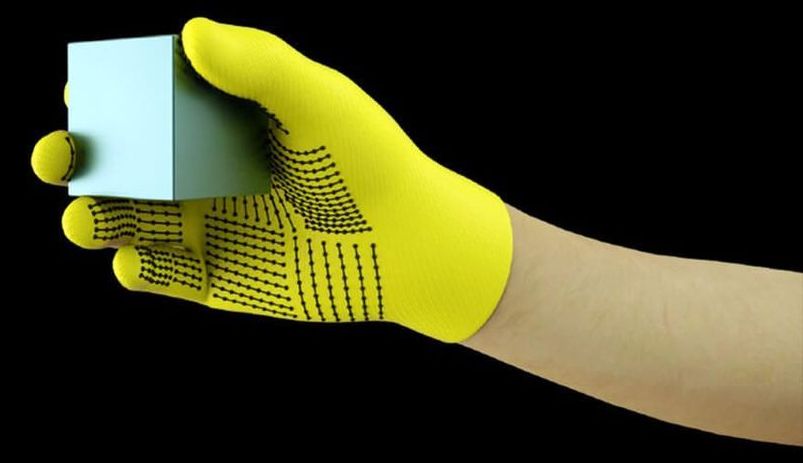
These $10 Sensor-Packed Gloves Could Give Robots a Sense of Touch
Machines are mastering vision and language, but one sense they’re lagging behind on is touch. Now researchers have created a sensor-laden glove for just $10 and recorded the most comprehensive tactile dataset to date, which can be used to train machine learning algorithms to feel the world around them.
Dexterity would be an incredibly useful skill for robots to master, opening up new applications everywhere from hospitals to our homes. And they’ve been coming along in leaps and strides in their ability to manipulate objects, OpenAI’s cube juggling robotic hand being a particularly impressive example.
So far, though, they’ve had one hand tied behind their backs. Most approaches have relied on using either visual data or demonstrations to show machines how they should grasp objects. But if you look at how humans learn to manipulate objects, you realize that’s just one part of the puzzle.
