Sorry, we’re having trouble playing this video.
Learn More.
World Economic Forum.
· —6-h ·
A call to protect the planet 📱
🔎 Learn more about the rise in e-waste.

Sorry, we’re having trouble playing this video.
Learn More.
World Economic Forum.
· —6-h ·
A call to protect the planet 📱
🔎 Learn more about the rise in e-waste.

MediaTek and Qualcomm may be the dominant players in the 5G smartphone SoC sector, but Chinese phone vendors Oppo and Xiaomi are mounting a challenge by developing their own chips. Shortages plaguing the semidoncutor industry are sending firms scrambling for supply. NOR flash chipmakers say that more of their clients are now willing to strike long-term supply contracts. For backend firms, demand from MCU clients remains robust.
Unisoc, Oppo, Xiaomi gearing up for new 5G mobile chips roll-outs: Oppo and Xiaomi will introduce their in-house-developed sub-6GHz 5G chip solutions between late 2021 and early 2022, joining fabless chipmaker Unisoc in competing against chip vendors such as Qualcomm and MediaTek, according to industry sources in Taiwan.
NOR flash chipmakers see more customers eager for long-term deals: Taiwan-based NOR flash chipmakers have seen more of their clients eager to strike long-term supply agreements, according to industry sources.

As they researched why the avalanche occurred with such force, researchers studying climate change pored over images taken in the days and weeks before and saw that ominous cracks had begun to form in the ice and snow. Then, scanning photos of a nearby glacier, they noticed similar crevasses forming, touching off a scramble to warn local authorities that it was also about to come crashing down.
The images of the glaciers came from a constellation of satellites no bigger than a shoebox, in orbit 280 miles up. Operated by San Francisco-based company Planet, the satellites, called Doves, weigh just over 10 pounds each and fly in “flocks” that today include 175 satellites. If one fails, the company replaces it, and as better batteries, solar arrays and cameras become available, the company updates its satellites the way Apple unveils a new iPhone.
The revolution in technology that transformed personal computing, put smart speakers in homes and gave rise to the age of artificial intelligence and machine learning is also transforming space. While rockets and human exploration get most of the attention, a quiet and often overlooked transformation has taken place in the way satellites are manufactured and operated. The result is an explosion of data and imagery from orbit.

Remote-controlled Venus flytrap “robo-plants” and crops that tell farmers when they are hit by disease could become reality after scientists developed a high-tech system for communicating with vegetation.
Researchers in Singapore linked up plants to electrodes capable of monitoring the weak electrical pulses naturally emitted by the greenery.
The scientists used the technology to trigger a Venus flytrap to snap its jaws shut at the push of a button on a smartphone app.

Days after the first malware targeting Apple M1 chips was discovered in the wild, researchers have disclosed yet another previously undetected piece of malicious software that was found in about 30000 Macs running Intel x86_64 and the iPhone maker’s M1 processors.
However, the ultimate goal of the operation remains something of a conundrum, what with the lack of a next-stage or final payload leaving researchers unsure of its distribution timeline and whether the threat is just under active development.
Calling the malware “Silver Sparrow,” cybersecurity firm Red Canary said it identified two different versions of the malware — one compiled only for Intel x86_64 and uploaded to VirusTotal on August 31, 2020 (version 1), and a second variant submitted to the database on January 22 that’s compatible with both Intel x86_64 and M1 ARM64 architectures (version 2).

Huaqiangbei, the world’s largest electronics wholesale market area in the Chinese technology hub of Shenzhen, has become the latest Wonderland for geeks, the way Tokyo’s Akihabara was to otaku during the tech bubble at the turn of the millennium. Amid the warren of closet-sized shops and makeshift stalls, the latest catalogue of smartphones, LED lights, holograms, electronic parts and every type of gadget imaginable compete for attention and the spending yuan of consumers.
Shenzhen has become an international hotspot for the unmanned aerial vehicle industry, following the global success of drone giant DJI.

Google has announced an update to its Developer Program Policy that will help to prevent applications from viewing which other apps are installed on an Android device. The company states that they consider installed apps to be private user information and therefore, aim to protect Android users by keeping this data secure.
That is to say, Google will limit which apps can request the QUERY_ALL_PACKAGES permission, presently mandatory for application targeting API level 30 (Android 11) and above that wish to query the list of application a user has installed for an Android 11 or later device.
From now on, the QUERY_ALL_PACKAGES permission will only be available when the core functionality of an app in question must query any of the device’s installed applications. Therefore, in order to dispute this new policy, developers will have to provide reasonable evidence for how querying the API of an Android devices installed applications is absolutely necessary in order for that device to properly function.

Would you use one in your phone though?
A U.S. startup combined radioactive isotopes from nuclear waste with ultra-slim layers of nanodiamonds to assemble a ridiculous battery that allegedly can last 28000 years.
According to the California startup in question, called NDB (Nano Diamond Battery), their product is a “high-power diamond-based alpha, beta, and neutron voltaic battery.”
The energy comes from waste graphite that was previously used in graphite-cooled nuclear reactors. The radioactive graphite is encased in layers of nano-thin, single crystalline diamond, which act both as a semiconductor and heat sink.
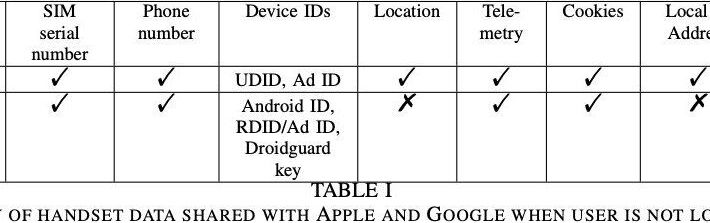
The School of Computer Science and Statistics in Dublin, Ireland, has begun investigating how much user data iOS and Android send to Apple and Google, respectively. Overall, they discovered that, even when the devices are idle or minimally configured, each tends to share an average of 4.5 minutes’ worth of data every day.
For instance, Apple and Google both receive the devices’ IMEI, hardware serial number, SIM serial number and IMSI, handset phone number and other items. Moreover, Android and iOS continue to transmit telemetry to their manufacturing companies, even if the user specifically opts not to share this data. In fact, as soon as the user inserts a SIM card into either device, corresponding user data beacons out to the parent companies of each.
Meanwhile, users have no way to avoid iOS devices sharing with Apple the MAC addresses of nearby devices—such as other handsets or home gateway—as well as GPS location. Indeed, these users do not even have to log in for the device to share their data. On the other hand, Google collects a much larger amount of data from nearby devices than Apple. As a comparison, Google receives about 1MB of data versus 42KB for Apple. While idle, the Android Pixel sends around 1MB every 12 hours, while iOS shares 52KB of data. Furthermore, Google even collects about 20 times more handset data than Apple, and the majority of users in the US have Android devices.
A team from Georgia Tech has just announced a world-first: a 3D-printed rectifying antenna the size of a playing card that can harvest electromagnetic energy from 5G signals and use it to power devices, turning 5G networks into wireless power grids.
Wireless communications put a lot of energy into the air, and over the years we’ve covered a number of efforts to harvest that energy. Short-range Wi-Fi signals have been the target of several projects, TV broadcasts and radio signals have been the focus of others. One device even hopes to increase the life of a smartphone’s battery by 30 percent just by harvesting some of the radio waves the phone itself is generating.
But 5G communications offer a whole new opportunity. 5G has been designed for blazing fast and low-latency communications, reads the Georgia Tech team’s latest study, published in the peer-reviewed journal Scientific Reports. To do so, mm-wave frequencies were adopted and allowed unprecedently high radiated power densities by the FCC. Unknowingly, the architects of 5G have, thereby, created a wireless power grid capable of powering devices at ranges far exceeding the capabilities of any existing technologies.