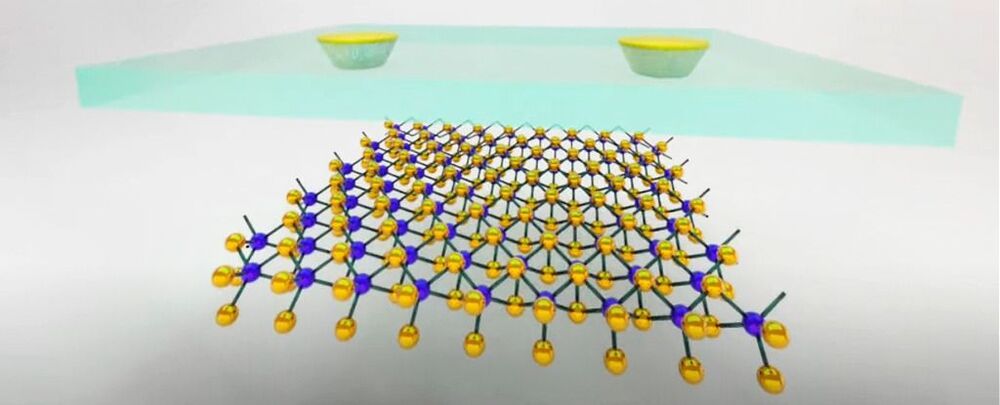
Scientists have succeeded in combining two exciting material types together for the very first time: an ultrathin semiconductor just a single atom thick; and a superconductor, capable of conducting electricity with zero resistance.
Both these materials have unusual and fascinating properties, and by putting them together through a delicate lab fabrication process, the team behind the research is hoping to open up all kinds of new applications in classical and quantum physics.
Semiconductors are key to the electrical gadgets that dominate our lives, from TVs to phones. What makes them so useful as opposed to regular metals is their electrical conductivity can be adjusted by applying a voltage to them (among other methods), making it easy to switch a current flow on and off.