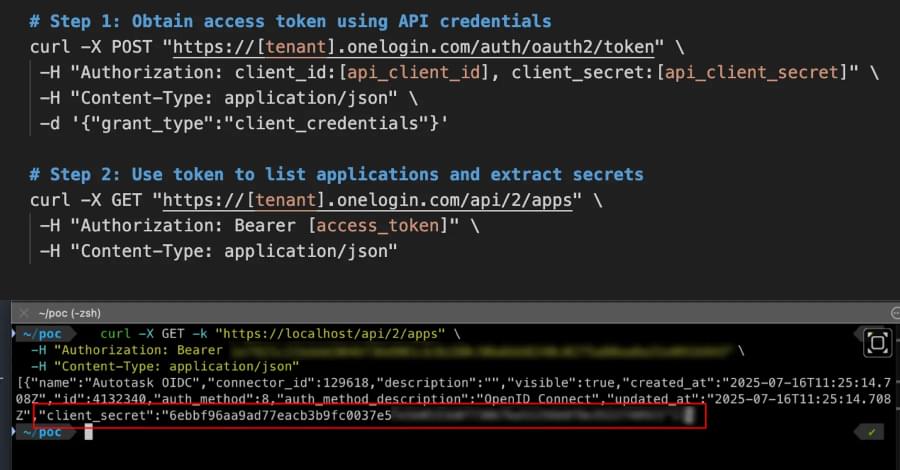
Check Point: Rhadamanthys MaaS stealer (v0.9.2) expands fingerprinting, PNG steganography, and tiered pricing from $299–$499/month.



PC gamers are celebrating games that actually run, and it’s the FPS leading by example.


China has launched CHIEF1300, the world’s largest centrifuge, capable of generating 300 times Earth’s gravity for research.
Scientists have built the first rechargeable hydride ion battery. Hydride ions (H⁻) have drawn interest as potential charge carriers for future electrochemical devices because of their extremely low mass and high redox potential. Yet, progress has been limited since no electrolyte has been able to