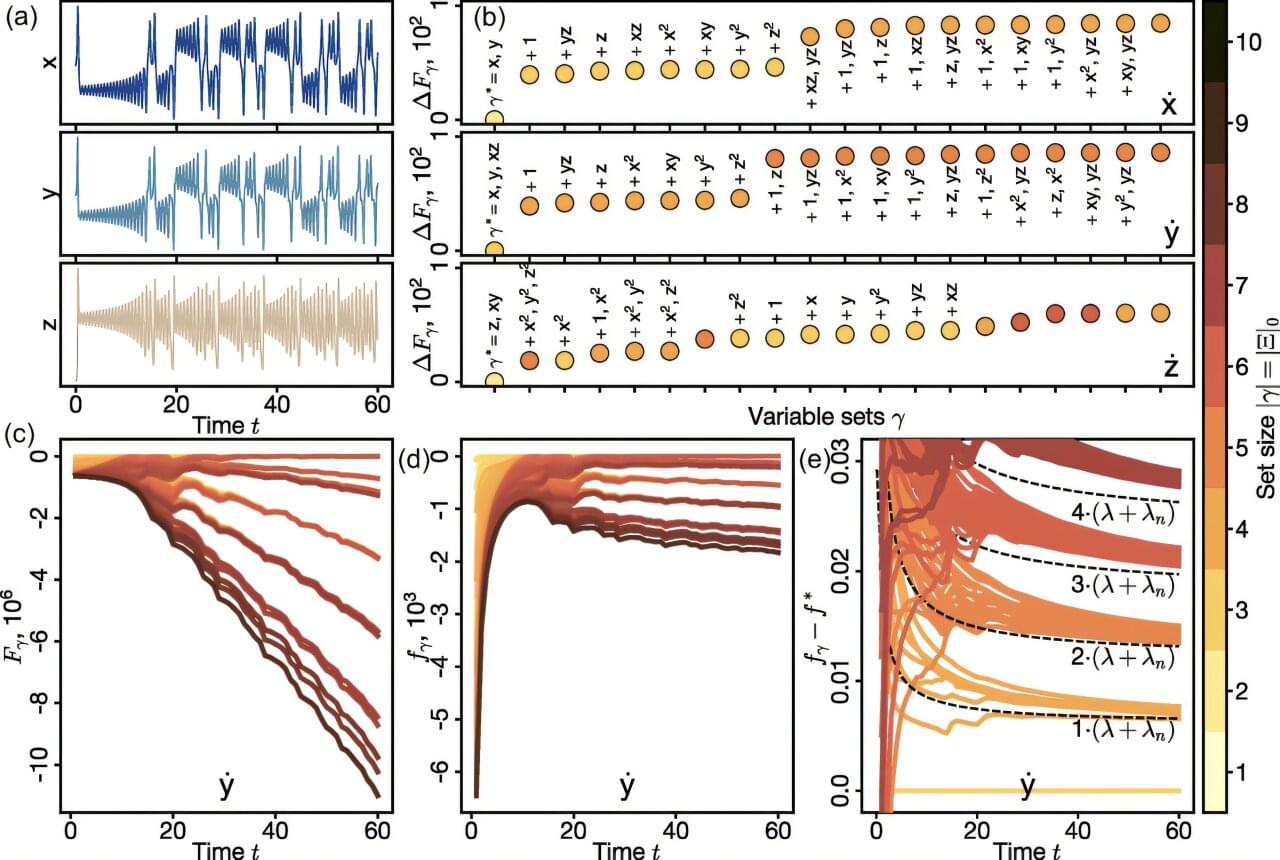
Near-Field Communication (NFC) relay malware has grown massively popular in Eastern Europe, with researchers discovering over 760 malicious Android apps using the technique to steal people’s payment card information in the past few months.
Contrary to the traditional banking trojans that use overlays to steal banking credentials or remote access tools to perform fraudulent transactions, NFC malware abuses Android’s Host Card Emulation (HCE) to emulate or steal contactless credit card and payment data.
They capture EMV fields, respond to APDU commands from a POS terminal with attacker-controlled replies, or forward terminal requests to a remote server, which crafts the proper APDU responses to enable payments at the terminal without the physical cardholder present.