US pair set to return home on Wednesday after Boeing Starliner problems meant eight-day mission lasted nine months.



A new ransomware operator named ‘Mora_001’ is exploiting two Fortinet vulnerabilities to gain unauthorized access to firewall appliances and deploy a custom ransomware strain dubbed SuperBlack.
The two vulnerabilities, both authentication bypasses, are CVE-2024–55591 and CVE-2025–24472, which Fortinet disclosed in January and February, respectively.
When Fortinet first disclosed CVE-2024–55591 on January 14, they confirmed it had been exploited as a zero-day, with Arctic Wolf stating it had been used in attacks since November 2024 to breach FortiGate firewalls.


So far, 20 pipo don share ova $4m in rewards afta dem find $40m of di stolen money and call di crypto companies make dem block di transfer.
But sabi pipo no dey optimistic again say dem go fit recover di rest of di money becos of di North Korean knowledge for hacking and laundering of di money.
Dr Dorit Dor from cyber security company Check Point tok say, “North Korea na veri closed system and closed economy so dem don create successful industry of hacking and laundering and dem no care about di negative impression of cyber crime”


The Dark Storm hacktivist group claims to be behind DDoS attacks causing multiple X worldwide outages on Monday, leading the company to enable DDoS protections from Cloudflare.
While X owner Elon Musk did not specifically state that DDoS attacks were behind the outages, he did confirm that it was caused by a “massive cyberattack.”
“There was (still is) a massive cyberattack against X,” Musk posted on X.
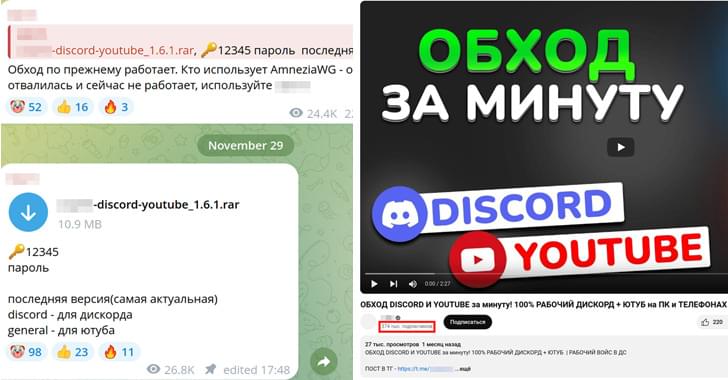
A new mass malware campaign is infecting users with a cryptocurrency miner named SilentCryptoMiner by masquerading it as a tool designed to circumvent internet blocks and restrictions around online services.
Russian cybersecurity company Kaspersky said the activity is part of a larger trend where cybercriminals are increasingly leveraging Windows Packet Divert (WPD) tools to distribute malware under the guise of restriction bypass programs.
“Such software is often distributed in the form of archives with text installation instructions, in which the developers recommend disabling security solutions, citing false positives,” researchers Leonid Bezvershenko, Dmitry Pikush, and Oleg Kupreev said. “This plays into the hands of attackers by allowing them to persist in an unprotected system without the risk of detection.”
