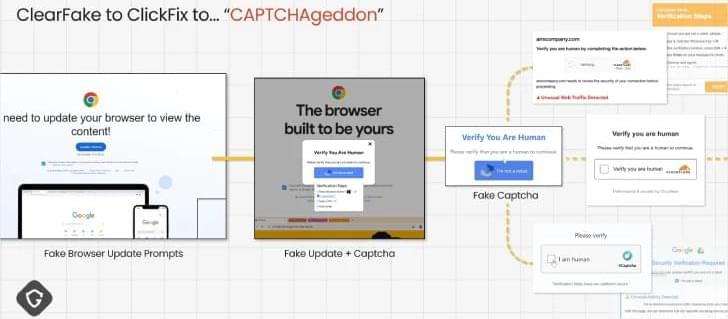
ControlVault3 firmware vulnerabilities impacting over 100 Dell laptop models can allow attackers to bypass Windows login and install malware that persists across system reinstalls.
Dell ControlVault is a hardware-based security solution that stores passwords, biometric data, and security codes within firmware on a dedicated daughterboard, known as the Unified Security Hub (USH).
The five vulnerabilities, reported by Cisco’s Talos security division and dubbed “ReVault,” affect both the ControlVault3 firmware and its Windows application programming interfaces (APIs) across Dell’s business-focused Latitude and Precision laptop series.