Hackers have updated the XCSSET malware to add support for macOS Monterey by updating the source code components to Python 3.


The software that runs John Deere tractors was successfully “jailbroken” at this year’s DEF CON hacker convention, enabling farmers to repair or retune their equipment without engaging with the company that sold them their vehicles.
The hacker involved, who calls himself Sick Codes, was responding directly to U.S. farmers’ long-standing concerns that their “smart” tractors are run on software that only John Deere can access to repair. Smart tractors, including those manufactured by John Deere, are also widely used in the U.K.
Sick Codes’ jailbreak was undertaken to “liberate the tractors,” he said. John Deere responded in a statement to Wired magazine that it works closely with cybersecurity partners and also “embraces the broader ethical hacking community” to ensure its security capabilities remain industry-leading. In March 2022, the manufacturer responded to pressure from farmers with the announcement that it would make more of its software repair tools available to customers and mechanics from next year.

Please see my article published today in Skytop Strategies. Thanks and have a great weekend!
Essential emerging technology: companies are woefully unprepared by chuck brooks.
Link to article:
Chuck Brooks, President of Brooks Consulting International, is a globally recognized thought leader and subject matter expert on Cybersecurity and Emerging Technologies. LinkedIn named Chuck as one of “The Top 5 Tech People to Follow on LinkedIn.” He was named by Thomson Reuters as a “Top 50 Global Influencer in Risk, Compliance,” and by IFSEC as the “#2 Global Cybersecurity Influencer.” He was featured in the 2020 Onalytica “Who’s Who in Cybersecurity” – as one of the top Influencers for cybersecurity issues. He was also named one of the Top 5 Executives to Follow on Cybersecurity by Executive Mosaic. He is also a Cybersecurity Expert for “The Network” at the Washington Post, Visiting Editor at Homeland Security Today, Expert for Executive Mosaic/GovCon, and a Contributor to FORBES. He has also been a featured author in technology and cybersecurity blogs & events by IBM, AT&T, Microsoft, Cylance, Xerox, Malwarebytes, General Dynamics Mission Systems, and many others. He recently presented to the G20 on Energy Cybersecurity.
Chuck is on the Faculty of Georgetown University where he teaches in the Graduate Applied Intelligence and Cybersecurity Risk Programs. In government, Chuck was a “plank holder” at The Department of Homeland Security (DHS) serving as the first Legislative Director of The Science & Technology Directorate at the Department of Homeland Security. He served as a top Advisor to the late Senator Arlen Specter on Capitol Hill covering security and technology issues on Capitol Hill. He has an M.A from the University of Chicago and a B.A. from DePauw University.
The 4th Industrial Era
⭕ Watch the full episode on EpochTV 👉https://ept.ms/Cyberattack_FULL
🔵 SURVEY: Your View on the FBI Raid of Trump👉https://ept.ms/3dsTLUU
🔔 A Documentary by The Epoch Times, reveals the truth that has been hidden from the American people.👉https://ept.ms/3cTR1zF
🔵 Enjoy 50% OFF 👉 https://ept.ms/3OAQfFI
⭕️ Sign up for our NEWSLETTER and stay in touch👉https://www.ntd.com/newsletter.html.
Destroying a nation from within is the goal of the Chinese regime.


We’ve got a cybersecurity problem, but it’s not the one we think we have. The problem is how we think about cybersecurity problems.
Were you unable to attend Transform 2022? Check out all of the summit sessions in our on-demand library now! Watch here.
The problem is not that there are problems. The problem is expecting otherwise and thinking that having problems is a problem.
We’ve got a cybersecurity problem, but it’s not the one we think we have. The problem is in how we think about cybersecurity problems. Too many of us are stuck in a reactive loop, looking for silver bullet solutions, when we need to change how we view cybersecurity problems instead.
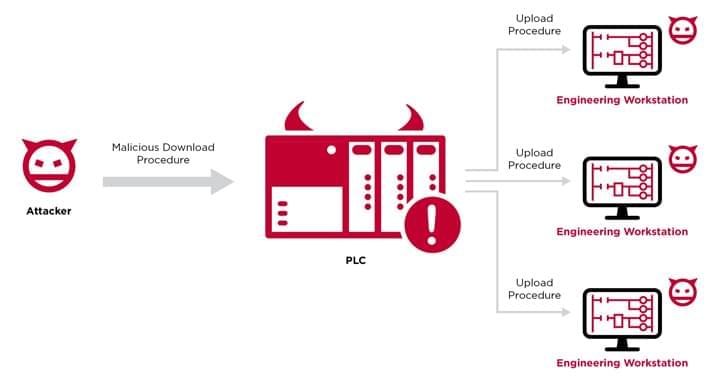
Cybersecurity researchers have elaborated a novel attack technique that weaponizes programmable logic controllers (PLCs) to gain an initial foothold in engineering workstations and subsequently invade the operational technology (OT) networks.
Dubbed “Evil PLC” attack by industrial security firm Claroty, the issue impacts engineering workstation software from Rockwell Automation, Schneider Electric, GE, B&R, Xinje, OVARRO, and Emerson.
Programmable logic controllers are a crucial component of industrial devices that control manufacturing processes in critical infrastructure sectors. PLCs, besides orchestrating the automation tasks, are also configured to start and stop processes and generate alarms.

Wikimedia Commons.
The Elon Musk space company may be popular for ferrying astronauts and cargo missions on its reusable rockets, but its satellite internet services have also made a mark in recent times. When Russia invaded Ukraine earlier this year, it also tried to break the communication chain inside the country by attacking its fiber optic network. However, SpaceX’s terminals were flown in, and connectivity was restored in a matter of days.
It cost a researcher only $25 worth of parts to create a tool that allows custom code to run on the satellite dishes.