Over the past year, SideWinder has been linked to a cyber attack aimed at Pakistan Navy War College (PNWC) as well as an Android malware campaign that leveraged rogue phone cleaner and VPN apps uploaded to the Google Play Store to harvest sensitive information.
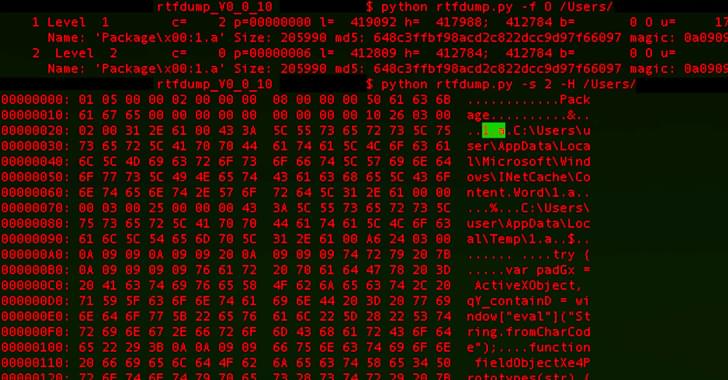
The latest infection chain documented by BlackBerry mirrors findings from Chinese cybersecurity firm QiAnXin in December 2022 detailing the use of PNWC lure documents to drop a lightweight. NET-based backdoor (App.dll) that’s capable of retrieving and executing next-stage malware from a remote server.
What makes the campaign also stand out is the threat actor’s use of server-based polymorphism as a way to potentially sidestep traditional signature-based antivirus (AV) detection and distribute additional payloads by responding with two different versions of an intermediate RTF file.